-
Notifications
You must be signed in to change notification settings - Fork 48
Enable BIOS Secure Boot with OpenCore
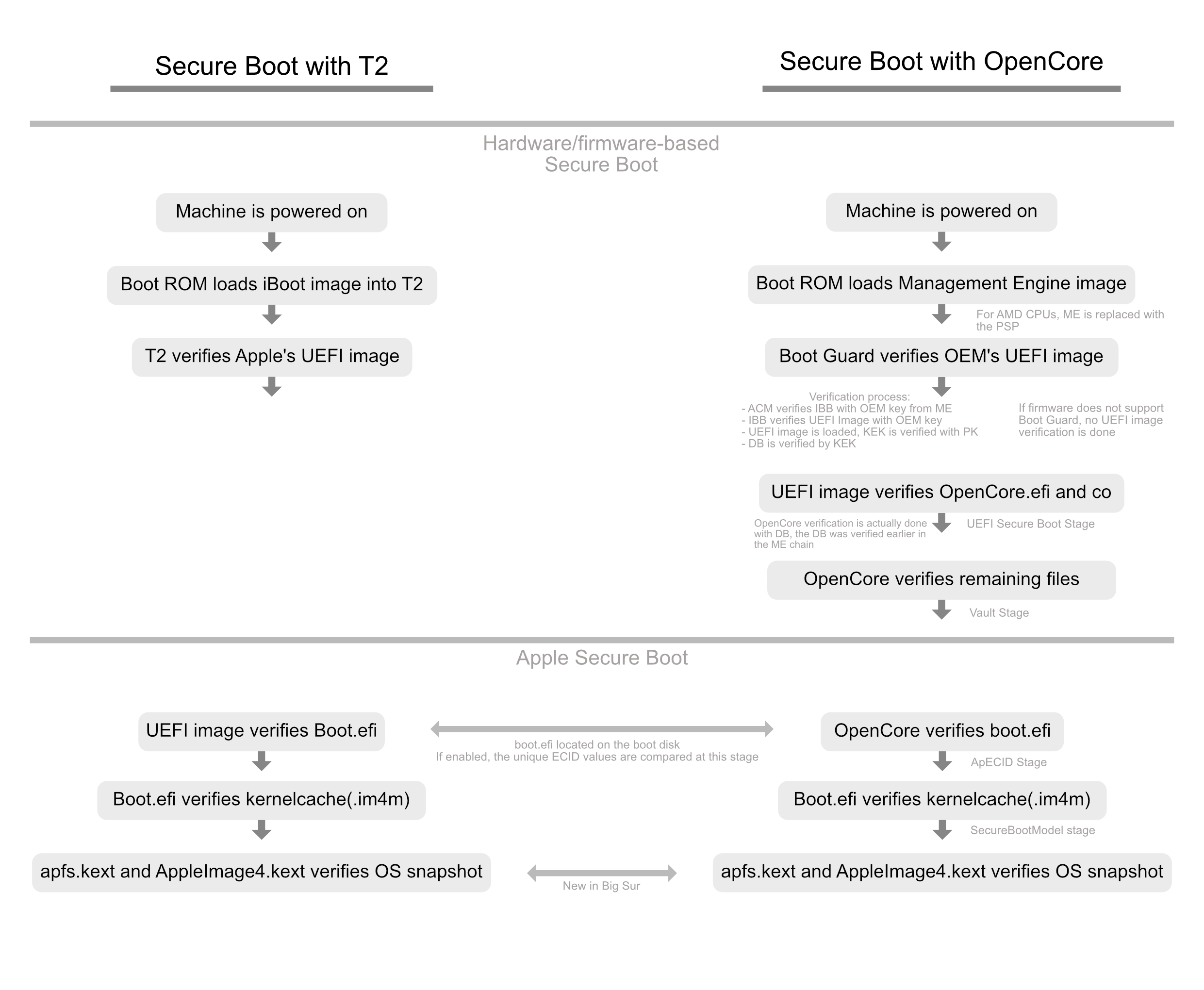
As reported on OpenCore Configuration at Chapter 12.2, OpenCore is designed to provide a secure boot chain between firmware and operating system. On most x86 platforms trusted loading is implemented via UEFI Secure Boot model. Not only OpenCore fully supports this model, but it also extends its capabilities to ensure sealed configuration via vaulting and provide trusted loading to the operating systems using custom verification, such as Apple Secure Boot.
What does it mean? Apple Secure Boot is not equivalent to UEFI Secure Boot i.e. the Secure Boot option which could be enabled in BIOS menu.
Apple Secure Boot is the technology used in Macs to verify the integrity of the operating system at boot: boot loader -> kernel -> snapshot of the system volume.
- If this check fails, macOS won't boot.
- Apple Secure Boot only works during the boot process: once macOS is running it no longer performs any function.
Apple defines 3 Secure Boot modes:
-
Full Security:
- Only allows to boot the installed operating system or another signed version of macOS in which Apple currently trusts.
- It also checks the integrity of the installed version.
- If the check fails, the system offers to reinstall macOS or boot from a different disk.
-
Medium Security:
- Checks that the installed version of macOS is legitimate but not the integrity of the system.
- Lets you boot any signed version of macOS in which Apple has ever trusted.
-
No Security:
- Other systems or versions different from those mentioned in the secure options are allowed.
- There are no requirements on the boot operating system.
OpenCore has a SecureBootModel key that adjusts the Apple Secure Boot mode to make it similar to Macs.
To achieve Full Security with OpenCore v. 0.7.2+, in config.plist you need to:
- set
Debug -> DisableWatchDogtofalse - set
NVRAM -> Add -> csr-active-configto<00000000>and check if SIP is properly enabled launching the commandcsrutil statusinTerminalapp - set
Misc -> Security -> DmgLoadingtoSigned - set
Misc -> Security -> SecureBootModelto-
Default(which is the failsafe value equivalent tox86legacy) or (for example)j132(which corresponds toMacBookPro15,2with minimum macOS 10.13.6) for macOS 11 Big Sur -
Defaultorx86legacyfor macOS 12 Monterey
-
- set
Misc -> Security -> ApECIDto a non-zero random 64-bit integer (which allows using personalised Apple Secure Boot identifiers) generated with a cryptographically secure random number generator - set
Misc -> Security -> VaulttoSecurevalue and then vaulting OC files using the script in defaultOC/Utilities/CreateVaultfolder
In OpenCore Configuration at Chapter 8.5 a list for valid values is reported:
- you can also set
SecureBootModelto the value, from the list, that corresponds to the macOS version you want to boot - you can always put the model that only supports the versions you need of macOS and not the previous ones
- remember that
SMBIOSandSecureBootModeldo not need to match: Apple Secure Boot model does not depend on the SMBIOS model so there is no point in trying to choose the same
It is up to you to decide whether enabling Full Security or not. Atm I recommend enabling Medium Security because it's easier to make changes to the config.plist and to the contents of the EFI/OC folder without having to reapply vaulting to OC files every time!
For enabling Medium Security, please apply steps 1 -> 4 mentioned above for Full Security.
If you would try now to enable UEFI/BIOS Secure Boot in your BIOS, you could not to boot your machine because you secured OpenCore boot phase but OpenCore is not recognized yet as a trusted OS from your BIOS!
UEFI Secure Boot works by using a set of keys embedded in the computer's firmware. These keys (or more precisely, their private counterparts) are used to sign boot loaders, drivers, option ROMs, and other software that the firmware runs:
- All PCs sold today include keys that Microsoft controls.
- If you would like to enable UEFI Secure Boot for macOS, you need to replace your computer's standard keys with ones that you control.
In order to sign your OpenCore install with your own private keys, you'll need Linux! Why? Because atm (September 2021) there is no way to sign properly with macOS!
- Download Ubuntu and create a bootable live USB drive using UNetbootin
- Reboot your computer and boot your USB key (press
F12at boot) - Boot into your live Ubuntu distribution
- Set your Wi-Fi credentials since you need a working Internet connection
- Click on
Show Applications -> Software Updater -> Settings - In
Ubuntu Softwaretab, check first 4 repositories i.e.main,universe,restrictedandmultiverse, and uncheckInstallation medium with Ubuntu; then click onClosebutton - Then click on
Reloadbutton to update from newly added or changed sources - Open a
Terminalapp and type the following commands
sudo apt-get update -y
sudo apt-get install -y efitools
- Now you can create your own three Secure Boot key sets (public and private) PK, KEK and db:
- you need to download Microsoft Certificates:
-
from a trusted repository (Microsoft Windows Production CA 2011 and Microsoft UEFI Driver Signing CA) as reported on
OpenCore Configuration.pdfat Chapter 12.2 - or from my local copy (MicWinProPCA2011_2011-10-19.crt and MicCorUEFCA2011_2011-06-27.crt)
-
from a trusted repository (Microsoft Windows Production CA 2011 and Microsoft UEFI Driver Signing CA) as reported on
- you can download a short script for this purpose make_keys.sh
- or you can copy-and-paste it from the following listing into a file (I call it
make_keys.sh)
- you need to download Microsoft Certificates:
!/bin/bash
# Copyright (c) 2021 by profzei
# Licensed under the terms of the GPL v3
# Common Name : Huawei MBXP 2018
echo -n "Enter a Common Name to embed in the keys: "
read NAME
openssl req -new -x509 -newkey rsa:2048 -sha256 -days 3650 -nodes -subj "/CN=$NAME Platform Key" -keyout PK.key -out PK.pem
openssl req -new -x509 -newkey rsa:2048 -sha256 -days 3650 -nodes -subj "/CN=$NAME Key Exchange Key" -keyout KEK.key -out KEK.pem
openssl req -new -x509 -newkey rsa:2048 -sha256 -days 3650 -nodes -subj "/CN=$NAME Image Signing Key" -keyout ISK.key -out ISK.pem
GUID=`python3 -c 'import uuid; print(str(uuid.uuid1()))'`
echo $GUID > myGUID.txt
cert-to-efi-sig-list -g "$GUID" PK.pem PK.esl
cert-to-efi-sig-list -g "$GUID" KEK.pem KEK.esl
cert-to-efi-sig-list -g "$GUID" ISK.pem ISK.esl
openssl x509 -in MicWinProPCA2011_2011-10-19.crt -inform DER -out MsWin.pem -outform PEM
openssl x509 -in MicCorUEFCA2011_2011-06-27.crt -inform DER -out UEFI.pem -outform PEM
cert-to-efi-sig-list -g "$GUID" MsWin.pem MsWin.esl
cert-to-efi-sig-list -g "$GUID" UEFI.pem UEFI.esl
cat ISK.esl MsWin.esl UEFI.esl > db.esl
sign-efi-sig-list -k PK.key -c PK.pem PK PK.esl PK.auth
sign-efi-sig-list -k PK.key -c PK.pem KEK KEK.esl KEK.auth
sign-efi-sig-list -k KEK.key -c KEK.pem db db.esl db.auth
chmod 0600 *.key
echo ""
echo ""
echo "For use with KeyTool, copy the *.auth files to a FAT32 USB"
echo "flash drive or to your EFI System Partition (ESP)."
echo ""
- Run
make_keys.sh:
- Be sure to set the executable bit:
chmod a+x make_keys.sh - This script prompts you for a common name (which will help you identify your keys and differentiate them from other keys) to embed in your keys: I suggest, for example,
Huawei MBXP 2018. - please, check
myGUID.txtis not empty (more myGUID.txt), otherwise you could have some issues with Python interpreter!
- Save all the generated keys on a safe USB flash drive.
In order to sign OpenCore Efi binaries with your own keys (which have also embedded standard Microsoft Certificates for dual boot purpouses):
- Create a new folder:
mkdir Signing_OpenCoreand
- download into this folder sign_opencore.sh script and set its executable bit:
chmod a+x sign_opencore.sh - copy into this folder
ISK.keyandISK.pemfiles you generated before
- The script
sign_opencore.shneeds 2 arguments:
- URL for downloading OpenCore Release package
- OpenCore Release version
- Run the following command in
Terminalapp:
./sign_opencore.sh https://github.com/acidanthera/OpenCorePkg/releases/download/0.7.3/OpenCore-0.7.3-RELEASE.zip 0.7.3
- Note: you should see some warnings: do not worry about them since they do not harm! All Efi binaries signed (that have produced those warnings) will work fine!
- Inside
Signing_OpenCore/Signedfolder you should find all neededOpenCoreefi binaries signed with your own keys! - Save
Signing_OpenCore/Signedfolder content into a safe USB flash drive. - Now you don't need anymore your Ubuntu live distribution so you can reboot your machine!
Some UEFIs provide the means to install your own keys using their own built-in user interfaces: for more details and explicative screenshots, please, refer to:
- http://www.rodsbooks.com/efi-bootloaders/controlling-sb.html
- https://habr.com/en/post/273497/ (Russian article)
Huawei Matebook X Pro Insyde Bios does not provide any Secure Boot key management interface, so we need a more general approach to perform such tasks using KeyTool.efi!
- Download from my local repository
KeyTool.zipfile from here and unzip it into a FAT32 formatted USB flash drive: please, check to get a file structure similar to the following

- Copy your own generated keys
db.auth,KEK.authandPK.authintoEFIfolder on the same FAT32 formatted USB flash drive as shown in the previous figure - Reboot your computer and boot your FAT32 formatted USB flash drive (press
F12at boot); the result should resemble the following:

- Select
Edit Keysoption

- Start by replacing
The Allowed Signature Database (db):- Select
Replace Key(s)option - Navigate into your FAT32 formatted USB flash drive (for Matebook X Pro you should see a path like
PciRoot(0)/Pci(0x14,0x0)/Usb ...which indicates your USB flash drive while the other path shown is your SSD)
- Select
- Select the associated
.authfile

- Do the same for
The Key Exchange Key Database (KEK)andThe Platform Key (PK)in this order - Summarizing, you need to replace (repeating steps #5 + #6) first
db.auth, thenKEK.authand finallyPK.auth - Exit and shutdown your machine
- Boot into the BIOS/UEFI settings and check if Secure Boot option is reported as
Enabled: if all went right, you should not to enable Secure Boot option, but it should be already set asEnabled! - Now you could boot macOS using OpenCore Efi binaries previously signed with your own keys with UEFI Secure Boot enabled (since standard Microsoft Certificates have been included, you could also boot
Windows 10orWindows 11from OpenCanopy Boot picker without any issues)
Adding OpenCore entry to UEFI Boot
Activate Surround Sound via MIDI on internal speakers
Add custom shortcuts to Fn hotkeys
Drive Intel(R) UHD Graphics 620
Drive Intel(R) WiFi network card
Enable BIOS Secure Boot with OpenCore
Handle EFI partition from Windows
Keep Bluetooth devices paired on macOS and Windows
Prevent Windows partition from automatically mounting
Remove unnecessary Intel(R) Bluetooth firmware files
Remove unnecessary Intel(R) WiFi firmware files