-
Notifications
You must be signed in to change notification settings - Fork 206
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
TUD and Traefik redirect issue #36136
Comments
|
Applicable links: Infrastructure directory - https://github.com/department-of-veterans-affairs/vsp-infra-application-manifests/tree/main/apps/vsp-identity/test-user-dashboard/utility TUD readme (repo) - https://github.com/department-of-veterans-affairs/vsp-test-user-dashboard |
|
Joe, Peter, Ryan Beckwith and I attended Ops Office Hours on Friday to talk about the problem. Matt Leclerc gave Ryan some direction. Ryan, Darius and I are meeting later this hour to review the problem, the infrastructure architecture, Matt's suggestions, etc., then we're gonna mob on trying to get this fixed today. |
|
After standup yesterday morning, Ryan, Darius, Peter and I met to discuss the problems with the TUD redirects. Ryan shared the following posts:
Here's a thread about the difficulties we experienced with the updates to the I tried updating PRs to update
Matt Leclerc posted this last night, which looks promising, and explains why the updates to
Overall, things went super slow yesterday because we were not able to see the effects of our updates to We also discovered that the workflow for updating TUD dev that we inherited is broken. That needs to be fixed some day. |
|
We need to slow down and regroup after attempting a bunch of config changes in the past few days. Let's --
|
|
It turned about part of this issue had to do with Gatsby and it not liking links that don't end with a trailing Ryan discovered the fix was to simply add a trailing slash to the GitHub OAuth callback URL: This: was changed to this: GitHub was sending a request to There is quite a bit of confusion regarding Gatsby and how they implemented links and handle redirects. Examples: |
|
The underlying problem did end up being gatsby. The secondary issue was not having |
|
Hooray, this issue is resolved! |
The gateway application has been put up, but there is still a strange redirect occurring.
traefikis appending port:9000to the host, which then causes the whole request to fail.Trying to determine if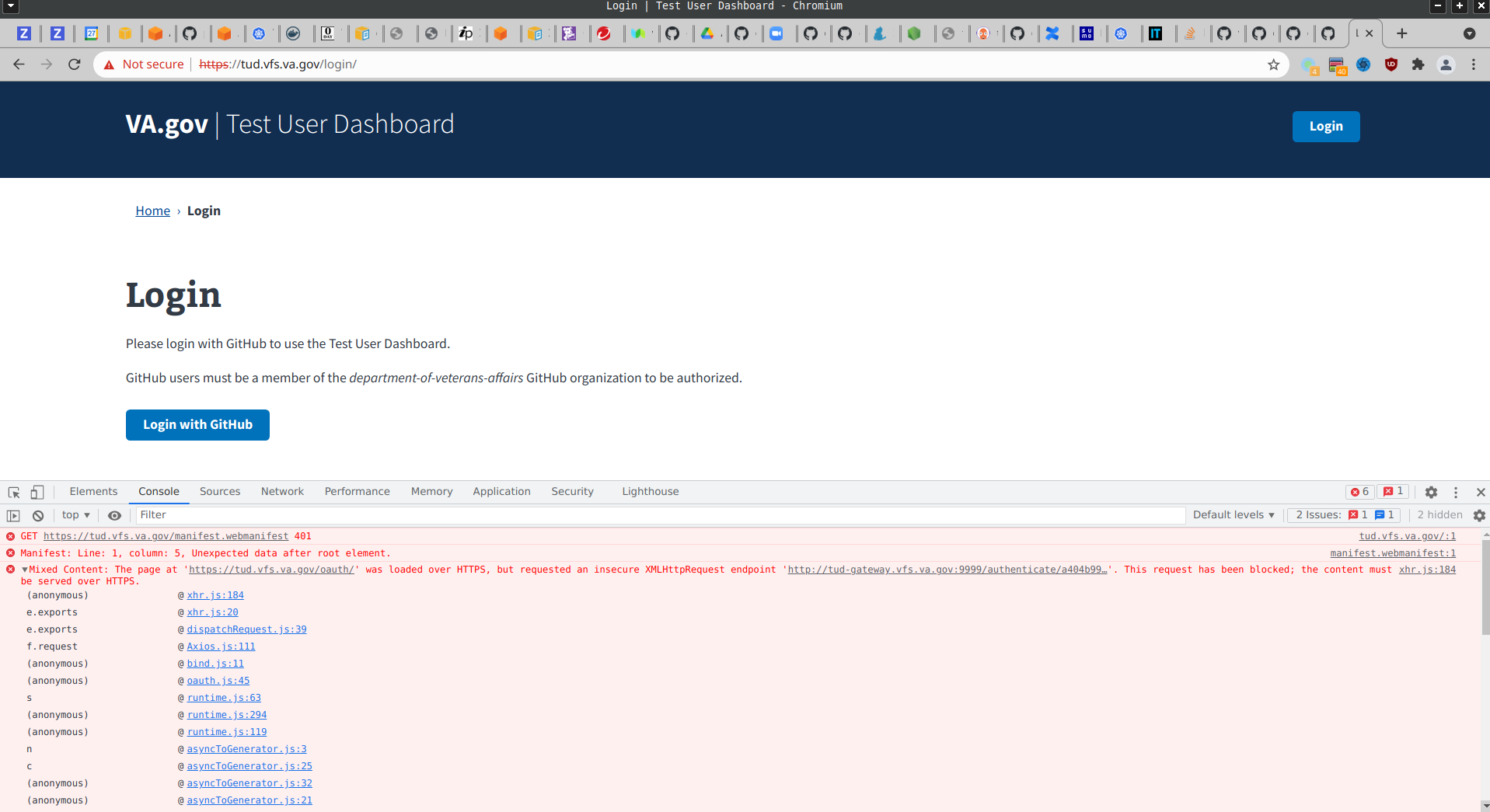
traefikis redirecting to SSL, or if the browser is doing it.Looking into
traefikfurther to determine why it is redirecting and what it is supposed to be doing.The text was updated successfully, but these errors were encountered: