-
-
Notifications
You must be signed in to change notification settings - Fork 434
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
PRs created don't trigger other actions #48
Comments
|
This is a deliberate limitation imposed by GitHub Actions that an action cannot trigger other workflows. From the documentation:
https://help.github.com/en/articles/events-that-trigger-workflows#example-using-more-than-one-event I'm not sure if there are any work arounds. I guess you would need another event to trigger the additional workflow. |
|
I've found a work around. It looks like GitHub are determining that API calls are coming from actions by checking the authentication token. If you use a Create a Use that secret in your workflow and assign it to the environment variable There is a downside to this method. The PR is no longer created by the |
|
I contacted GitHub about this issue and their response confirms that using a personal token as I outlined above is the correct approach. From GitHub Support:
|
|
Ah what a pain. Resorting to a token that applies to every repository of the user without being able to scope specifically to the desired repository is quite the security concern. (My complaints are to GitHub, not this repo BUT SOMEONE MUST HEAR ME AS I SHOUT POWERLESS INTO THE VOID!! 😅) |
|
Hey all, check it out... another possible workaround is to use an pascalgn/automerge-action#37 (comment) Here's my (sample/testing 😁) configuration: Not as elegant as a direct trigger, but certainly better than having to resort to a Personal Access Token. Thought I'd share. 👍 |
Default Github token does not trigger CI when bot creates a new PR. See <peter-evans/create-pull-request#48> for more details.
|
There is a massive drawback to using this token, if a repository owner uses a personal token they will not be able to request changes nor approve a PR. This is due to the fact that the PR will be created by the owner. |
|
Thanks to @proudust for bringing it to my attention, an alternative to using a PAT is SSH Deploy keys that can be set per repository. See the documentation here for how to use Deploy keys with create-pull-request action. Note that this method will only trigger |
|
Using deploy keys is now even easier because |
|
Sorry if this has been explained - do I understand correctly that if the repository needs to have workflows triggered on |
|
@brockfanning There are actually a number of different workarounds now with various pros and cons. I've summarised them and updated the documentation here. |
|
I was able to trigger actions, using Fine-grained personal access token (BETA) , with those permissions: Didn't test if this is minimal set of permissions, probably can be limited even more: |
|
Peter, thanks for writing up an explanation of this issue and the workarounds, even though it's not really your responsibility. Fwiw, this is my situation. I maintain a website template where I try to automate as much as possible for the (often low-technical-knowledge) user. As such, I can't ask the user to create personal access tokens and things like that. So asking them to close/reopen by clicking a big red/green button is the best and most elegant workaround. I'm also making use of the |
|
@vincerubinetti I can understand how that might be the best option for non-technical users. There's a similar approach that @bmacher commented here, that also might work for you.
|
As discussed here, workflows cannot be triggered for PRs created by bot accounts. peter-evans/create-pull-request#48 There are workarounds, but they involve more work than they're worth. For now, let's assume that these auto-version- branches don't need to be linted. They only make a single change to package.json, anyway.
As discussed here, workflows cannot be triggered for PRs created by bot accounts. peter-evans/create-pull-request#48 There are workarounds, but they involve more work than they're worth. For now, let's assume that these auto-version- branches don't need to be linted. They only make a single change to package.json, anyway.
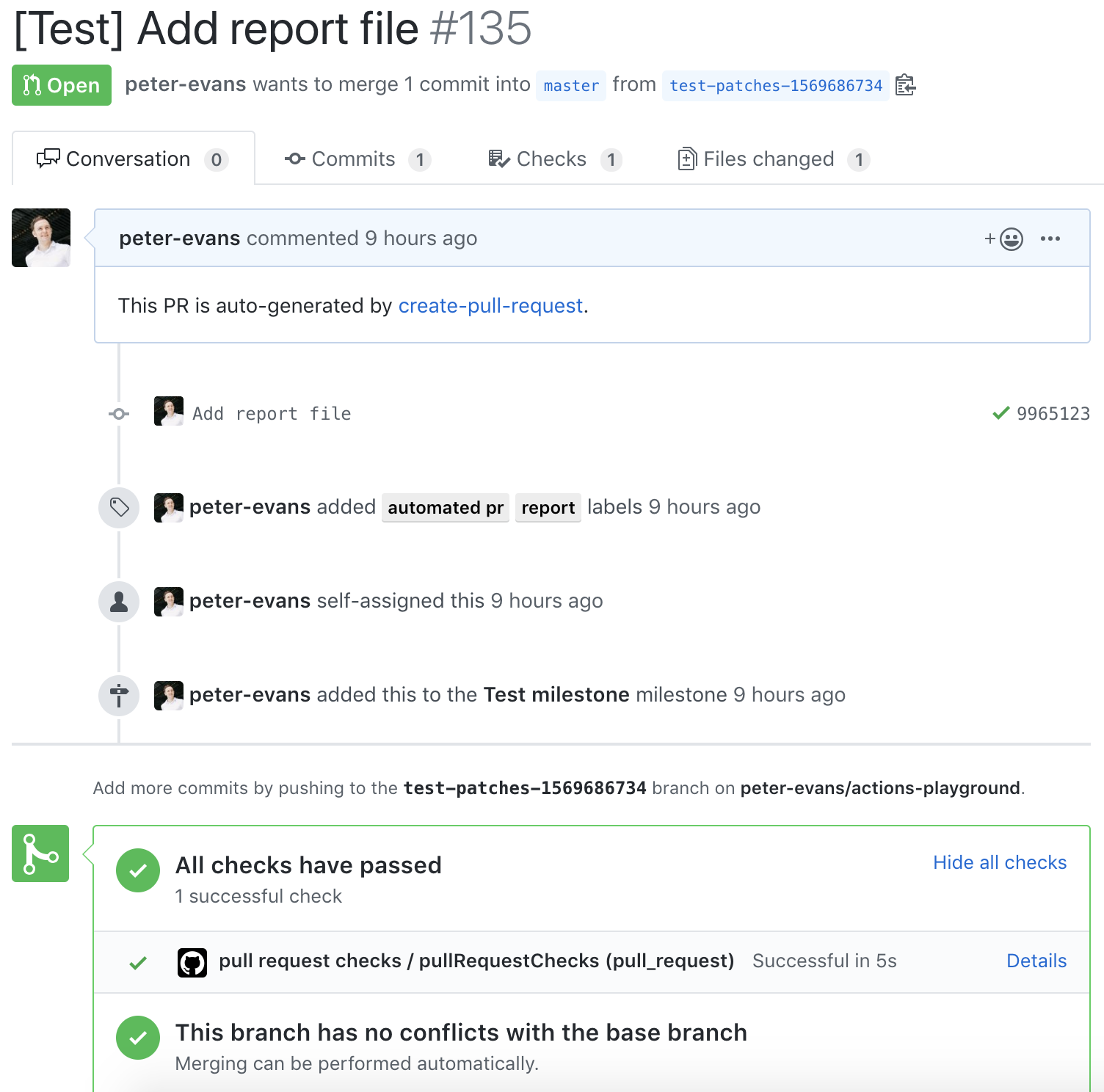
It seems that any PRs that get created by this action will not trigger any actions waiting on a pull request event, which means that you can have any required status checks.
Any ideas for how to get around this?
The text was updated successfully, but these errors were encountered: