-
Notifications
You must be signed in to change notification settings - Fork 8.3k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[Security Solution] Introduce an endpoint to use for the detection rules table filters/data #137428
Comments
|
Pinging @elastic/security-detections-response (Team:Detections and Resp) |
|
Pinging @elastic/security-solution (Team: SecuritySolution) |
…146826) **Addresses:** #137428 ## Summary Adds a new internal lightweight endpoint to fetch rules related information like the number of installed prebuilt rules, the number of custom rules and etc. ## Details This PR adds a quite simple and lightweight endpoint for fetching rules related information which is - the number of installed prebuilt rules - the number of custom rules - tags UI has been updated accordingly. The result of the endpoint are mostly used in the rules table filter but not limited to. **_The added endpoint doesn't implement full aggregation for fetching rule numbers so it's planned to be done in the following PR._** ### Comparison The following screenshots from the browser's network tab demonstrate that the new endpoint is faster which is good since it's intended to be updated executed relatively often whenever the rules are updated. Prebuilt rules endpoint which was used for fetching rules related information <img width="942" alt="Screenshot 2022-12-04 at 21 50 50" src="https://user-images.githubusercontent.com/3775283/205514981-ce51dd4e-faed-4999-b770-5737e0c118d4.png"> The new endpoint 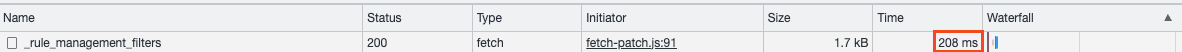 ### Checklist - [x] Any text added follows [EUI's writing guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses sentence case text and includes [i18n support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md) - [x] [Unit or functional tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html) were updated or added to match the most common scenarios
|
Once #125659 is addressed we will need to get back to the filters endpoint and optimize its performance by using aggregation queries. |
|
Aggregations are already used for fetching aggregated rule tags. What we can do is to use aggs for fetching the rest of the data needed for filters. We can do it as part of a separate ticket: #166364 |
Epic: https://github.com/elastic/security-team/issues/1974 (internal)
Summary
Currently we use the
detection_engine/rules/prepackages/_statusendpoint to populate theElastic rulesandCustom rulescounters on the rules management page:We re-fetch those counters once in 5 minutes and on every rule state mutation. However, the
detection_engine/rules/prepackages/_statuswas designed for different purposes. Using it for re-fetching the rules table counters is computationally expensive and will become even more expensive with advances in rule customization epic.We need to extract the logic that calculates the number of custom and prebuilt rules to a separate endpoint and use it to populate the rules table values. Consider introducing an endpoint that returns all data required for the table filters: the number of custom and prebuilt rules, rule tags, etc.
The text was updated successfully, but these errors were encountered: