-
Notifications
You must be signed in to change notification settings - Fork 8.3k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[Security Solution] Find a way to reuse tests between ESS and Serverless suites #161537
Comments
|
Pinging @elastic/security-detections-response (Team:Detections and Resp) |
|
Pinging @elastic/security-threat-hunting (Team:Threat Hunting) |
|
Pinging @elastic/security-solution (Team: SecuritySolution) |
|
Pinging @elastic/security-defend-workflows (Team:Defend Workflows) |
|
Adding Defend Workflows label so we can follow along and give feedback on this |
|
Sharing some information to give more context to the ticket: There is a Kibana Serverless testing document with some guidelines around how to proceed with the automation on serverless, agreed by various stakeholders. About the structure, the original guideline is the following one: For the Cypress-specific side of things, that would be translated to the reuse of |
|
Notes from a @elastic/security-defend-workflows meeting:
|
|
@kevinlog may you please elaborate on this?
At some point in the pipeline/flow we'll use a real serverless environment so it would be great to hear about those concerns to be taken into consideration with time :) |
Yes, this was our concern. It's understood that this would be a longer term goal. If we have a plan to use a real serverless environment then that works! |
I'm sorry if I miss something, since I'm just familiarising myself with the serverless offering and its testing plan, but based on the doc @MadameSheema shared, it is not a global goal to run the same tests against both stateful and serverless Kibana, although, I'd imagine that would help a lot to ensure SW quality (but results far slower test runs). @banderror could you please elaborate what the goal is here? is it to opt in some existing ESS tests to ensure features work on serverless? or maybe all of them?
|
|
@gergoabraham I'm sorry for the terribly delayed response.
True, based on the information I have I think it's not a global (Kibana-wide) goal. The Kibana Serverless e2e Test Guide (internal document) proposes that:
We've also got the following comment from the AppEx QA team:
Several teams have expressed some concerns with that approach, including the Threat Hunting folks. This especially applies to the two teams under Detection and Response, because most of our functionality is going to work the same way in ESS (self-managed) and Serverless. All the API endpoints available in Serverless are going to work exactly the same way as in ESS too. So we want to be able to reuse our existing test coverage, instead of duplicating it in a different folder. We also don't think that not covering Serverless with existing tests and only writing Serverless tests for features that work differently in Serverless, would be a good way for developing the Detection Engine and maybe other features of Security Solution. Many people from D&R and AET are on board with the idea of reusing existing tests, including @oatkiller @marshallmain @MadameSheema @MindyRS.
The goal is to reuse our existing E2E (Cypress) and API integration (FTR) tests in all cases where a feature under test works exactly the same way in Serverless and ESS. For those features that work differently, we will need to have ESS-specific and Serverless-specific tests. The amount of reusable and environment-specific tests will depend on every area and team, but for D&R features and tests we expect a very high ratio of reusable-to-specific tests. When we figure out how to reuse tests, we can start to gradually opt them in (add them to the serverless suite) until we feel that the coverage for Serverless is full or sufficient. More about reusing Cypress tests in the next comment. @gergoabraham Please let me know if I was able to answer your questions. |
|
@MadameSheema has been working on POCs for reusing our existing
I guess people tend to prefer the second POC that allows us to keep all Cypress tests (reusable, serverless-specific, and ess-specific) in @MadameSheema started to work on the implementation PR based on the second POC: #162698 |
|
@banderror Thank you for your detailed answer, now I think I have a good grasp of the context. There are some really good arguments on both sides of reusing or not reusing tests, but as our features from Defend Workflows team work practically the same on both environments, I totally agree with the reuse of the tests. Also, I support the idea of tagging: I think we rather implement new functionalities organized by features and not by environments, so it's much easier to overview a feature and its tests in one place, and making sure it's okay for serverless only by adding a tag. |
… using Mocha Tagging (#166755) # Summary - Addresses #161537 ## Description - This PR follows the second option defined in this [document](https://docs.google.com/document/d/1mqkpjDdFQRFvx_RPvNmjstVj8SXYMr2mrETMv3esda8/edit#heading=h.rpv1zyeb04ay) the [Mocha tagging ](https://github.com/mochajs/mocha/wiki/Tagging) - It introduces a new folder `x-pack/test/security_solution_api_integration` which will serve as a centralized location to meet all the requirements related to renaming tests appropriately and grouping similar tests together. It will facilitate the management of tests that must be run in Serverless and ESS environments. - Within this folder, there is a "config" subdirectory that stores base configurations specific to both the [Serverless](https://github.com/elastic/kibana/pull/166755/files#diff-afe1f42d5ac2006de8dc09069448b9e8734a6a950586376cd6e8eeb9110ab5f1R1) and [ESS](https://github.com/elastic/kibana/pull/166755/files#diff-4a60bd8c91da08a3f7ec14bf3bfef8449af155611374c32579b0318da03e292cR1) environments, These configurations build upon the base configuration provided by test_serverless and api_integrations, incorporating additional settings such as environment variables and tagging options. - It demonstrates scenarios involving `@ess`, `@serverless`, and `@brokenInServerless`. - The file` x-pack/test/security_solution_api_integration/test_suites/detections_response/rule_creation/create_rules.ts` is functional in both **Serverless** and **ESS**. However, some tests related to roles are currently skipped for Serverless until they are resolved, and these tests are tagged with `@brokenInServerless`  ## CI - It includes a new entry in the ftr_configs.yml to execute the newly added tests in the pipeline. - It involves the addition of mochaOptions in both serverless/config.base.ts and ess/config.base.ts. In the case of serverless, it includes **@serverless** while excluding @brokenInServerless. Similarly, for **ess**, it includes @ess and excludes **@brokenInEss**. from `x-pack/test/security_solution_api_integration/config/serverless` 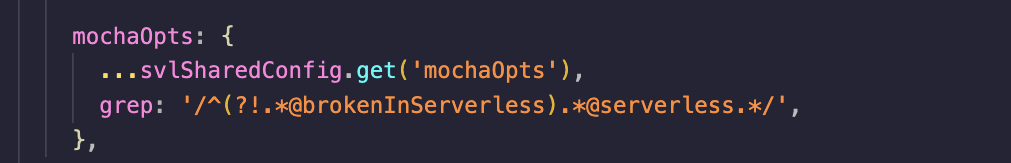 ## Update in x-pack/test/detection_engine_api_integration - The `create_rules.ts` and `create_rule_exceptions` files have been relocated from `x-pack/test/detection_engine_api_integration/security_and_spaces/group1` to their respective domains within the `x-pack/test/security_solution_api_integration` folder. - The util files now are copied over from the old folder `x-pack/test/detection_engine_api_integration` to the new folder and will be removed once all tests are moved to the new folder to don't break the existing tests --------- Co-authored-by: kibanamachine <[email protected]>
… using Mocha Tagging (elastic#166755) # Summary - Addresses elastic#161537 ## Description - This PR follows the second option defined in this [document](https://docs.google.com/document/d/1mqkpjDdFQRFvx_RPvNmjstVj8SXYMr2mrETMv3esda8/edit#heading=h.rpv1zyeb04ay) the [Mocha tagging ](https://github.com/mochajs/mocha/wiki/Tagging) - It introduces a new folder `x-pack/test/security_solution_api_integration` which will serve as a centralized location to meet all the requirements related to renaming tests appropriately and grouping similar tests together. It will facilitate the management of tests that must be run in Serverless and ESS environments. - Within this folder, there is a "config" subdirectory that stores base configurations specific to both the [Serverless](https://github.com/elastic/kibana/pull/166755/files#diff-afe1f42d5ac2006de8dc09069448b9e8734a6a950586376cd6e8eeb9110ab5f1R1) and [ESS](https://github.com/elastic/kibana/pull/166755/files#diff-4a60bd8c91da08a3f7ec14bf3bfef8449af155611374c32579b0318da03e292cR1) environments, These configurations build upon the base configuration provided by test_serverless and api_integrations, incorporating additional settings such as environment variables and tagging options. - It demonstrates scenarios involving `@ess`, `@serverless`, and `@brokenInServerless`. - The file` x-pack/test/security_solution_api_integration/test_suites/detections_response/rule_creation/create_rules.ts` is functional in both **Serverless** and **ESS**. However, some tests related to roles are currently skipped for Serverless until they are resolved, and these tests are tagged with `@brokenInServerless`  ## CI - It includes a new entry in the ftr_configs.yml to execute the newly added tests in the pipeline. - It involves the addition of mochaOptions in both serverless/config.base.ts and ess/config.base.ts. In the case of serverless, it includes **@serverless** while excluding @brokenInServerless. Similarly, for **ess**, it includes @ess and excludes **@brokenInEss**. from `x-pack/test/security_solution_api_integration/config/serverless`  ## Update in x-pack/test/detection_engine_api_integration - The `create_rules.ts` and `create_rule_exceptions` files have been relocated from `x-pack/test/detection_engine_api_integration/security_and_spaces/group1` to their respective domains within the `x-pack/test/security_solution_api_integration` folder. - The util files now are copied over from the old folder `x-pack/test/detection_engine_api_integration` to the new folder and will be removed once all tests are moved to the new folder to don't break the existing tests --------- Co-authored-by: kibanamachine <[email protected]>
|
The problem of reusing API integration (FTR) tests has been addressed by @WafaaNasr in #166755. The leftover work which is out of the scope of this ticket:
|
Related PRs: #157166, #158707
Summary
Security Solution teams are going to need to start adding tests, that will be executed against Serverless environments, to the
x-pack/test_serverlessfolder. In this folder, we will need to have both API integration and E2E functional tests. Support for Cypress was added in #158707.We already have a lot of existing tests, for example:
x-pack/plugins/security_solution/cypressx-pack/test/detection_engine_api_integrationThis is a lot of existing tests, and we'd like some of them to run in both ESS and Serverless. Instead of duplicating them for Serverless, we'd like to be able to reuse them as much as possible. This is especially important for Detections features that are going to work mostly the same way in ESS and Serverless.
How we could do this
Some thoughts:
Todo
x-pack/plugins/security_solution/cypressx-pack/test/detection_engine_api_integrationThe text was updated successfully, but these errors were encountered: