-
Notifications
You must be signed in to change notification settings - Fork 4.2k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
If WordPress user session expires on post edit page, Gutenberg autosave continues resulting in 403s #13509
Comments
|
+1 I would expect the behavior of the editor to stop making failing POSTs to the site and instead give me the option to reconnect. |
|
Users get blacklisted from their hosting provider servers when tabs get left open and sessions expire, thus driving contacts to the respective hosting providers. How can we get this prioritized? |
|
@jayhill90 @nateinaction Can you please test this scenario in latest Gutenberg plugin? I checked this and I'm not seeing autosave request triggering once the nonce is expired or cookie is cleared. Heartbeat requests are triggered, yes. But not the autosave requests. Can you confirm? |
|
Came across this one after @Mamaduka pointed out the issue I opened was a potential duplicate (which I think I agree on). Here are steps to reproduce this problem.
Another scenario to reproduce this is detailed in the ticket that I opened. (#42400) |
|
Thanks for the detailed reproductions steps, @desrosj. The key for consistently reproducing the issue was only to delete The problem
Possible solutions
Pinging a few folks who collaborated on #16683 for more visibility. Cc. @ellatrix, @gziolo, @kadamwhite. |
|
Could both solutions be implemented? I'm not familiar with Also, I noticed that Finally, there is a mechanism already in Core for refreshing nonces attached to the Heartbeat API. Addressing these last two points may warrant a new ticket, but if it's not too much of a lift, addressing these items at the same time may be beneficial. |
|
I was able to reproduce the error at one of our customers. He deletes browser cookies from time to time to test certain things. As soon as the cookie is deleted starting with I do not know if this can be solved with a check of
I think, this is the correct approach. When retrieving Programmatically, this could be solved like this: let initializedAjaxSend = false;
function waitForValidLogin() {
if (!wp?.heartbeat) {
return Promise.reject();
}
const $ = jQuery;
// Trigger the WordPress auth dialog to be shown
// Unfortunately, wp-auth-check.js does not allow to trigger this via another API like `wp.auth.showLoginDialog()`
// See https://github.com/WordPress/WordPress/blob/d4c39df30839133f3b9a46b01a229233d8f99f10/wp-includes/js/wp-auth-check.js#L162
$(document).trigger("heartbeat-tick", [{ "wp-auth-check": false }, "error", null]);
// Suspend all heartbeat requests as they are not needed atm
// See https://github.com/WordPress/WordPress/blob/d4c39df30839133f3b9a46b01a229233d8f99f10/wp-includes/js/heartbeat.js#L226-L228
// $(window).trigger("unload.wp-heartbeat");
// Unfortunately, we cannot use this event as when the user focus the window again, it requests the admin-ajax.php again
if (!initializedAjaxSend) {
initializedAjaxSend = true;
$(document).ajaxSend((event, jqXHR, { url, data }) => {
if (
url &&
data &&
url.endsWith("/admin-ajax.php") &&
data.indexOf("action=heartbeat") > -1 &&
$("#wp-auth-check-frame").length > 0
) {
jqXHR.abort();
}
});
}
// Unfortuantely, wp-auth-check.js does not trigger events when auth dialog gets hidden
// See https://github.com/WordPress/WordPress/blob/d4c39df30839133f3b9a46b01a229233d8f99f10/wp-includes/js/wp-auth-check.js#L110
return new Promise((resolve) => {
const checkInterval = setInterval(() => {
const element = $("#wp-auth-check-frame");
if (element.length === 0) {
clearInterval(checkInterval);
resolve();
}
}, 100);
});
}Usage: waitForValidLogin.then(() => {
console.log("we have a valid login now");
});Also, I found out that the heartbeat |



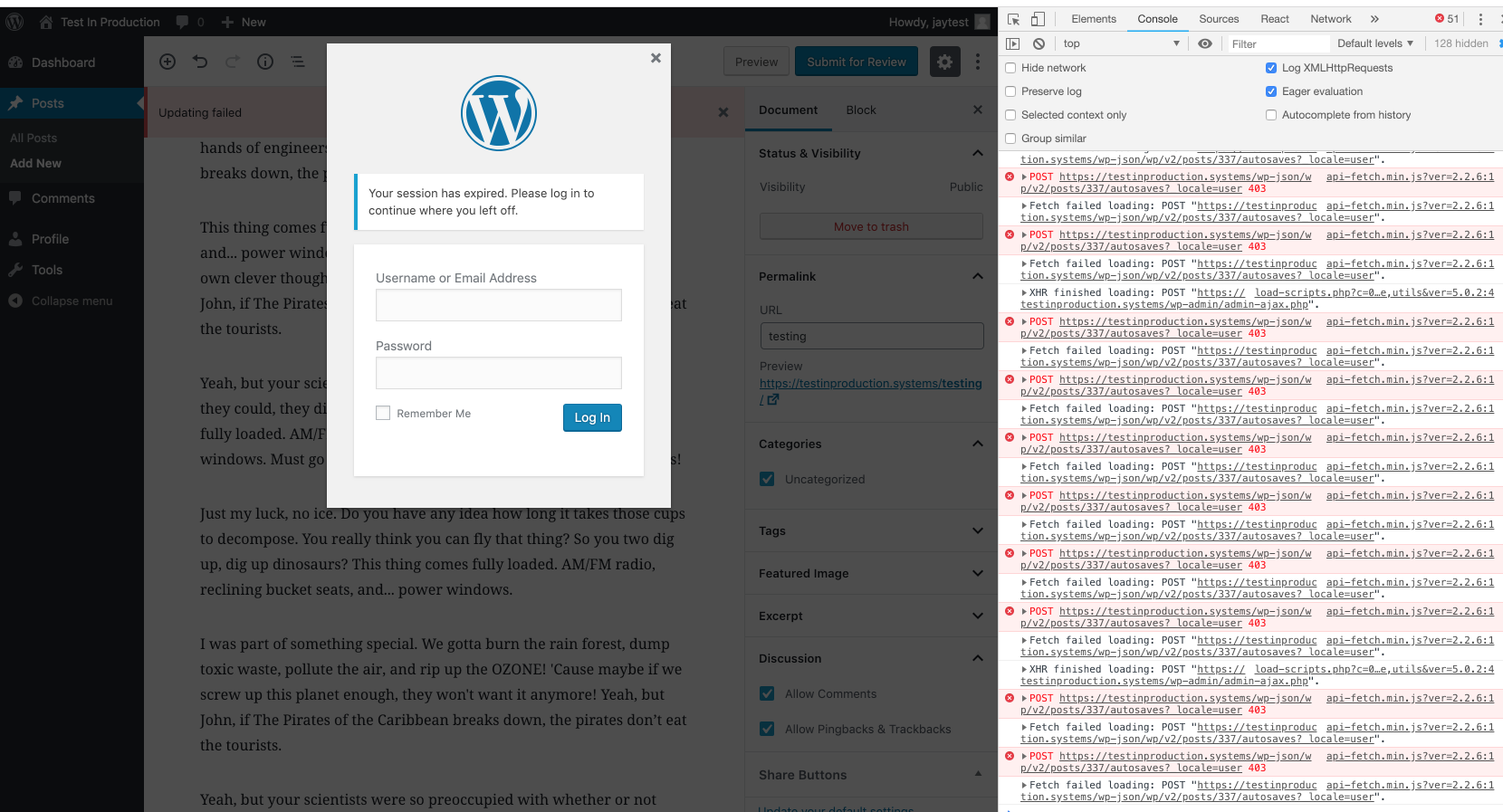
Describe the bug
If a user's session expires while editing a post, Gutenberg continues to make POST requests to the autosave endpoint.
To Reproduce
Expected behavior
If a session expires, WordPress should no longer try to autosave the post.
Screenshots
Desktop (please complete the following information):
Additional context
The text was updated successfully, but these errors were encountered: