-
-
Notifications
You must be signed in to change notification settings - Fork 0
Firewall configuration
The configuration of External Dynamic Lists (EDLs) on firewalls requires security engineers to possess the necessary knowledge. This section provides a concise overview of the essential steps to enable the functionality of EDLs with FWAdmin. For comprehensive instructions, it is recommended to refer to the vendor's documentation.
The configuration process involves the following steps:
- Create a dedicated role for API requests.
- Establish a specific user account exclusively for FWAdmin.
- Generate the token associated with the firewall user.
- Define the required EDL objects for the desired scenarios.
- Configure the necessary policies for the intended scenarios.
- Thoroughly test and validate the functionality of the EDLs.
Please note that when working with production firewalls, it is crucial to utilize HTTPS for reading EDLs. However, during testing, HTTP can be used for experimental purposes only.
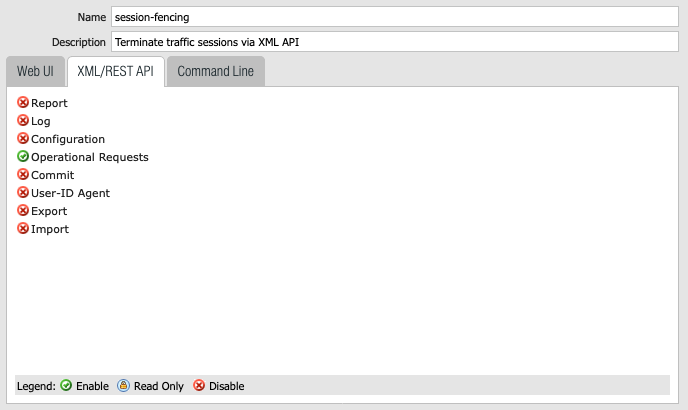
Go to Device -> Admin Roles and add a new role:
- Name:
session-fencing. - Description:
Terminate traffic sessions via XML API. - Web UI: disable everything.
- XML/REST API: enable
Operational Requestsonly. - Command Line:
None.
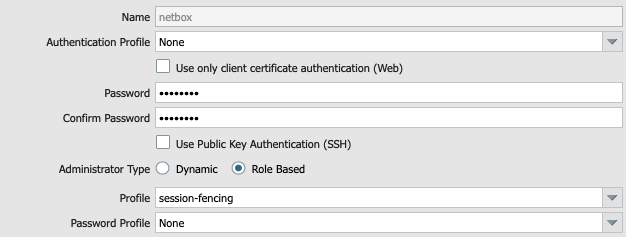
Go to Device -> Administrators and add a new administrator:
- Name:
netbox. - Authentication Profile:
None. - Password: type your password.
- Confirm Password: retype your password.
- Administration Type:
Role Based. - Profile:
session-fencing.
Optionally, configure your password profile as desired.
Open the following URL replacing:
- FWIP: your firewall IP address.
- USERNAME: the user created above (
netbox). - PASSWORD: the user's password.
https://FWIP/api/?type=keygen&user=USERNAME&password=PASSWORD
Retrieve and securely store the token provided in the XML response:
<response status="success">
<result>
<key>
LUFRPT1rUnZlM3lHeXhSRzI4MGNVY0ZCK3NxMUtRbkU9YkFRQjV1Sm9BK0tGeTA5QXNqL29ka0NOTFZIYjdadERicDkxOWhUeFNRcEtHOFFQSUtydFl5UGk5VW9SYmlCdA==
</key>
</result>
</response>
Go to Objects -> External Dynamic Lists and add the required EDLs:
- Source: type a temporary URL, you will update when FWAdmin is configured.
- Check for update:
Five Minute.
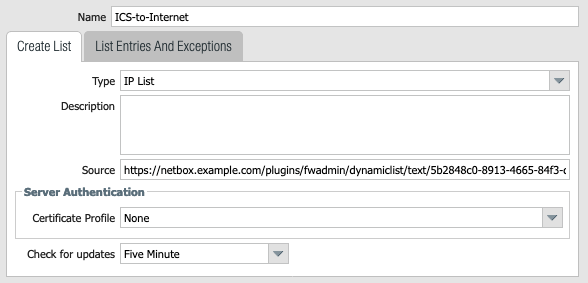
Optionally, set your certificate profile. If you intend to modify the check update interval, it is necessary to update the FWAdmin configuration accordingly.
Go to Policies -> Security and add the required policies:
- reference your EDL in source or destination, according to your scenario.
- set application, service, URL category as needed.
- Action:
Allow.
Force EDL update:
admin@PA-VM> request system external-list refresh type ip name ICS-to-Internet
EDL refresh job enqueued
Check enqueued job:
admin@PA-VM> show jobs all
Enqueued Dequeued ID PositionInQ Type Status Result Completed
------------------------------------------------------------------------------------------------------------------------------------------
2023/05/19 03:29:48 03:29:48 33 EDLRefresh FIN OK 03:29:57
Display the EDL content:
admin@PA-VM> request system external-list show type ip name ICS-to-Internet
ICS-to-Internet
Total valid entries : 1
Total ignored entries : 0
Total invalid entries : 0
Total displayed entries : 1
Valid ips:
192.168.192.25/32
Display active sessions allowed by the EDL:
admin@PA-VM> show session all filter rule ICS-to-Internet
--------------------------------------------------------------------------------
ID Application State Type Flag Src[Sport]/Zone/Proto (translated IP[Port])
Vsys Dst[Dport]/Zone (translated IP[Port])
--------------------------------------------------------------------------------
323 ssh ACTIVE FLOW 192.168.193.25[39686]/Server/6 (192.168.193.25[39686])
vsys1 192.168.192.25[22]/DMZ (192.168.192.25[22])
Terminate sessions allowed by the EDL:
admin@PA-VM> clear session all filter rule ICS-to-Internet
sessions cleared
Terminate sessions allowed by the EDL via Python:
import request
FW = "fw.example.com
TOKEN = "firewalltoken"
EDL = "ICS-to-Internet"
URL = f"https://{FW}/api/?type=op&cmd=<clear><session><all><filter><rule>{EDL}</rule></filter></all></session></clear>&key={TOKEN}"
r = requests.get(url, verify=False)
print(r.status_code)
print(r.text)