-
-
Notifications
You must be signed in to change notification settings - Fork 5.5k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Debian apt package & yum package registry #20751
Comments
|
https://github.com/esell/deb-simple has implemented it. |
|
Hey! I've had a go at this but it needs a lot of work, primarily on its design. https://github.com/awkwardbunny/gitea/tree/feature-apt I also wanted to discuss some designs, as the way it works right now uses files/directories created in the application data path, which is probably not desirable. The files are uploaded and deleted through The Packages/Releases files are generated in I wasn't really sure how best to structure this; mainly where to store the generated files as it might be take too much to generate everything each request and didn't want to muck up the database by having it's own table for Debian package repo. The code may be trash, but I was hoping someone would find it useful if they want to use it for reference or fix it up. |
|
@awkwardbunny this is so amazing! Thank you! |
|
@awkwardbunny Thank you for your work!
Yes, the files need to use the existing package storage to benefit from deduplication and all other features. So far I implemented 17 different package registries and they all could be mapped to my schema. This should work for Debian packages too.
I did not much research for Debian packages but my thought was to store the signing key(s) as user/system setting or secret. This leads to the next question. Should every user have its own signing key? Are there disadvantages to share a global/system-wide key for multiple user registries? Currently I think one key should be enough.
Not trash at all. I usually need one or two weeks per package type. I spend most of the time researching / reverse engineering how the protocol works and such stuff. Your code is a great starting point. If you don't mind I would adopt your branch and finish it. |
The actual packages are stored using the packages service like the other packages types (I used your code for reference). The thing that makes it hard/annoying for a Debian repo is that it is split by architecture first, and then name (docs). On top of that, managing versions can also be difficult. In my code, (it's a little hacky) it stores the version and arch as part of the filename (packagename_version_arch.deb) as well as the version in the package registry.
I actually did initially add a settings page for signing key. However, I didn't want to muck up the settings, and for simplicity, opted to just read from the key files just for proof-of-concept. I believe there is one signing key for a repo (Debian repo, not git repo). I initially tried to use the user GPG keys but (1) it's per-user keys and (2) only stores public keys, which cannot be used for signing. This does bring up another point. A single Debian repository is usually split into [distro]/[component/section]/[architecture].
Thanks and awesome! |
|
I added the RPM package registry in #23380. |
Co-authored-by: @awkwardbunny This PR adds a Debian package registry. You can follow [this tutorial](https://www.baeldung.com/linux/create-debian-package) to build a *.deb package for testing. Source packages are not supported at the moment and I did not find documentation of the architecture "all" and how these packages should be treated. 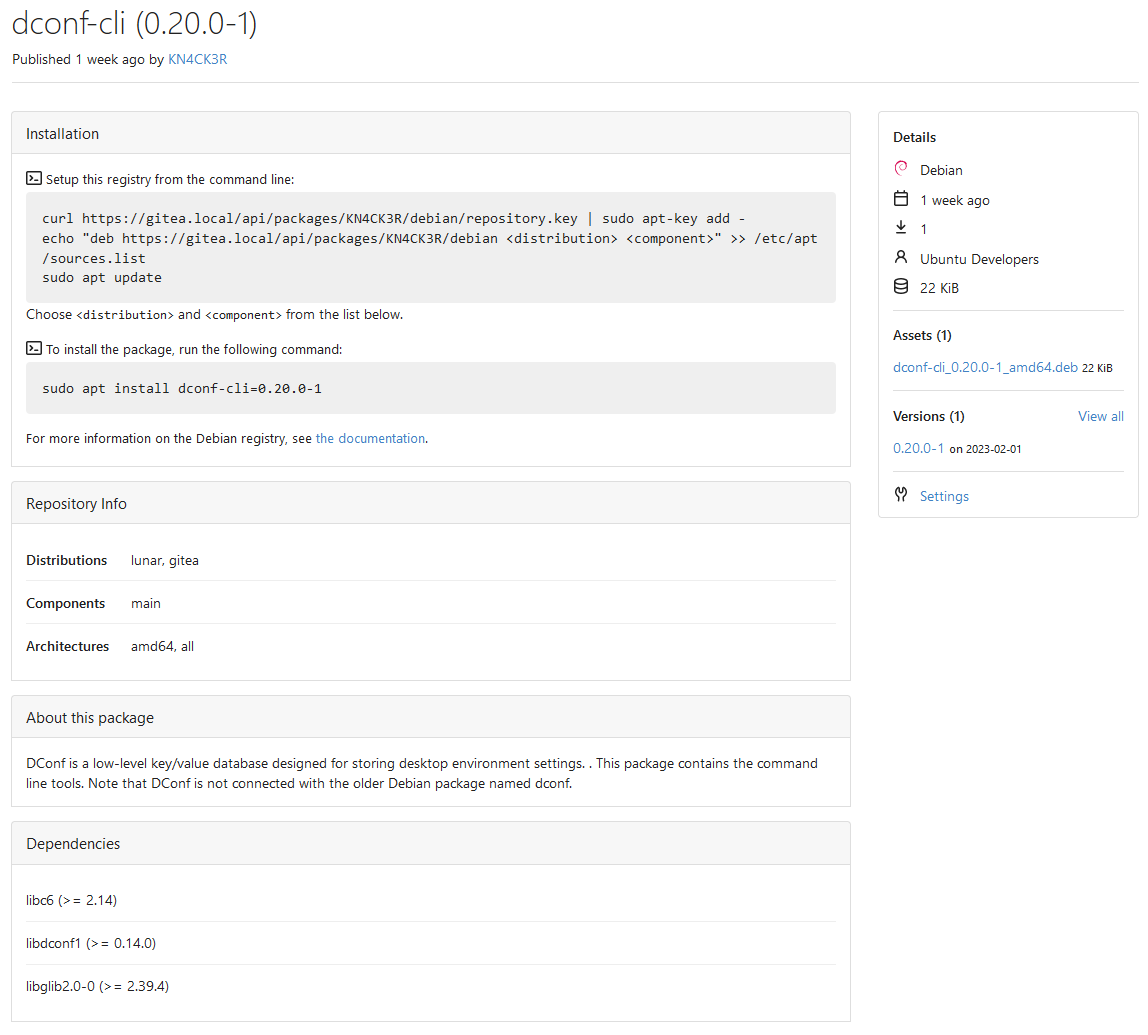 Part of #20751. Revised copy of #22854. --------- Co-authored-by: Brian Hong <[email protected]> Co-authored-by: techknowlogick <[email protected]> Co-authored-by: Giteabot <[email protected]>
Fixes #20751 This PR adds a RPM package registry. You can follow [this tutorial](https://opensource.com/article/18/9/how-build-rpm-packages) to build a *.rpm package for testing. This functionality is similar to the Debian registry (#22854) and therefore shares some methods. I marked this PR as blocked because it should be merged after #22854. 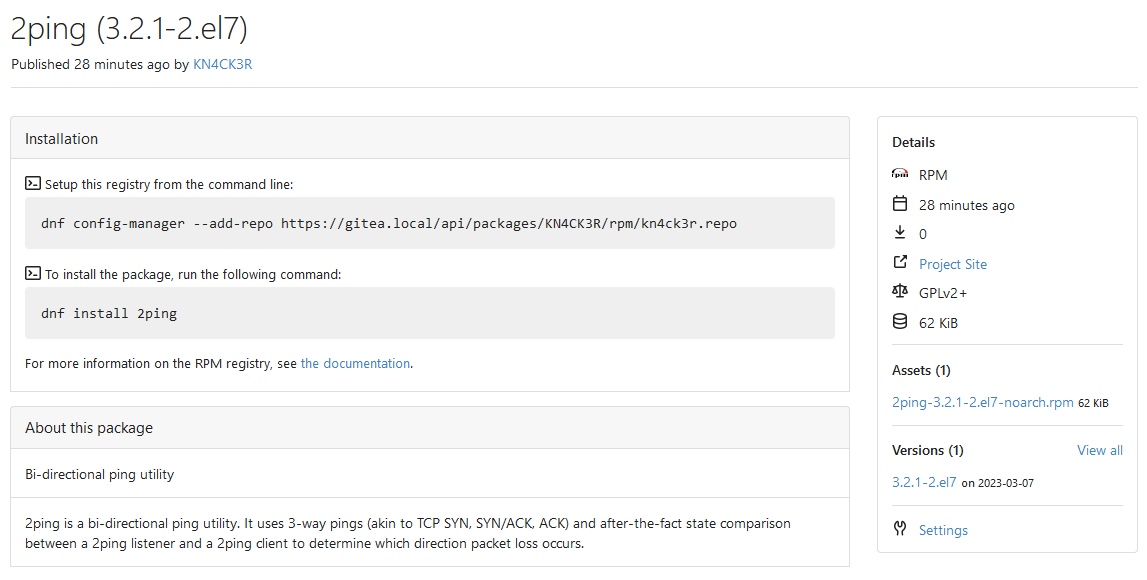
It would be great to support debian apt package registry and yum package registry.
The text was updated successfully, but these errors were encountered: