HorusEyesRat | OUTDATED | New remote acces tool available written in C# here : https://github.com/arsium/EagleMonitorRAT !
Remote Access Tool Written in VB.NET
In the current circumstances , I authorize you to hack your government against the measurements they took for the "covid-19". The deprivation of the liberty has to be punished.
Server : .NET 4.8
Client : .NET 4.5
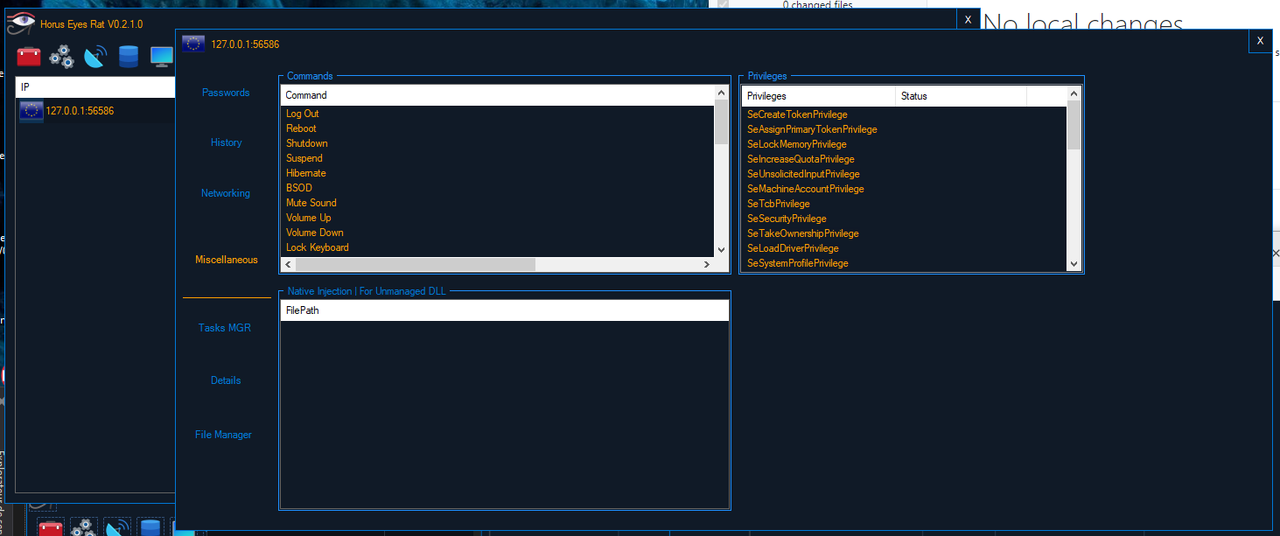
Features :
- Supports DNS (No-IP for example)
- Multi-Threaded
- Asynchronous
- Packets Serialization
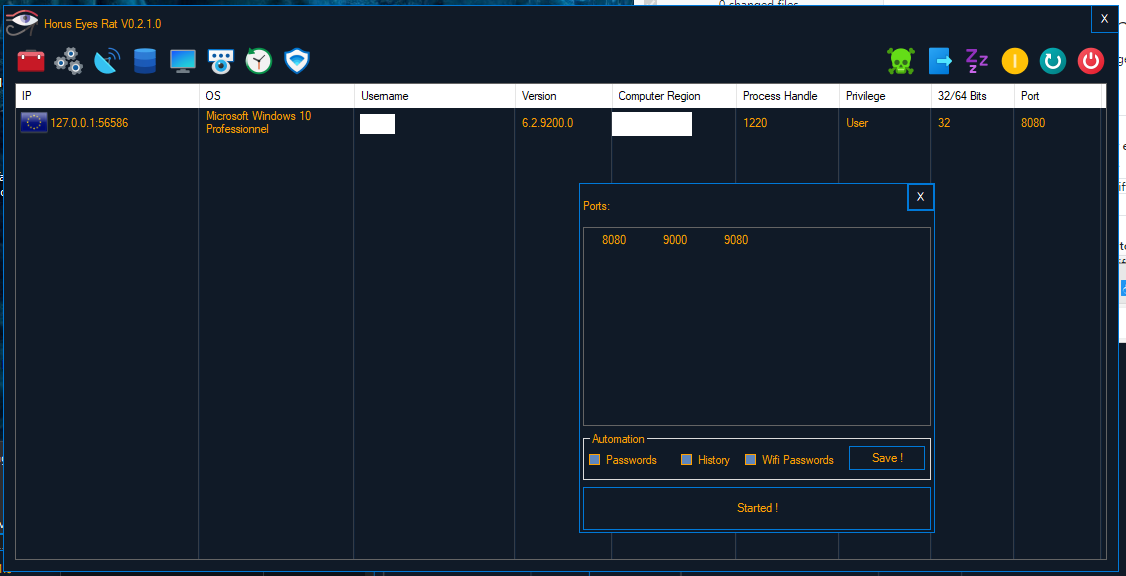
- Multi Ports Listener
- Automation Tasks when client is connected
- Save Settings for automation tasks
- Blur ScreenLocker
- Monitor Rotation (0 , 90 , 180 , 270 degrees)
- Hide & Show Taskbar
- Hide & Show Desktop Icons
- Hide & Show Cursor
- Swap & Normal State Mouse Buttons
- Lock & Unlock Keyboard
- Empty Bin
- Native Injection : You can inject an unmanaged DLL (C++ , C , D...)
- 32 & 64 bits stubs
- Mass Tasks: Passwords Recovery , History Recovery , Wifi Passwords Recovery
- Tasks Manager : Kill , Resume , Pause
- Passwords Recovery (+35 web browsers based on chromium)
- History Recovery (+35 web browsers based on chromium)
- Wifi Passwords Recovery
- Power : Log out , Reboot , Shutdown , Hibernate , Suspend
- BSOD
- Increase Volume
- Decrease Volume
- Mute | Unmute Volume
- Save all passwords | history recovered
- Export History | Passwords as .csv file
- Installation : Set a task in TaskScheduler | Hidden from startup + copy file in local user path hidden
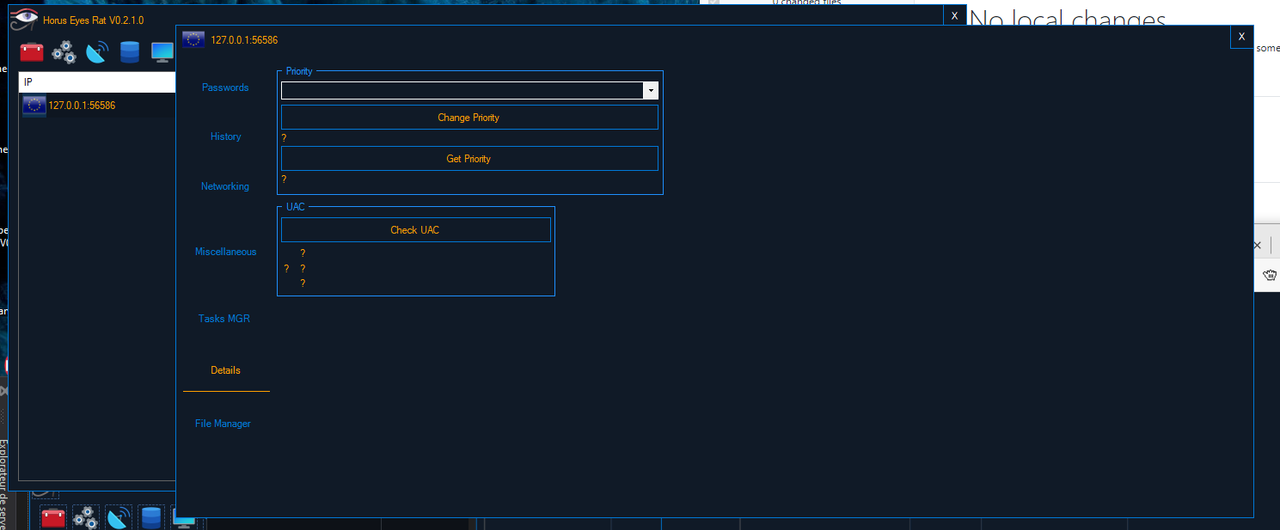
- Ability to change your client priority
- Ability to ask for privileges
- Check UAC at different levels (if enable or not)
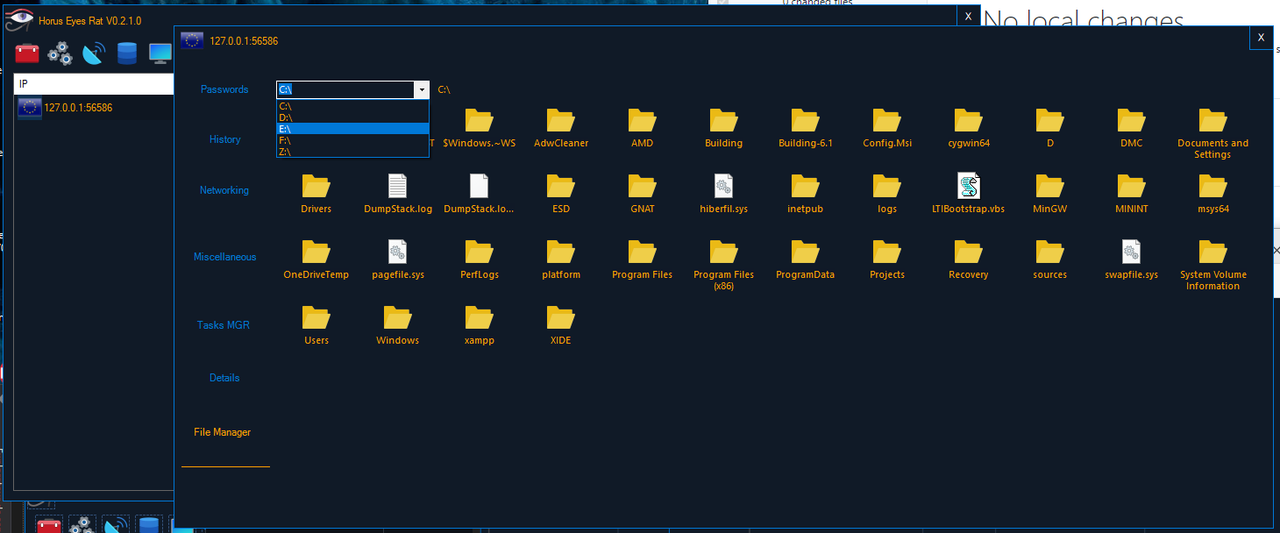
- File Manager : Create Directory, Open File, Delete File, Move File To Bin, Download File
Sources :
- System.Data.SQLite.dll : https://github.com/Faithlife/System.Data.SQLite
- IpAPI : https://ip-api.com/
- Passwords Recovery : Modded Library Based on : https://github.com/0xfd3/Chrome-Password-Recovery
- Wifi Passwords Recovery : Modded Library Based on : https://github.com/r3nhat/SharpWifiGrabber
- Loading Unmanaged DLLs in Managed EXE : Class comes from : https://github.com/schellingb/DLLFromMemory-net with manual mapping for those dlls.
- Code I used to test the loading of dll in memory (in C++ but also worked in D Lang) :
BOOL APIENTRY DllMain( HMODULE hModule,
DWORD ul_reason_for_call,
LPVOID lpReserved
)
{
switch (ul_reason_for_call)
{
case DLL_PROCESS_ATTACH:
MessageBoxA(NULL, "Hello World!", "Dll says:", MB_OK);
case DLL_THREAD_ATTACH:
case DLL_THREAD_DETACH:
case DLL_PROCESS_DETACH:
break;
}
return TRUE;
}
Note for injection:
- 32 bit dlls (in c++ or whatever you want) is for 32 bit stub
- 64 bit dlls (in c++ or whatever you want) is for 64 bit stub
- Don't inject a 32 bit dll in 64 bit stub and vice-versa (you can try if you want but the server will give you an error :))
- To use File Manager, make Refresh => All
Preview :