-
Notifications
You must be signed in to change notification settings - Fork 8.3k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[Serverless][Security Solution][Endpoint] Restrict endpoint exceptions on serverless via plugin sub-features #164107
[Serverless][Security Solution][Endpoint] Restrict endpoint exceptions on serverless via plugin sub-features #164107
Conversation
…features_configs_to_plugins
…features_configs_to_plugins # Conflicts: # x-pack/plugins/security_solution/public/rules/links.ts # x-pack/plugins/security_solution/tsconfig.json # x-pack/plugins/security_solution_serverless/server/plugin.ts # x-pack/plugins/security_solution_serverless/tsconfig.json
…ith-plugin-sub-features
…sub-features' of github.com:ashokaditya/kibana into task/dw-serverless-endpoint-exceptions-pli-with-plugin-sub-features
…endpoint-exceptions-pli-with-plugin-sub-features
…ith-plugin-sub-features
…ith-plugin-sub-features
…endpoint-exceptions-pli-with-plugin-sub-features
fae0330 to
4119d61
Compare
…ith-plugin-sub-features
…ith-plugin-sub-features
💔 Build FailedFailed CI StepsTest Failures
Metrics [docs]Module Count
Public APIs missing comments
Any counts in public APIs
Async chunks
Public APIs missing exports
Page load bundle
Unknown metric groupsAPI count
History
To update your PR or re-run it, just comment with: cc @ashokaditya |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@ashokaditya Great work integrating the features package.
Thank you!! 💯
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
ResponseOps changes LGTM
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
LGTM
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
A lot of work here, thanks! Left two questions but other than that, this looks good!
| if (!canWriteEndpointExceptions) { | ||
| return { | ||
| exceptionActionItems: exceptionActionItems.map((item) => { | ||
| return { ...item, disabled: item.name === ACTION_ADD_ENDPOINT_EXCEPTION }; |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Do we show any tooltip or callout when this is disabled? I wonder if having this disabled with no messaging could generate some confusion for users.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Good call @dasansol92. So currently without this change, we do show the Add endpoint exception menu item but it is disabled if it is a non-endpoint alert or the user doesn't have the right privilege (on index). We don't show a tooltip though.
This change is disabling the menu item based on available product-line items, so maybe we should show a tooltip to distinguish from the above case. (On the serverless side, however, the user without an endpoint PLI won't see any endpoint alerts, so this is the only time they see a disabled menu item). Thoughts @kevinlog @caitlinbetz?
| createExceptionList(getExceptionList1(), getExceptionList1().list_id).as( | ||
| 'exceptionListResponse' | ||
| ); | ||
| createExceptionList(getExceptionList1(), getExceptionList1().list_id); |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Why is this (an the other one below) change required?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@dasansol92 Looks like the network requests were not actually waited on, anywhere in the test suites. Might have been leftover/redundant code from /pull/152757
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
LGTM! Great work!
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Detection Engine code area LGTM
| * 2.0. | ||
| */ | ||
| /* | ||
| * Copyright Elasticsearch B.V. and/or licensed to Elasticsearch B.V. under one |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
nit: license message duplicated
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@vitaliidm I am writing the README of the package in a separate PR, I'll clean this in there. Thanks!
… rule details and API changes (#165613) ## What this PR changes Follow up of /pull/164107/ For serverless ES/Kibana, it gates exception list API for endpoint exceptions and restricts endpoint exceptions tab on Endpoint Security rule details based on project PLIs. If no endpoint PLIs, endpoint exceptions should not be accessible. - [x] Add upselling to `app/security/exceptions/details/endpoint_list` page - [ ] Tests (WIP) - in a follow up PR ### How to review Best to follow along commits for a code review. Below are details to manually test the changes. - Setup for _Servlerless_ - Run `yarn es serverless --kill --clean --license trial -E xpack.security.authc.api_key.enabled=true` on a terminal window to start ES. - Copy `config/serverless.security.yml` to `config/serverless.security.dev.yml` - Run `yarn serverless-security --no-base-path` on another terminal window to start kibana in serverless mode - Log in using `serverless_security` user. ### Tests (Serverless) This needs to be tested with a custom user/role and not `elastic_serverless` which has `superuser` role. 1. ### PLI configs `{ product_line: 'security', product_tier: 'essentials' }` or `{ product_line: 'security', product_tier: 'complete' }` and `{ product_line: 'endpoint', product_tier: 'essentials' }` or `{ product_line: 'endpoint', product_tier: 'complete' }` - #### UX 1. Navigate to Rules via `http://localhost:5601/app/security/rules/`. Click on `Add Elastic rules`. 2. Select and add `Endpoint Security` rule. 3. Click `Endpoint Security` and navigate to the rules details page, and you should see `Endpoint exceptions` tab. The tabs visible are `Alerts`, `Endpoint exceptions`, `Rule exceptions`, `Execution results`. 4. Navigate to Rules>Shared Exception Lists > Endpoint Security Exception List via `app/security/exceptions/details/endpoint_list` and you should be able to see the page with any added endpoint exceptions. - #### API requests (with user `serverless_security`) 1. should get a status `200` on`POST api/exception_lists/items` 2. should get a status `200` on `POST api/exception_lists/_export?id=endpoint_list&list_id=endpoint_list&namespace_type=agnostic&include_expired_exceptions=true` 3. should get a status `200` on `PUT api/exception_lists/items` 5. should get a status `200` on `DELETE api/exception_lists/items` 6. should get a status `200` on `GET api/exception_lists/items/_find?list_id=endpoint_list&namespace_type=agnostic` 2. ### PLI configs `{ product_line: 'security', product_tier: 'essentials' }` or `{ product_line: 'security', product_tier: 'complete' }` - #### UX 1. Navigate to Rules via `http://localhost:5601/app/security/rules/`. Click on `Add Elastic rules`. 2. Select and add `Endpoint Security` rule. 3. Click `Endpoint Security` and navigate to the rules details page, and you should not see `Endpoint exceptions` tab. The only tabs visible are `Alerts`, `Rule exceptions`, `Execution results`.  4. Navigate to Rules>Shared Exception Lists > Endpoint Security Exception List via `app/security/exceptions/details/endpoint_list` and you should see an upsell message. 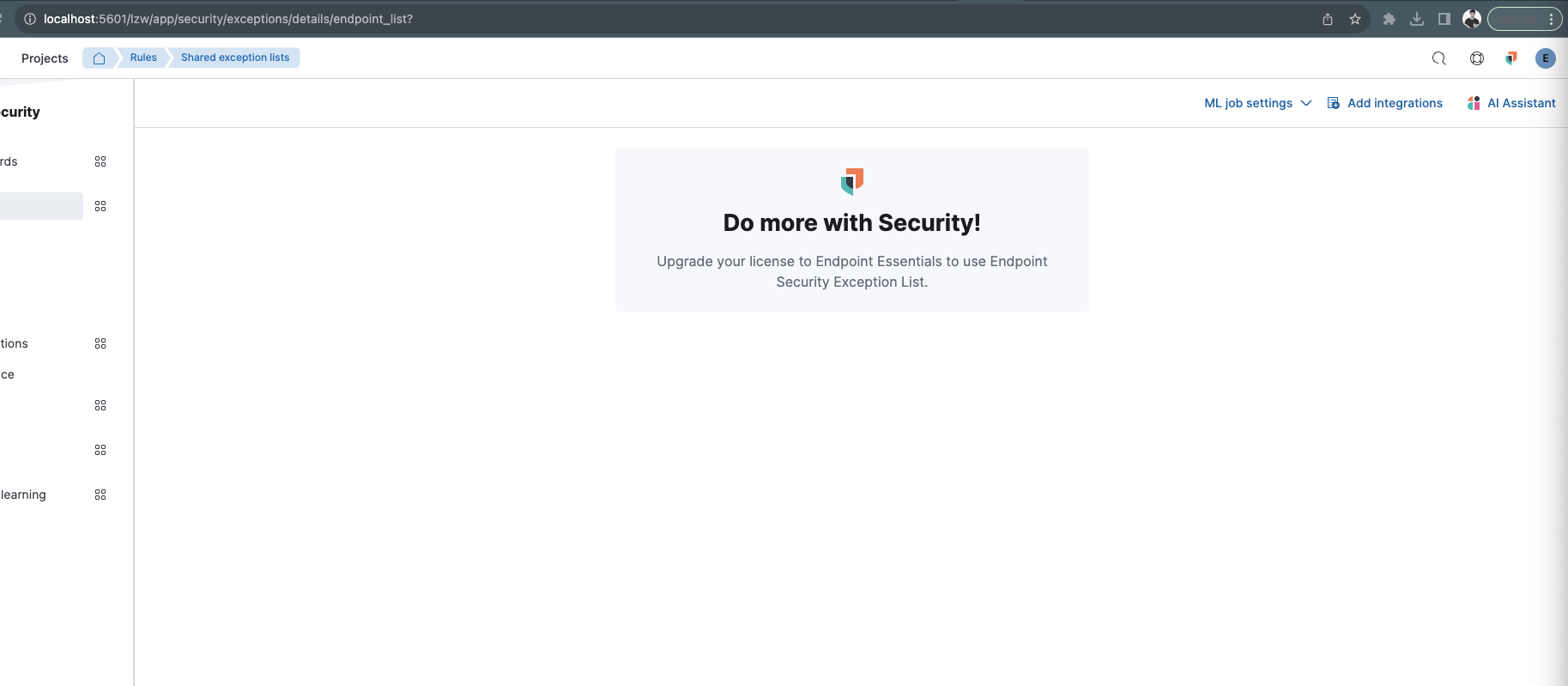 - #### API requests 1. should get a status `403` on`POST api/exception_lists/items` 2. should get a status `403` on `POST api/exception_lists/_export?id=endpoint_list&list_id=endpoint_list&namespace_type=agnostic&include_expired_exceptions=true` 3. should get a status `403` on `PUT api/exception_lists/items` 6. should get a status `403` on `DELETE api/exception_lists/items` 7. should get a status `403` on `GET api/exception_lists/items/_find?list_id=endpoint_list&namespace_type=agnostic` --- **Flaky FTRs** https://buildkite.com/elastic/kibana-flaky-test-suite-runner/builds/3248 https://buildkite.com/elastic/kibana-flaky-test-suite-runner/builds/3255 ### Checklist - [x] Any text added follows [EUI's writing guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses sentence case text and includes [i18n support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md) - [x] [Unit or functional tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html) were updated or added to match the most common scenarios - [x] Any UI touched in this PR does not create any new axe failures (run axe in browser: [FF](https://addons.mozilla.org/en-US/firefox/addon/axe-devtools/), [Chrome](https://chrome.google.com/webstore/detail/axe-web-accessibility-tes/lhdoppojpmngadmnindnejefpokejbdd?hl=en-US)) - [ ] If a plugin configuration key changed, check if it needs to be allowlisted in the cloud and added to the [docker list](https://github.com/elastic/kibana/blob/main/src/dev/build/tasks/os_packages/docker_generator/resources/base/bin/kibana-docker) - [ ] This renders correctly on smaller devices using a responsive layout. (You can test this [in your browser](https://www.browserstack.com/guide/responsive-testing-on-local-server)) - [ ] This was checked for [cross-browser compatibility](https://www.elastic.co/support/matrix#matrix_browsers) ### Risk Matrix Delete this section if it is not applicable to this PR. Before closing this PR, invite QA, stakeholders, and other developers to identify risks that should be tested prior to the change/feature release. When forming the risk matrix, consider some of the following examples and how they may potentially impact the change: | Risk | Probability | Severity | Mitigation/Notes | |---------------------------|-------------|----------|-------------------------| | Multiple Spaces—unexpected behavior in non-default Kibana Space. | Low | High | Integration tests will verify that all features are still supported in non-default Kibana Space and when user switches between spaces. | | Multiple nodes—Elasticsearch polling might have race conditions when multiple Kibana nodes are polling for the same tasks. | High | Low | Tasks are idempotent, so executing them multiple times will not result in logical error, but will degrade performance. To test for this case we add plenty of unit tests around this logic and document manual testing procedure. | | Code should gracefully handle cases when feature X or plugin Y are disabled. | Medium | High | Unit tests will verify that any feature flag or plugin combination still results in our service operational. | | [See more potential risk examples](https://github.com/elastic/kibana/blob/main/RISK_MATRIX.mdx) | ### For maintainers - [ ] This was checked for breaking API changes and was [labeled appropriately](https://www.elastic.co/guide/en/kibana/master/contributing.html#kibana-release-notes-process) --------- Co-authored-by: kibanamachine <[email protected]>
What this PR changes
branched from /pull/163759
@kbn/security-solution-featureswith the common logic andAppFeatureServiceto apply offering specific configurations for Security Solution features independently for Serverless and ESS. This logic is replacing the earlierAppFeaturesin order to introduce new Kibana feature privileges for serverless PLIs so that new Kibana privileges introduced for serverless PLIs do not affect/show up as new Kibana feature privileges in ESS.Endpoint exceptionsshould be accessible/seen only on endpoint essentials/complete.New AppFeatures logic architecture diagram:
Note: Corresponding API changes related to endpoint exceptions will be in a new PR, along with the last set of UX changes for hiding the
Endpoint exceptionstab from the Rules details page.How to review
yarn es snapshoton a terminal window to start ES.config/serverless.security.ymltoconfig/serverless.security.dev.ymlyarn serverless-security --no-base-pathon another terminal window to start kibana in serverless modenode x-pack/plugins/security_solution/scripts/endpoint/endpoint_agent_emulator.js --asSuperuseron a new window and then select1toLoad Endointsand then1toRunthe loader script. This will load some fake agents/alerts data to test with.Tests (Serverless)
{ product_line: 'security', product_tier: 'essentials' }or{ product_line: 'security', product_tier: 'complete' }and
{ product_line: 'endpoint', product_tier: 'essentials' }or{ product_line: 'endpoint', product_tier: 'complete' }http://localhost:5601/app/security/exceptionsEndpoint Security Exception Listcard on the shared exception lists page.Alertspage viaapp/security/alerts, you should see endpoint alerts. If not, then click onManage Rulesand then disable/enableEndpoint Securityrules. That should trigger alerts to show up on the Alerts table.View Detailsbutton underActionscolumn. Once the flyout is visible, click onTake Actionand verify thatAdd Endpoint exceptionis visible/enabled/clickable on the menu.More actionsbutton underActionscolumn and verify thatAdd Endpoint exceptionis visible/enabled/clickable on the menu.Investigate in timelinebutton underActionscolumn; when the timeline view is visible and the alert item is displayed, click on buttons mentioned in 4. and 5. above and verify the same.Rules>DetectionRules>Endpoint Securityrule under theRulestable. Select theAlertstab.View details,More actionsandInvestigate in timelinebuttons same as in 4., 5., 6. above.Endpoint exceptionstab as well. Click and verify that you can see the tab's content.{ product_line: 'security', product_tier: 'essentials' }or{ product_line: 'security', product_tier: 'complete' }config/serverless.security.dev.ymlso thatendpointproduct line item is commented out.Endpoint Security Exception Listcard on the shared exception lists page.Tests (ESS)
On the ESS side, endpoint exceptions are not affected by this change and work as usual based on index privileges.