-
Notifications
You must be signed in to change notification settings - Fork 2.1k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[Platform] Implement a DeviceAttestationVerifier in Java to allow user to overwrite the DefaultDACVerifier #24297
Comments
|
I have refined the process design, we can see if it's ok. @yufengwangca @tennessee-google Interface Design DescriptionChipDeviceController.java add a new method void setDeviceAttestationVerifierDelegate(DeviceAttestationVerifierDelegate deviceAttestationVerifierDelegate);DeviceAttestationVerifierDelegate.java public interface DeviceAttestationVerifierDelegate {
/**
* Fetch product attestation authority cert from DCL.
*
* @param skid Subject key identifier (SKID)
* @param paaFetchedCallback
*/
void fetchProductAttestationAuthorityCert(byte[] skid, PaaFetchedCallback paaFetchedCallback);
}PaaFetchedCallback.java public interface PaaFetchedCallback {
void onComplete(@Nullable byte[] paaCert);
}AndroidDeviceAttestationVerifier.h class AndroidDeviceAttestationVerifier : public chip::Credentials::DeviceAttestationVerifier
{
public:
AndroidDeviceAttestationVerifier(jobject deviceAttestationVerifierDelegate) :
mDeviceAttestationVerifierDelegate(deviceAttestationVerifierDelegate)
{}
~AndroidDeviceAttestationVerifier();
void VerifyAttestationInformation(const DeviceAttestationVerifier::AttestationInfo & info,
Callback::Callback<OnAttestationInformationVerification> * onCompletion) override;
protected:
jobject mDeviceAttestationVerifierDelegate = nullptr;
};AndroidDeviceAttestationVerifier.cpp pseudocode void AndroidDeviceAttestationVerifier::VerifyAttestationInformation(const DeviceAttestationVerifier::AttestationInfo & info,
Callback::Callback<OnAttestationInformationVerification> * onCompletion)
{
// Fetch PAA Cert
MutableByteSpan paaDerBuffer;
FetchPaaCert(mDeviceAttestationVerifierDelegate, paaDerBuffer);
// Add PAA cert to truststore
EphemeralAttestationTrustStore attestationTrustStore(paaDerBuffer);
// Verify attestation information by DefaultDACVerifier
DefaultDACVerifier defaultDACVerifier(attestationTrustStore);
defaultDACVerifier.VerifyAttestationInformation(info, onCompletion);
}For external callers, |
|
@panliming-tuya in your refined workflow, is the AndroidDeviceAttestationVerifier new C++ class talk to PaaFetcherDelegate?Why this new flow is better than the one Tennessee proposed? I think both flows do the similar job, allow the client to fetch the PAA from DCL on the fly during attestation process. |
@yufengwangca It has been modified and the interface design has been added |
|
how about provide a path which store the PAA files from java-layer to native-layer . |
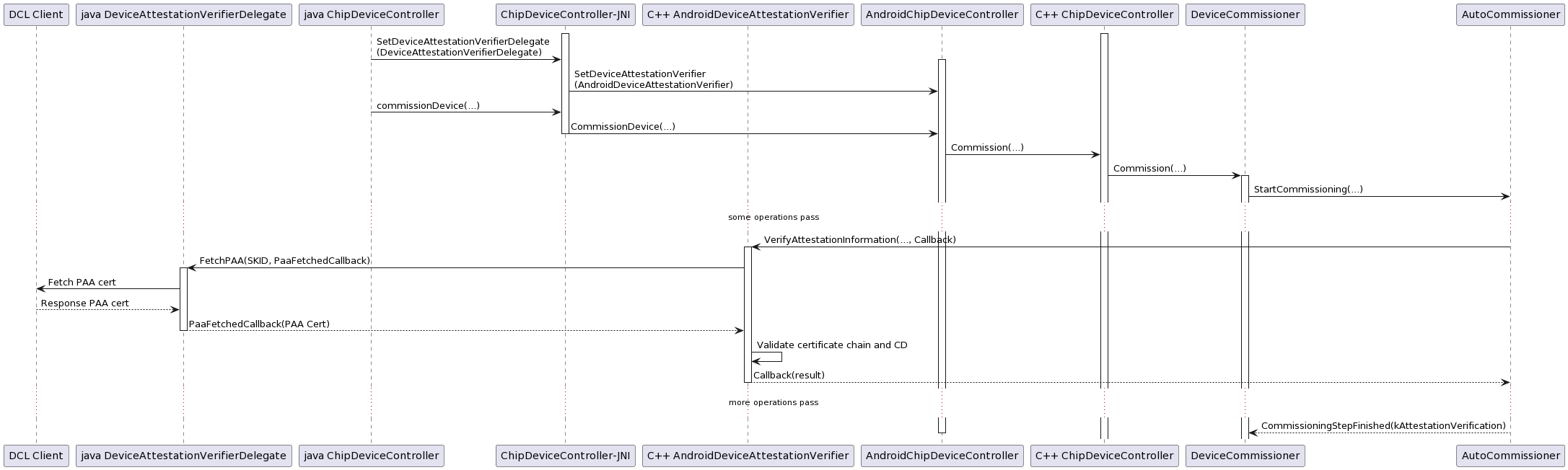
Reproduction steps
Per @tcarmelveilleux
See
AndroidDeviceControllerWrapper::AllocateNewin src/controller/java/AndroidDeviceControllerWrapper.cpp:The Device Attestation Verifier is what could be bridged to Java.
Overall, the flow could be something like:
The general concept:
Regarding the CD trust store, there is already a set of Well-known keys. The CdWellKnownKeysTrustStore used by default should be good enough for a while.
Overall, I agree that these Java APIs are cumbersome. However, unless someone is willing to help rewrite them to "flow-through" with a frameworked design that works for everyone, we have to keep going incrementally.
Platform
android
Platform Version(s)
No response
Type
Manually tested with SDK
(Optional) If manually tested please explain why this is only manually tested
No response
Anything else?
No response
The text was updated successfully, but these errors were encountered: