-
-
Notifications
You must be signed in to change notification settings - Fork 0
Home
FWAdmin is a NetBox plugin designed to manage time-based remote access to equipment. It has been developed based on the requirements of several customers I have interacted with in recent years.
FWAdmin implements External Dynamic Lists (EDL), which are dynamically populated based on a straightforward workflow involving datetime and user requests.
- Introduction
- Firewall configuration
- NetBox with FWAdmin installation
- Utilizing FWAdmin
- Developing FWAdmin
The primary use case involves remote access to industrial equipment. Field ICS/OT equipment is critical due to the sensitive data (intellectual property) it carries. OT managers are concerned about who can connect to ICS/OT equipment, when they can connect, and for what purpose. Additionally, many field equipment implement an always-on VPN, allowing suppliers to connect to customer equipment without prior notification. Manual editing of firewall policies is not a feasible option due to the potential for human errors and the need for responsiveness (maintenance windows can be unplanned and often occur during the night).
In the first use case (scenario A), the ICS equipment implements an always-on VPN based on the SSH protocol:
The ICS gateway, provisioned by the supplier along with the plant, establishes an always-on VPN, enabling the supplier's technical team to monitor and respond to failures or anomalies. The ICS gateway also supports telemetry. The organization is usually unaware of this arrangement and is generally unwilling to allow unmonitored and unrestricted access to the plant equipment. To terminate the VPN, we need to isolate the ICS gateway and enable it only when maintenance is required.
In the second use case (scenario B), the ICS equipment is accessed via a conventional Site-to-Site IPSec VPN:
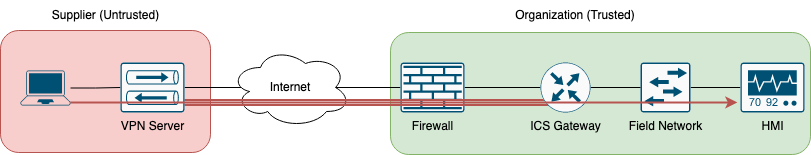
The IPSec VPN is established between the supplier and the organization, but there is no monitoring of who, when, and why someone is connecting to the plant equipment. To terminate the connection, we need to activate traffic only when maintenance is required.

Both scenarios are similar, but the direction of traffic is different:
- In scenario A, we are managing organization-to-supplier traffic.
- In scenario B, we are managing supplier-to-organization traffic.
We cannot terminate user sessions in scenario A because they are hidden (encrypted) within the SSH tunnel.
While OT managers are concerned about intellectual property, we must not overlook the cyber risks. In scenarios like these, supply-chain attacks are highly likely, and I have personally witnessed a couple of supply-chain attacks targeting IoT devices.
FWAdmin is based on NetBox, providing access to all NetBox features. The following NetBox features may be of interest in the context of FWAdmin:
- User roles.
- LDAP/Active Directory integration.
- API.
FWAdmin features include:
- IPv4 EDLs based on groups of NetBox devices.
- EDLs are populated with NetBox device IP addresses based on user requests.
- User requests can be approved by an administrator or self-approved.
- Active traffic sessions are terminated by invoking firewall APIs.
- Support is provided for multiple firewalls.
The upcoming FWAdmin releases will bring about significant changes to the way security engineers currently administer firewall policies. The objective is to incorporate DevOps methodologies into firewall administration.
Currently, only Palo Alto Networks NG firewalls are supported. Others can be added if they meet the following requirements:
- Support IP address EDLs.
- Provide a CLI/API method for terminating active sessions.
To use FWAdmin, you need:
- A supported firewall properly configured.
- A NetBox installation with the FWAdmin plugin.
- Proper configuration of FWAdmin.
The following chapters explain the steps mentioned above.
If you require assistance, please open an issue on GitHub and consider sponsoring the project.