## know how tools## know how gathering informtation
## know how recon tools
## know how tools enumeration
## know how enumeration toolsAutoRecon AutoRecon is a multi-threaded network reconnaissance tool which performs automated enumeration of services. It is intended as a time-saving tool for use in CTFs and other penetration testing environments (e.g. OSCP). It may also be useful in real-world engagements.
## know how smb tools
## know how samba toolsEnum4linux Enum4linux is a tool for enumerating information from Windows and Samba systems.
## web scanner
## web scanner install
know how vpn windows --> openvpn comunity
sudo apt-get install libwebkitgtk-1.0 default-jdk unzip
## errors
# Unrecognized VM option 'PermSize=128m'
# delete from vega.ini
-XX:PermSize=128m
-XX:MaxPermSize=256m
2.Next execute the follow commands:
apt-get install libwebkitgtk-1.0
apt-get install libwebkitgtk-1.0-common
apt-get install libwebkitgtk-1.0-0
## know how tools ewpt ewptx oscphttpx httpx is a fast and multi-purpose HTTP toolkit that allows running multiple probes using the retryablehttp library
Nuclei is used to send requests across targets based on a template, leading to zero false positives and providing fast scanning on a large number of hosts. Nuclei offers scanning for a variety of protocols, including TCP, DNS, HTTP, SSL, File, Whois, Websocket, Headless etc. With powerful and flexible templating, Nuclei can be used to model all kinds of security checks.
Fuxploider is an open source penetration testing tool that automates the process of detecting and exploiting file upload forms flaws. This tool is able to detect the file types allowed to be uploaded and is able to detect which technique will work best to upload web shells or any malicious file on the desired web server.
ffuf: Fast web fuzzer
## know how oscp tool
## know how gathering subdomains
ffuf -u "https://FUZZ.fullledcolor.es" -w SecLists/Discovery/Web-Content/raft-large-words.txt
## know how gathering directories
ffuf -u "https://fullledcolor.es/FUZZ" -w SecLists/Discovery/Web-Content/raft-large-words.txt
## know how gathering files php
ffuf -u "https://fullledcolor.es/FUZZ" -w SecLists/Discovery/Web-Content/raft-large-words.txt -e .php
## know how gathering files php not show 404
ffuf -u "https://fullledcolor.es/FUZZ" -w SecLists/Discovery/Web-Content/raft-large-words.txt -e .php -fc 404
# Directory discovery
ffuf -w /path/to/wordlist -u https://target/FUZZ
# Adding classical header (some WAF bypass)
ffuf -c -w "/opt/host/main.txt:FILE" -H "X-Originating-IP: 127.0.0.1, X-Forwarded-For: 127.0.0.1, X-Remote-IP: 127.0.0.1, X-Remote-Addr: 127.0.0.1, X-Client-IP: 127.0.0.1" -fs 5682,0 -u https://target/FUZZ
# match all responses but filter out those with content-size 42
ffuf -w wordlist.txt -u https://example.org/FUZZ -mc all -fs 42 -c -v
# Fuzz Host-header, match HTTP 200 responses.
ffuf -w hosts.txt -u https://example.org/ -H "Host: FUZZ" -mc 200
# Virtual host discovery (without DNS records)
ffuf -w /path/to/vhost/wordlist -u https://target -H "Host: FUZZ" -fs 4242
# Playing with threads and wait
./ffuf -u https://target/FUZZ -w /home/mdayber/Documents/Tools/Wordlists/WebContent_Discovery/content_discovery_4500.txt -c -p 0.1 -t 10
# GET param fuzzing, filtering for invalid response size (or whatever)
ffuf -w /path/to/paramnames.txt -u https://target/script.php?FUZZ=test_value -fs 4242
# GET parameter fuzzing if the param is known (fuzzing values) and filtering 401
ffuf -w /path/to/values.txt -u https://target/script.php?valid_name=FUZZ -fc 401
# POST parameter fuzzing
ffuf -w /path/to/postdata.txt -X POST -d "username=admin\&password=FUZZ" -u https://target/login.php -fc 401
# Fuzz POST JSON data. Match all responses not containing text "error".
ffuf -w entries.txt -u https://example.org/ -X POST -H "Content-Type: application/json" \
-d '{"name": "FUZZ", "anotherkey": "anothervalue"}' -fr "error"Ferobuxter A simple, fast, recursive content discovery tool written in Rust Sublist3r Fast Subdomains Enumeration Tool for Penetration Testers
Sublist3r is a python tool designed to enumerate subdomains of websites using OSINT. It helps penetration testers and bug hunters collect and gather subdomains for the domain they are targeting. Sublist3r enumerates subdomains using many search engines such as Google, Yahoo, Bing, Baidu, and Ask. Sublist3r also enumerates subdomains using Netcraft, Virustotal, ThreatCrowd, DNSdumpster, and ReverseDNS.
To list all the basic options and switches use -h switch:
python sublist3r.py -h
To enumerate subdomains of specific domain:
python sublist3r.py -d example.com
To enumerate subdomains of specific domain and show only subdomains which have open ports 80 and 443 :
python sublist3r.py -d example.com -p 80,443
To enumerate subdomains of specific domain and show the results in realtime:
python sublist3r.py -v -d example.com
To enumerate subdomains and enable the bruteforce module:
python sublist3r.py -b -d example.com
To enumerate subdomains and use specific engines such Google, Yahoo and Virustotal engines
python sublist3r.py -e google,yahoo,virustotal -d example.comBurp Suite Professional: Toolkit to automate, find and assist web vulnerability discovery and exploitation
sqlmap: Automatic SQL injection and database takeover tool
Frida: Dynamic instrumentation toolkit to intercept and debug software that is closed-source or locked down
APKLab: Set of scripts and tools to perform Reverse Engineering on Android applications
## know how mimikatz windows
## know how windows enumeration mimikatz
## knnow how enumeration windows mimiktazmimikatz: Windows x32/x64 program to extract passwords, hash, PINs, and Kerberos tickets from memory
Rubeus: Toolset for raw Kerberos interaction and abuses
Metasploit: Framework to help launching and developing exploits and offensive tasks
Ghidra: Software Reverse Engineering (SRE) suite of tools developed by NSA's Research Directorate
John the Ripper: Password recovery tool
hashcat: Fast, efficient and versatile hacking tool that assists offline brute-force attacks
Wireshark: Network protocol analyzer
Aircrack-ng: Suite of tools to assess WiFi network security
ngrok: Cross-platform application that exposes local server ports to the Internet
Covenant: .NET command and control framework
Nmap: Utility for network discovery and security auditing
Vega: Web security scanner and web security testing platform that helps validate SQLi, XSS, etc.
x64dbg: Open-source x64/x32 debugger for Windows
WinDbg: Windows default debugger that we use for kernel debugging
Hereby, I’m presenting HackTools, a firefox/chrome extension that summarizes useful commands and helps to build a payload after choosing the required parameters. It might be very useful in a penetration testing engagement.
convert ip for evading waff hackvector.co.ku (multi tools evasion waf)
aaencode tools javascript evasion jjencode tools javascript evasion jsfuck tools javascript evasion
js compresor evading waf js yui compresor evading waf
OpenVAS: Full-featured vulnerability scanner
## know how xss toolshttps://github.com/hahwul/dalfox xsscrapy xsser brutexss xssstrike BeEF: The Browser Exploitation Framework, a penetration testing tool that focuses on the web browser
## know how tools phising
## know how tools clone website
## know how clone website toolsSet social engineer toolkit site cloner
use urlcrazy to get similar domains.
Metasploit --> use auxiliary/server/capture/http_javascript_keylogger
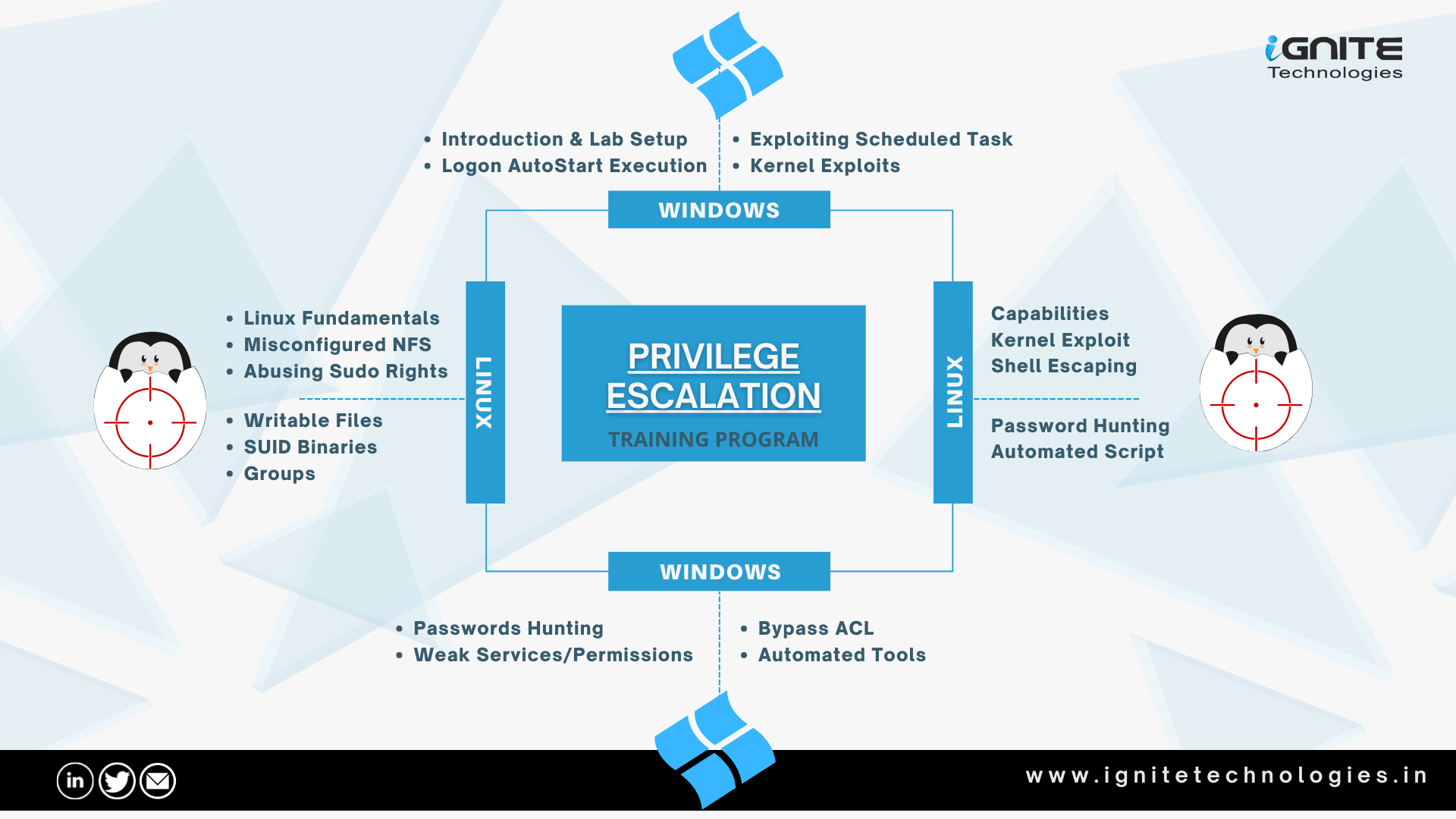
checklist linux privilege escalation
Linux Exploit Suggester LES tool is designed to assist in detecting security deficiencies for given Linux kernel/Linux-based machine. It provides following functionality
Linux Exploit Suggester 2 Next-generation exploit suggester based on Linux_Exploit_Suggester
pspy unprivileged linux process snooping pspy is a command line tool designed to snoop on processes without need for root permissions. It allows you to see commands run by other users, cron jobs, etc. as they execute. Great for enumeration of Linux systems in CTFs. Also great to demonstrate your colleagues why passing secrets as arguments on the command line is a bad idea.
subinACL powersploit powerup.ps1 Winpeas powerup muestra los vectores Priv Esc de Windows en función de las configuraciones incorrectas del sistema. DO NOT use the auto-exploit modules windows exploit suggester This tool compares a targets patch levels against the Microsoft vulnerability database in order to detect potential missing patches on the target. It also notifies the user if there are public exploits and Metasploit modules available for the missing bulletins. sherlck watson Watson is a .NET tool designed to enumerate missing KBs and suggest exploits for Privilege Escalation vulnerabilities. jaws JAWS is PowerShell script designed to help penetration testers (and CTFers) quickly identify potential privilege escalation vectors on Windows systems. It is written using PowerShell 2.0 so 'should' run on every Windows version since Windows 7 SharpUp is a C# port of various PowerUp functionality. Currently, only the most common checks have been ported; no weaponization functions have yet been implemented. psexec PsExec's most powerful uses include launching interactive command-prompts on remote systems and remote-enabling tools like IpConfig that otherwise do not have the ability to show information about remote systems.
Methodology unquoted privilege escalation windows1. AlwaysInstallElevated 2. SeBackupPrivilege 3. DnsAdmins to DomainAdmin 4. SeImpersonatePrivilege 5. HiveNightmare 6. Logon Autostart Execution (Registry Run Keys) 7. Boot Logon Autostart Execution (Startup Folder) 8. Stored Credentials (Runas) 9. Weak Registry Permission 10. Unquoted Service Path 11. Insecure GUI Application 12. Weak Service Permissions 13. Scheduled Task/Job (T1573.005) 14. Kernel Exploit 15. SamAccountSpoofing (CVE-2021–42278) 16. SpoolFool 17. PrintNightmare 18. Server Operator Group
- Abusing Sudo Rights
- SUID Binaries
- Capabilities
- Lxd Privilege Escalation
- Docker Privilege Escalation
- Exploiting Cron jobs
- Writable /etc/passwd File
- Misconfigured NFS
- Exploiting Wildcard
- LD_Preload Privilege Escalation
- Exploiting PATH Variable
- Python Library Hijacking
- Polkit (CVE 2021-3560)
- PwnKit (CVE 2021-4034)
- DirtyPipe (CVE 2022-0847)
oscp
bloodhound : muestra una imagen del entorno de AD
powerview permite la enumeración de un entorno AD
PowerShell Empire Empire is a post-exploitation framework that includes a pure-PowerShell2.0 Windows agent, and a pure Python 2.6/2.7 Linux/OS X agent
Covenant Covenant is a .NET command and control framework that aims to highlight the attack surface of .NET, make the use of offensive .NET tradecraft easier, and serve as a collaborative command and control platform for red teamers.
Rubeus Rubeus is a C# toolset for raw Kerberos interaction and abuses
Responder (Poisoning and Spoofing are not allowed in the labs or on the exam)
Compromised both external-facing Active Directory sets in the OSCP lab environment. TryHackMe — Active Directory Basics (for subscribers only) TryHackMe — Attacktive Directory TryHackMe — Post-Exploitation Basics TryHackMe — Attacking Kerberos (for subscribers only)
[+] Complete the TryHackMe Offensive Pentesting track — This is something you will have to pay for, but it isn’t required. I do recommend it to all novice hackers preparing for the OSCP Exam. Also, you’ll need it if you want to do the TryHackMe labs marked with a [$] below. Complete the Course Exercises — Offensive Security has received a lot of hate about the lab environment. A lot of the feedback calls it “dated” and complains that it bears no similarities to the exam. I disagree. While yes, it is not like the exam (nor should it be!), it will provide you with a variety of targets that allow you to develop your own methodology.