-
Notifications
You must be signed in to change notification settings - Fork 25
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[TEST] Add state machine #63
Conversation
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thanks a lot for your PR!
A suggestion: if we're going to do things properly, we should do them this way:
- Instead of having the stateMachine in a hook, it should become an integral part of the aio5gc's UEState, which would make it possible to properly implement the transition
RegistrationRequest -> AuthReq and
RegistrationRequest -> RegistrationAcccept depending on current status, for example.
And if AuthReject, we start again from the beginning etc... basically allowing us to validate the whole call flow. - And then, we modify the hook system so that we can insert a hook at each transition (eg. in the callbacks) rather than as we do at present, as the whole point of having a stateMachine with transitions was to check the correct flow of messages, which might be different in each test.
Make sure to accept DCO as well.
|
Thanks for the new commit! if !ue.GetInitialContextSetup() {
return errors.New("[5GC][NGAP] This UE has no security context set up")
}
if ue != ranUe {
return errors.New("[5GC][NGAP] RanUeNgapId does not match the one registred for this UE")
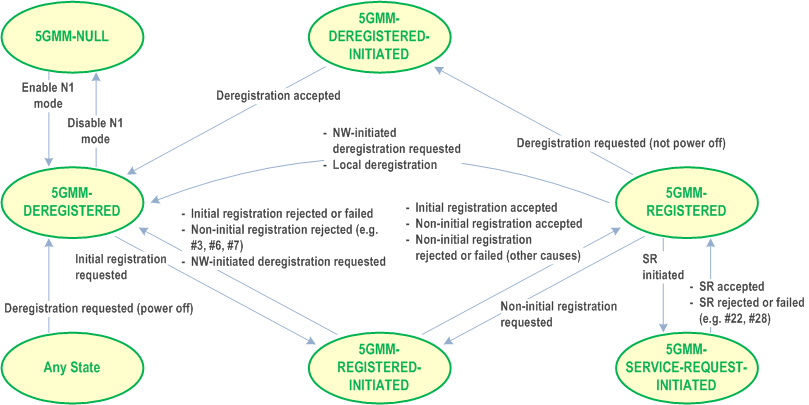
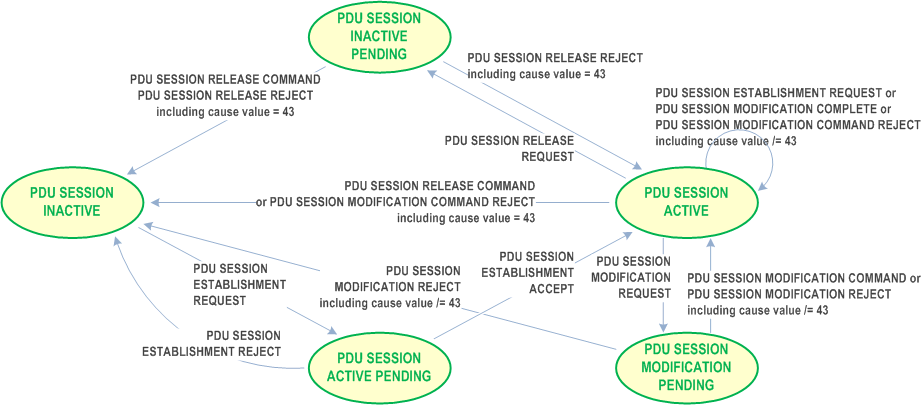
}Basically, the point is that you have one handler per state (eg. the callback). Note that you can have several PDU Sessions, so you'll need a global state machine + one per PDU Session (this is what's normally done in the AMF for the 5GMM state machine the SMF for the 5GSM state machine per PDU Session). This is something we would also need to implement on PacketRusher's side instead of our current big global handler. See for reference: 24.501 Figure 5.1.3.2.1.1.1: 5GMM main states in the UE: And 24.501 Figure 6.1.3.2.1.1: The 5GSM sublayer states for PDU session handling in the UE: |
test/aio5gc/lib/tools/nasCoder.go
Outdated
| @@ -46,7 +46,8 @@ func Encode(ue *context.UEContext, msg *nas.Message) ([]byte, error) { | |||
| } | |||
|
|
|||
| // Plain NAS message | |||
| if ue == nil || !ue.SecurityContextAvailable { | |||
|
|
|||
| if ue == nil || !(ue.GetSecurityContext() != nil) { | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
You should use your state machine instead of doing this kind of check. You should have a branch of states where you are sure that securityContext is available. The goal of having a state machine is that when you arrive to a given state, you are sure that some preconditions are valid, here that the SecurityContext is available.
Then you have an Encode for state SecurityContextAvailable and an when it is not the case. Same for Decode.
|
Thanks a lot for your work! |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Cool! Make sure that nasEncoder changes depending the states to avoid all these checks a bit everywhere
Same for decoder, you should not allow a non-integrity protected message after auth.
Don't forget about DCO on previous commits, no FSM global, and previous comments as well :-)
Thanks a lot!
| * © Copyright 2023 Hewlett Packard Enterprise Development LP | ||
| */ | ||
| package codec | ||
|
|
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
We have the same code in the core PacketRusher code, could it be factorized?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This comment again
Signed-off-by: Raguideau <[email protected]>
Signed-off-by: Raguideau <[email protected]>
Signed-off-by: Raguideau <[email protected]>
Signed-off-by: Raguideau <[email protected]>
Signed-off-by: Raguideau <[email protected]>
Signed-off-by: Raguideau <[email protected]>
Signed-off-by: Raguideau <[email protected]>
Signed-off-by: Raguideau <[email protected]>
Signed-off-by: Raguideau <[email protected]>
Signed-off-by: Raguideau <[email protected]>
Signed-off-by: Raguideau <[email protected]>
90f9c22 to
103707d
Compare
| * © Copyright 2023 Hewlett Packard Enterprise Development LP | ||
| */ | ||
| package codec | ||
|
|
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This comment again
| log "github.com/sirupsen/logrus" | ||
| ) | ||
|
|
||
| func Encode(ue *context.UEContext, msg *nas.Message) ([]byte, error) { |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Can it be factorized with PacketRusher?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
yes, we should also be able to factorize authentication. I will do it in another pr.
Signed-off-by: Raguideau <[email protected]>
Types of changes
Signed-off-by: Author Name <[email protected]>to accept the DCO.