-
Notifications
You must be signed in to change notification settings - Fork 88
Local Key Setup
In TFC, the Transmitter Program needs to share data securely to the Receiver Program. This is done by encrypting the data with what is called the local key. Local key will be delivered to Receiver Program automatically during the first setup, and at any later point when the user chooses to enter the /localkey command.
Local key is the most important key to keep secret because it protects the delivery of all encryption keys that protect the communication. Because this key needs to be delivered from Transmitter to Receiver Program via the Networked Computer (that might be compromised), it needs protection. The protection is done by encrypting the local key with another key called the key encryption key. This key must be manually typed into the Receiver Program's prompt.
WARNING! The key the Transmitter Program displays is the SECRET key encryption key. An attacker who has hacked the Networked Computer can steal the encrypted local key. If they can also see the key encryption key, they can decrypt ALL user's communications. It is therefore VITAL to make sure the user is in a safe physical environment when they perform the local key setup.
The user must type the local key decryption key to the Receiver program.
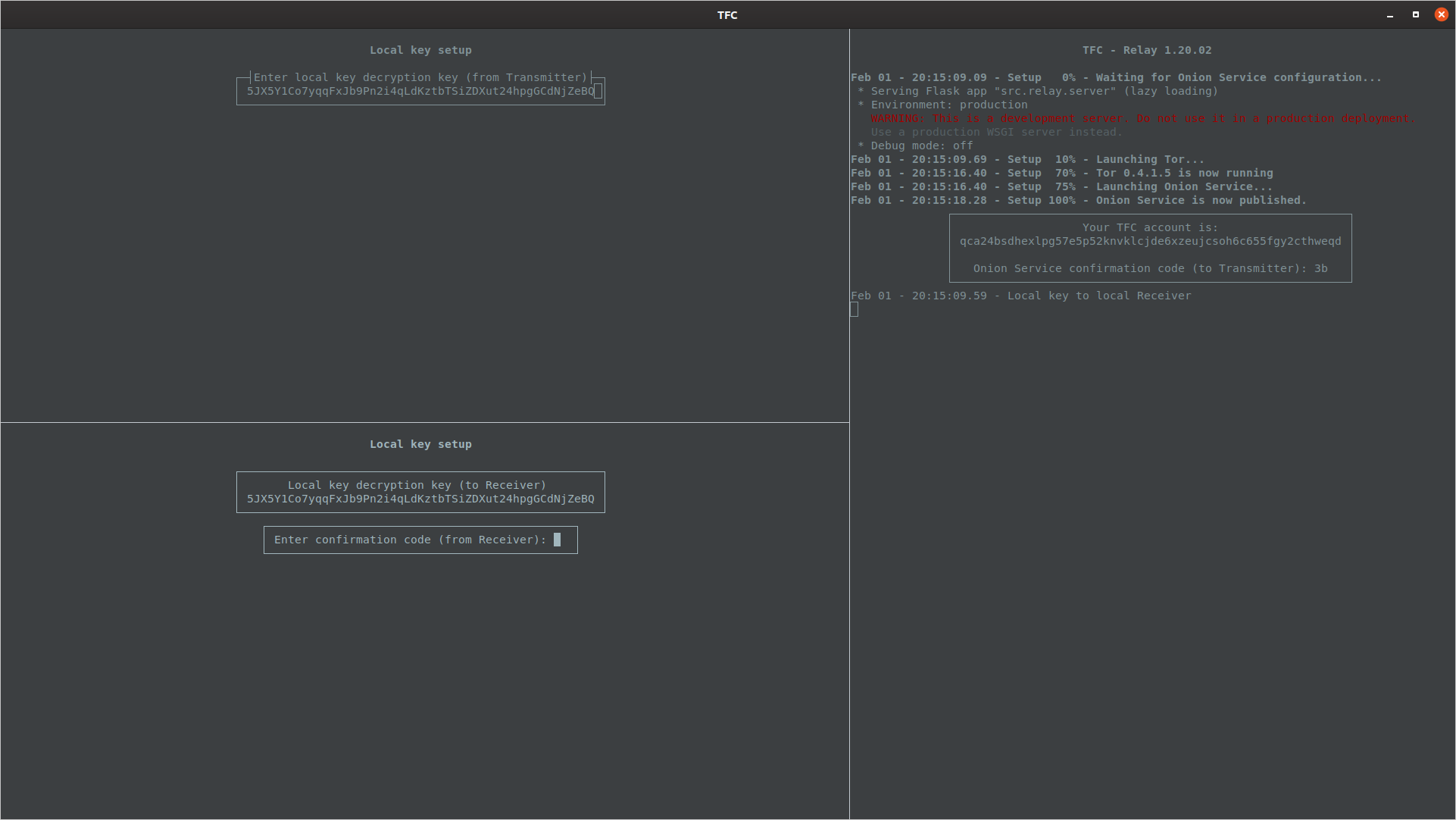
Once the Receiver Program has decrypted the local key, it will reset the terminal (to hide the key decryption key) and display the user a confirmation code.
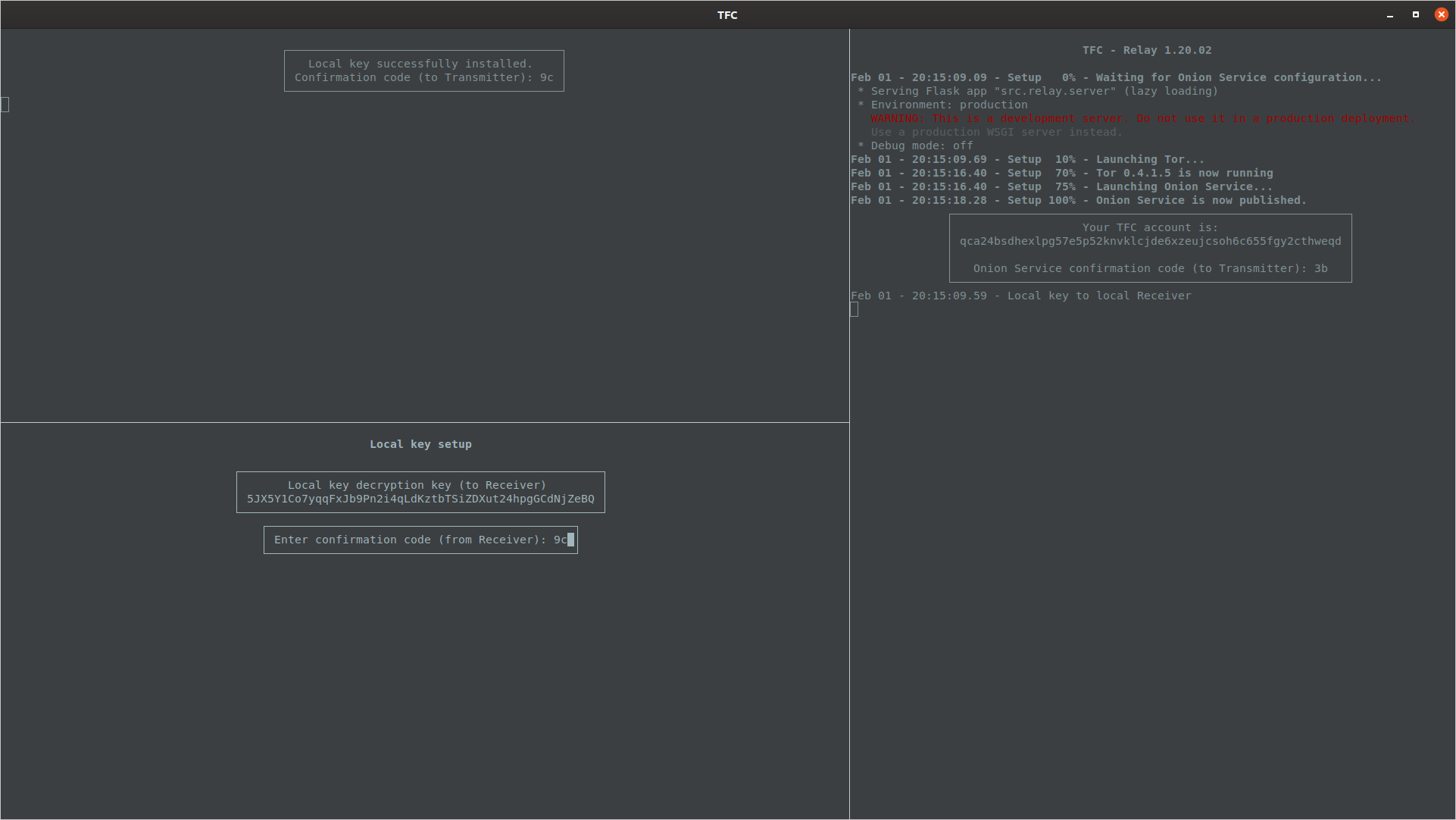
After typing the confirmation code, Transmitter Program will also reset the terminal, which completes the local key setup. If this was the initial setup, Transmitter Program will proceed to let the user add the first contact. Otherwise, it returns to the active conversation.