diff --git a/Packs/ArcherRSA/Playbooks/playbook-Archer_initiate_incident.yml b/Packs/ArcherRSA/Playbooks/playbook-Archer_initiate_incident.yml
index 1bb56d2891ff..ca59a255bd38 100644
--- a/Packs/ArcherRSA/Playbooks/playbook-Archer_initiate_incident.yml
+++ b/Packs/ArcherRSA/Playbooks/playbook-Archer_initiate_incident.yml
@@ -2,8 +2,10 @@ id: Archer initiate incident
version: -1
name: Archer initiate incident
fromversion: "5.0.0"
+deprecated: true
starttaskid: "0"
-description: "initiate Archer incident"
+description: "Deprecated. Use the `archer-get-file` command directly instead.
+initiate Archer incident"
tasks:
"0":
id: "0"
diff --git a/Packs/ArcherRSA/Playbooks/playbook-Archer_initiate_incident_README.md b/Packs/ArcherRSA/Playbooks/playbook-Archer_initiate_incident_README.md
index 1f887c2fccbf..19617781f931 100644
--- a/Packs/ArcherRSA/Playbooks/playbook-Archer_initiate_incident_README.md
+++ b/Packs/ArcherRSA/Playbooks/playbook-Archer_initiate_incident_README.md
@@ -1,28 +1,38 @@
-Initiates an Archer incident.
+Deprecated. Use the `archer-get-file` command directly instead.
+initiate Archer incident
## Dependencies
+
This playbook uses the following sub-playbooks, integrations, and scripts.
-## Sub-playbooks
+### Sub-playbooks
+
This playbook does not use any sub-playbooks.
-## Integrations
+### Integrations
+
* RSA Archer
-## Scripts
+### Scripts
+
This playbook does not use any scripts.
-## Commands
+### Commands
+
* archer-get-file
## Playbook Inputs
+
---
There are no inputs for this playbook.
## Playbook Outputs
+
---
There are no outputs for this playbook.
## Playbook Image
+
---
-
+
+
diff --git a/Packs/ArcherRSA/ReleaseNotes/1_2_12.md b/Packs/ArcherRSA/ReleaseNotes/1_2_12.md
new file mode 100644
index 000000000000..ae86c99e9258
--- /dev/null
+++ b/Packs/ArcherRSA/ReleaseNotes/1_2_12.md
@@ -0,0 +1,6 @@
+
+#### Playbooks
+
+##### Archer initiate incident
+
+Deprecated. Use the ***archer-get-file*** command directly instead.
diff --git a/Packs/ArcherRSA/doc_files/Archer_initiate_incident.png b/Packs/ArcherRSA/doc_files/Archer_initiate_incident.png
new file mode 100644
index 000000000000..b2b533353588
Binary files /dev/null and b/Packs/ArcherRSA/doc_files/Archer_initiate_incident.png differ
diff --git a/Packs/ArcherRSA/pack_metadata.json b/Packs/ArcherRSA/pack_metadata.json
index cd12e753f124..b54f1ee6846b 100644
--- a/Packs/ArcherRSA/pack_metadata.json
+++ b/Packs/ArcherRSA/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "RSA Archer",
"description": "The RSA Archer GRC Platform provides a common foundation for managing policies, controls, risks, assessments and deficiencies across lines of business.",
"support": "xsoar",
- "currentVersion": "1.2.11",
+ "currentVersion": "1.2.12",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/CommonPlaybooks/Playbooks/playbook-Block_Account_-_Generic_v2.yml b/Packs/CommonPlaybooks/Playbooks/playbook-Block_Account_-_Generic_v2.yml
index ff2c9b0a7875..6060f40c110a 100644
--- a/Packs/CommonPlaybooks/Playbooks/playbook-Block_Account_-_Generic_v2.yml
+++ b/Packs/CommonPlaybooks/Playbooks/playbook-Block_Account_-_Generic_v2.yml
@@ -160,8 +160,8 @@ tasks:
id: 6c4b8a60-449b-4710-89e8-a68c32fdda28
version: -1
name: PAN-OS - Register Tag to User
- description: Apply a tag to a user.
- script: "|||panorama-register-user-tag"
+ description: Registers users to a tag. This command is only available for PAN-OS version 9.x and above.
+ script: '|||pan-os-register-user-tag'
type: regular
iscommand: true
brand: ""
@@ -170,10 +170,14 @@ tasks:
- "2"
scriptarguments:
Users:
- simple: ${Blocklist.Final}
+ complex:
+ root: Blocklist
+ accessor: Final
tag:
- simple: ${inputs.Tag}
+ complex:
+ root: inputs.Tag
separatecontext: false
+ continueonerrortype: ""
view: |-
{
"position": {
diff --git a/Packs/CommonPlaybooks/Playbooks/playbook-Block_Account_-_Generic_v2_README.md b/Packs/CommonPlaybooks/Playbooks/playbook-Block_Account_-_Generic_v2_README.md
index 40c463f4ba12..47ec37fbcb63 100644
--- a/Packs/CommonPlaybooks/Playbooks/playbook-Block_Account_-_Generic_v2_README.md
+++ b/Packs/CommonPlaybooks/Playbooks/playbook-Block_Account_-_Generic_v2_README.md
@@ -3,28 +3,41 @@ This playbook blocks malicious usernames using all integrations that you have en
Supported integrations for this playbook:
* Active Directory
* PAN-OS - This requires PAN-OS 9.1 or higher.
+* SailPoint
+* PingOne
+* AWS IAM
+* Clarizen IAM
+* Envoy IAM
+* ExceedLMS IAM
+* Okta
## Dependencies
+
This playbook uses the following sub-playbooks, integrations, and scripts.
### Sub-playbooks
+
This playbook does not use any sub-playbooks.
### Integrations
+
* Active Directory Query v2
### Scripts
+
* SetAndHandleEmpty
* IsIntegrationAvailable
### Commands
-* panorama-register-user-tag
-* pingone-deactivate-user
+
+* iam-disable-user
* identityiq-disable-account
+* pingone-deactivate-user
+* pan-os-register-user-tag
* ad-disable-account
-* iam-disable-user
## Playbook Inputs
+
---
| **Name** | **Description** | **Default Value** | **Required** |
@@ -35,6 +48,7 @@ This playbook does not use any sub-playbooks.
| UserVerification | Possible values:True/False. Default:True.
Specify if User Verification is Requrired | True | Optional |
## Playbook Outputs
+
---
| **Path** | **Description** | **Type** |
@@ -42,5 +56,7 @@ This playbook does not use any sub-playbooks.
| Blocklist.Final | Blocked accounts | unknown |
## Playbook Image
+
---
-
\ No newline at end of file
+
+
diff --git a/Packs/CommonPlaybooks/ReleaseNotes/2_3_71.md b/Packs/CommonPlaybooks/ReleaseNotes/2_3_71.md
new file mode 100644
index 000000000000..0ae5ffd54345
--- /dev/null
+++ b/Packs/CommonPlaybooks/ReleaseNotes/2_3_71.md
@@ -0,0 +1,4 @@
+#### Playbooks
+
+##### Block Account - Generic v2
+Updated deprecated command from ***panorama-register-user-tag*** to ***pan-os-register-user-tag***.
\ No newline at end of file
diff --git a/Packs/CommonPlaybooks/pack_metadata.json b/Packs/CommonPlaybooks/pack_metadata.json
index 77d635c509a3..3210ddd5c9e4 100644
--- a/Packs/CommonPlaybooks/pack_metadata.json
+++ b/Packs/CommonPlaybooks/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Common Playbooks",
"description": "Frequently used playbooks pack.",
"support": "xsoar",
- "currentVersion": "2.3.70",
+ "currentVersion": "2.3.71",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Execute_snippet_code_script.yml b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Execute_snippet_code_script.yml
index 6b8035d8e332..f4524e44739c 100644
--- a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Execute_snippet_code_script.yml
+++ b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Execute_snippet_code_script.yml
@@ -1,4 +1,5 @@
-description: Initiates a new endpoint script execution action using the provided snippet
+deprecated: true
+description: Deprecated. Use the `xdr-snippet-code-script-execute` command instead. Initiates a new endpoint script execution action using the provided snippet
code and retrieves the file results.
id: Cortex XDR - Execute snippet code script
inputs:
diff --git a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Execute_snippet_code_script_README.md b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Execute_snippet_code_script_README.md
index d44ab61394cb..aa4010ba0f0b 100644
--- a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Execute_snippet_code_script_README.md
+++ b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Execute_snippet_code_script_README.md
@@ -1,23 +1,28 @@
-Initiates a new endpoint script execution action using the provided snippet code and retrieve the file results.
-
+Deprecated. Use the `xdr-snippet-code-script-execute` command instead. Initiates a new endpoint script execution action using the provided snippet code and retrieves the file results.
## Dependencies
+
This playbook uses the following sub-playbooks, integrations, and scripts.
### Sub-playbooks
-Cortex XDR - Check Action Status
+
+* Cortex XDR - Check Action Status
### Integrations
-CortexXDRIR
+
+* CortexXDRIR
### Scripts
+
This playbook does not use any scripts.
### Commands
+
* xdr-get-script-execution-results
* xdr-run-snippet-code-script
## Playbook Inputs
+
---
| **Name** | **Description** | **Default Value** | **Required** |
@@ -26,6 +31,7 @@ This playbook does not use any scripts.
| snippet_code | Section of a script you want to initiate on an endpoint \(e.g., print\("7"\)\). | | Optional |
## Playbook Outputs
+
---
| **Path** | **Description** | **Type** |
@@ -33,5 +39,7 @@ This playbook does not use any scripts.
| PaloAltoNetworksXDR.ScriptResult.results._return_value | Value returned by the script in case the type is not a dictionary. | unknown |
## Playbook Image
+
---
-
+
+
diff --git a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_True_Positive_Incident_Handling.yml b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_True_Positive_Incident_Handling.yml
index b4be141b7ad0..87d2497ce7aa 100644
--- a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_True_Positive_Incident_Handling.yml
+++ b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_True_Positive_Incident_Handling.yml
@@ -996,54 +996,6 @@ tasks:
}
}
continueonerrortype: ""
- '71':
- id: '71'
- ignoreworker: false
- isautoswitchedtoquietmode: false
- isoversize: false
- loop:
- exitCondition: ''
- iscommand: false
- max: 0
- wait: 1
- nexttasks:
- '#none#':
- - '64'
- note: false
- quietmode: 0
- scriptarguments:
- endpoint_id:
- simple: ${inputs.HostID}
- file_path:
- complex:
- root: Confirm which File Path will be deleted.Answers
- accessor: "0"
- transformers:
- - operator: uniq
- polling_timeout:
- simple: '10'
- separatecontext: true
- skipunavailable: false
- task:
- brand: ''
- description: Initiates a new endpoint script execution to delete the specified file and retrieve the results.
- id: 480bc329-81ff-4f7e-8f55-977b58dda775
- iscommand: false
- name: Cortex XDR - delete file
- type: playbook
- version: -1
- playbookName: Cortex XDR - delete file
- taskid: 480bc329-81ff-4f7e-8f55-977b58dda775
- timertriggers: []
- type: playbook
- view: |-
- {
- "position": {
- "x": -2030,
- "y": 580
- }
- }
- continueonerrortype: ""
'72':
id: '72'
ignoreworker: false
@@ -1209,7 +1161,7 @@ tasks:
'#default#':
- '64'
yes:
- - '71'
+ - '91'
note: false
quietmode: 0
separatecontext: false
@@ -1625,7 +1577,8 @@ tasks:
- "88"
scriptarguments:
entryIDs:
- simple: ${lastCompletedTaskEntries}
+ complex:
+ root: lastCompletedTaskEntries
tags:
simple: Found additional assets
separatecontext: false
@@ -1761,15 +1714,21 @@ tasks:
QRadarTimeFrame:
simple: LAST 7 DAYS
SHA1:
- simple: ${Specify IOCs to hunt upon.Answers.2}
+ complex:
+ root: Specify IOCs to hunt upon.Answers
+ accessor: "2"
SHA256:
- simple: ${Specify IOCs to hunt upon.Answers.1}
+ complex:
+ root: Specify IOCs to hunt upon.Answers
+ accessor: "1"
SplunkEarliestTime:
simple: -7d@d
SplunkLatestTime:
simple: now
URLDomain:
- simple: ${Specify IOCs to hunt upon.Answers.4}
+ complex:
+ root: Specify IOCs to hunt upon.Answers
+ accessor: "4"
separatecontext: true
continueonerrortype: ""
loop:
@@ -1791,7 +1750,51 @@ tasks:
quietmode: 0
isoversize: false
isautoswitchedtoquietmode: false
-version: -1
+ "91":
+ id: "91"
+ taskid: c79fa8ce-3da8-424b-865d-e1994c3ea043
+ type: regular
+ task:
+ id: c79fa8ce-3da8-424b-865d-e1994c3ea043
+ version: -1
+ name: xdr-file-delete-script-execute
+ description: Initiates a new endpoint script execution to delete the specified
+ file.
+ script: Cortex XDR - IR|||xdr-file-delete-script-execute
+ type: regular
+ iscommand: true
+ brand: Cortex XDR - IR
+ nexttasks:
+ '#none#':
+ - "64"
+ scriptarguments:
+ endpoint_ids:
+ complex:
+ root: inputs.HostID
+ file_path:
+ complex:
+ root: Confirm which File Path will be deleted.Answers
+ accessor: "0"
+ transformers:
+ - operator: uniq
+ timeout_in_seconds:
+ simple: "600"
+ separatecontext: false
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": -2030,
+ "y": 580
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
view: |-
{
"linkLabelsPosition": {},
@@ -1804,6 +1807,7 @@ view: |-
}
}
}
+version: -1
tests:
- Test XDR Playbook
fromversion: 6.5.0
diff --git a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_True_Positive_Incident_Handling_README.md b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_True_Positive_Incident_Handling_README.md
index 50f122744d55..a4be51b8709d 100644
--- a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_True_Positive_Incident_Handling_README.md
+++ b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_True_Positive_Incident_Handling_README.md
@@ -8,26 +8,27 @@ This playbook uses the following sub-playbooks, integrations, and scripts.
### Sub-playbooks
* Threat Hunting - Generic
-* Cortex XDR - delete file
* Cortex XDR - Isolate Endpoint
### Integrations
* CortexXDRIR
+* Cortex XDR - IR
### Scripts
+* AddEvidence
* ServiceNowCreateIncident
* IsIntegrationAvailable
-* AddEvidence
### Commands
-* closeInvestigation
-* jira-create-issue
* setIncident
+* jira-create-issue
* xdr-blocklist-files
+* closeInvestigation
* setIndicators
+* xdr-file-delete-script-execute
## Playbook Inputs
diff --git a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_check_file_existence.yml b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_check_file_existence.yml
index 1baa152f4204..9c6e054c0507 100644
--- a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_check_file_existence.yml
+++ b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_check_file_existence.yml
@@ -1,5 +1,6 @@
+deprecated: true
description: |
- Initiates a new endpoint script execution to check if the file exists and retrieve the results.
+ Deprecated. Use `xdr-file-exist-script-execute` command instead. Initiates a new endpoint script execution to check if the file exists and retrieve the results.
id: Cortex XDR - check file existence
inputs:
- description: 'A comma-separated list of endpoint IDs. '
diff --git a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_check_file_existence_README.md b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_check_file_existence_README.md
index 6df8aea47ec7..e8d529443143 100644
--- a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_check_file_existence_README.md
+++ b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_check_file_existence_README.md
@@ -1,23 +1,29 @@
-Initiates a new endpoint script execution to check if the file exists and retrieve the results.
+Deprecated. Use `xdr-file-exist-script-execute` command instead. Initiates a new endpoint script execution to check if the file exists and retrieve the results.
## Dependencies
+
This playbook uses the following sub-playbooks, integrations, and scripts.
### Sub-playbooks
+
* Cortex XDR - Check Action Status
### Integrations
+
* CortexXDRIR
### Scripts
+
This playbook does not use any scripts.
### Commands
+
* xdr-run-script-file-exists
* xdr-get-script-execution-results
## Playbook Inputs
+
---
| **Name** | **Description** | **Default Value** | **Required** |
@@ -28,6 +34,7 @@ This playbook does not use any scripts.
| polling_timeout | Amount of time to poll action status before declaring a timeout and resuming the playbook \(in minutes\). | 10 | Optional |
## Playbook Outputs
+
---
| **Path** | **Description** | **Type** |
@@ -35,5 +42,7 @@ This playbook does not use any scripts.
| PaloAltoNetworksXDR.ScriptResult.results._return_value | Value returned by the script in case the type is not a dictionary. | boolean |
## Playbook Image
+
---
-
\ No newline at end of file
+
+
diff --git a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_delete_file.yml b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_delete_file.yml
index 4e1cd627374d..18ff7d7bb436 100644
--- a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_delete_file.yml
+++ b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_delete_file.yml
@@ -1,4 +1,5 @@
-description: Initiates a new endpoint script execution to delete the specified file
+deprecated: true
+description: Deprecated. Use the `xdr-file-delete-script-execute` command instead. Initiates a new endpoint script execution to delete the specified file
and retrieve the results.
id: Cortex XDR - delete file
inputs:
diff --git a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_delete_file_README.md b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_delete_file_README.md
index d88367f52155..477ad33890cc 100644
--- a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_delete_file_README.md
+++ b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_delete_file_README.md
@@ -1,22 +1,28 @@
-Initiates a new endpoint script execution to delete the specified file and retrieve the results.
+Deprecated. Use the `xdr-file-delete-script-execute` command instead. Initiates a new endpoint script execution to delete the specified file and retrieve the results.
## Dependencies
+
This playbook uses the following sub-playbooks, integrations, and scripts.
### Sub-playbooks
+
* Cortex XDR - Check Action Status
### Integrations
+
* CortexXDRIR
### Scripts
+
This playbook does not use any scripts.
### Commands
+
* xdr-get-script-execution-results
* xdr-run-script-delete-file
## Playbook Inputs
+
---
| **Name** | **Description** | **Default Value** | **Required** |
@@ -27,6 +33,7 @@ This playbook does not use any scripts.
| polling_timeout | Amount of time to poll action status before declaring a timeout and resuming the playbook \(in minutes\). | 10 | Optional |
## Playbook Outputs
+
---
| **Path** | **Description** | **Type** |
@@ -34,5 +41,7 @@ This playbook does not use any scripts.
| PaloAltoNetworksXDR.ScriptResult.results._return_value | Value returned by the script in case the type is not a dictionary. | unknown |
## Playbook Image
+
---
-
\ No newline at end of file
+
+
diff --git a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_execute_commands.yml b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_execute_commands.yml
index 0f73accf4cec..1f753a6d04d5 100644
--- a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_execute_commands.yml
+++ b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_execute_commands.yml
@@ -1,4 +1,5 @@
-description: Initiates a new script execution of shell commands.
+deprecated: true
+description: Deprecated. Use the `xdr-script-commands-execute` command instead. Initiates a new script execution of shell commands.
id: Cortex XDR - Execute commands
inputs:
- description: A comma-separated list of endpoint IDs.
diff --git a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_execute_commands_README.md b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_execute_commands_README.md
index 4fea78a309fa..f09ea50942a0 100644
--- a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_execute_commands_README.md
+++ b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_execute_commands_README.md
@@ -1,22 +1,28 @@
-Initiates a new script execution of shell commands.
+Deprecated. Use the `xdr-script-commands-execute` command instead. Initiates a new script execution of shell commands.
## Dependencies
+
This playbook uses the following sub-playbooks, integrations, and scripts.
### Sub-playbooks
+
* Cortex XDR - Check Action Status
### Integrations
+
* CortexXDRIR
### Scripts
+
This playbook does not use any scripts.
### Commands
-* xdr-get-script-execution-results
+
* xdr-run-script-execute-commands
+* xdr-get-script-execution-results
## Playbook Inputs
+
---
| **Name** | **Description** | **Default Value** | **Required** |
@@ -27,9 +33,12 @@ This playbook does not use any scripts.
| polling_timeout | Amount of time to poll action status before declaring a timeout and resuming the playbook \(in minutes\). | 10 | Optional |
## Playbook Outputs
+
---
There are no outputs for this playbook.
## Playbook Image
+
---
-
\ No newline at end of file
+
+
diff --git a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_kill_process.yml b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_kill_process.yml
index 89129d62077c..a436ce79e6f9 100644
--- a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_kill_process.yml
+++ b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_kill_process.yml
@@ -1,6 +1,7 @@
+deprecated: true
id: Cortex XDR - kill process
version: -1
-description: Initiates a new endpoint script execution kill process and retrieves
+description: Deprecated. Use the `xdr-kill-process-script-execute` command instead. Initiates a new endpoint script execution kill process and retrieves
the results.
inputs:
- description: 'A comma-separated list of endpoint IDs. '
diff --git a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_kill_process_README.md b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_kill_process_README.md
index abb0ef513679..a8736d0c2165 100644
--- a/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_kill_process_README.md
+++ b/Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_kill_process_README.md
@@ -1,22 +1,28 @@
-Initiates a new endpoint script execution kill process and retrieves the results.
+Deprecated. Use the `xdr-kill-process-script-execute` command instead. Initiates a new endpoint script execution kill process and retrieves the results.
## Dependencies
+
This playbook uses the following sub-playbooks, integrations, and scripts.
### Sub-playbooks
+
* Cortex XDR - Check Action Status
### Integrations
+
* CortexXDRIR
### Scripts
+
This playbook does not use any scripts.
### Commands
+
* xdr-run-script-kill-process
* xdr-get-script-execution-results
## Playbook Inputs
+
---
| **Name** | **Description** | **Default Value** | **Required** |
@@ -27,6 +33,7 @@ This playbook does not use any scripts.
| polling_timeout | Amount of time to poll action status before declaring a timeout and resuming the playbook \(in minutes\). | 10 | Optional |
## Playbook Outputs
+
---
| **Path** | **Description** | **Type** |
@@ -35,5 +42,7 @@ This playbook does not use any scripts.
| PaloAltoNetworksXDR.ScriptResult.results.standard_output | The STDOUT and the STDERR logged by the script during the execution. | unknown |
## Playbook Image
+
---
-
\ No newline at end of file
+
+
diff --git a/Packs/CortexXDR/ReleaseNotes/4_11_1.md b/Packs/CortexXDR/ReleaseNotes/4_11_1.md
new file mode 100644
index 000000000000..9a3a85c3b2d7
--- /dev/null
+++ b/Packs/CortexXDR/ReleaseNotes/4_11_1.md
@@ -0,0 +1,25 @@
+#### Playbooks
+
+##### Cortex XDR - Execute commands
+
+Deprecated. Use the *xdr-script-commands-execute* command instead.
+
+##### Cortex XDR - Execute snippet code script
+
+Deprecated. Use the *xdr-snippet-code-script-execute* command instead.
+
+##### Cortex XDR - check file existence
+
+Deprecated. Use the *xdr-file-exist-script-execute* command instead.
+
+##### Cortex XDR - delete file
+
+Deprecated. Use the *xdr-file-delete-script-execute* command instead.
+
+##### Cortex XDR - kill process
+
+Deprecated. Use the *xdr-kill-process-script-execute* command instead.
+
+##### Cortex XDR - True Positive Incident Handling
+
+Replaced `Cortex XDR - delete file (Deprecated)` sub-playbook with the *xdr-file-exist-script-execute* command.
\ No newline at end of file
diff --git a/Packs/CortexXDR/doc_files/Cortex_XDR_-_True_Positive_Incident_Handling.png b/Packs/CortexXDR/doc_files/Cortex_XDR_-_True_Positive_Incident_Handling.png
index 856f365108fd..f3e4d7a525e1 100644
Binary files a/Packs/CortexXDR/doc_files/Cortex_XDR_-_True_Positive_Incident_Handling.png and b/Packs/CortexXDR/doc_files/Cortex_XDR_-_True_Positive_Incident_Handling.png differ
diff --git a/Packs/CortexXDR/pack_metadata.json b/Packs/CortexXDR/pack_metadata.json
index dafb04e133c5..d2a3e87871d9 100644
--- a/Packs/CortexXDR/pack_metadata.json
+++ b/Packs/CortexXDR/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Cortex XDR by Palo Alto Networks",
"description": "Automates Cortex XDR incident response, and includes custom Cortex XDR incident views and layouts to aid analyst investigations.",
"support": "xsoar",
- "currentVersion": "4.11.0",
+ "currentVersion": "4.11.1",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/McAfee-TIE/Playbooks/playbook-Search_Endpoints_By_Hash_-_TIE.yml b/Packs/McAfee-TIE/Playbooks/playbook-Search_Endpoints_By_Hash_-_TIE.yml
index e92d66a1953f..16eed35aa740 100644
--- a/Packs/McAfee-TIE/Playbooks/playbook-Search_Endpoints_By_Hash_-_TIE.yml
+++ b/Packs/McAfee-TIE/Playbooks/playbook-Search_Endpoints_By_Hash_-_TIE.yml
@@ -102,86 +102,6 @@ tasks:
quietmode: 0
isoversize: false
isautoswitchedtoquietmode: false
- "2":
- id: "2"
- taskid: b098fed0-d1ae-418c-8a37-756e1ae0cb37
- type: condition
- task:
- id: b098fed0-d1ae-418c-8a37-756e1ae0cb37
- version: -1
- name: Is ePO enabled?
- description: Is ePO enabled?
- type: condition
- iscommand: false
- brand: ""
- nexttasks:
- '#default#':
- - "4"
- "yes":
- - "6"
- scriptarguments:
- value:
- complex:
- root: modules
- filters:
- - - operator: isEqualString
- left:
- value:
- simple: modules.brand
- iscontext: true
- right:
- value:
- simple: epo
- - - operator: isEqualString
- left:
- value:
- simple: modules.state
- iscontext: true
- right:
- value:
- simple: active
- separatecontext: false
- conditions:
- - label: "yes"
- condition:
- - - operator: isExists
- left:
- value:
- complex:
- root: modules
- filters:
- - - operator: isEqualString
- left:
- value:
- simple: modules.brand
- iscontext: true
- right:
- value:
- simple: epo
- - - operator: isEqualString
- left:
- value:
- simple: modules.state
- iscontext: true
- right:
- value:
- simple: active
- accessor: brand
- iscontext: true
- view: |-
- {
- "position": {
- "x": 470,
- "y": 1638
- }
- }
- note: false
- timertriggers: []
- ignoreworker: false
- skipunavailable: false
- quietmode: 0
- isoversize: false
- isautoswitchedtoquietmode: false
"3":
id: "3"
taskid: 26ba9604-ced2-4c35-8e13-075d3ed04042
@@ -190,11 +110,11 @@ tasks:
id: 26ba9604-ced2-4c35-8e13-075d3ed04042
version: -1
name: List all agents that the Hash has been executed on
- description: Get Agent GUIDS for the given hashes
- script: McAfee Threat Intelligence Exchange|||tie-file-references
+ description: Retrieves the set of systems which have referenced (typically executed) the specified hashes.
+ script: '|||tie-file-references'
type: regular
iscommand: true
- brand: McAfee Threat Intelligence Exchange
+ brand: ""
nexttasks:
'#none#':
- "5"
@@ -207,7 +127,7 @@ tasks:
{
"position": {
"x": 430,
- "y": 737
+ "y": 757
}
}
note: false
@@ -233,8 +153,8 @@ tasks:
view: |-
{
"position": {
- "x": 178,
- "y": 2143
+ "x": 162.5,
+ "y": 1693
}
}
note: false
@@ -281,43 +201,7 @@ tasks:
{
"position": {
"x": 430,
- "y": 910
- }
- }
- note: false
- timertriggers: []
- ignoreworker: false
- skipunavailable: false
- quietmode: 0
- isoversize: false
- isautoswitchedtoquietmode: false
- "6":
- id: "6"
- taskid: 101e3e85-0246-4bd4-80be-2df713ee96e6
- type: regular
- task:
- id: 101e3e85-0246-4bd4-80be-2df713ee96e6
- version: -1
- name: Get Agent info from ePO
- description: Get hostnames for the Agent GUIDS
- scriptName: EPOFindSystem
- type: regular
- iscommand: false
- brand: ""
- nexttasks:
- '#none#':
- - "4"
- scriptarguments:
- searchText:
- complex:
- root: File
- accessor: References.AgentGuid
- separatecontext: false
- view: |-
- {
- "position": {
- "x": 470,
- "y": 1937
+ "y": 920
}
}
note: false
@@ -343,6 +227,7 @@ tasks:
'#none#':
- "1"
separatecontext: false
+ continueonerrortype: ""
view: |-
{
"position": {
@@ -442,7 +327,7 @@ tasks:
brand: ""
nexttasks:
'#default#':
- - "2"
+ - "4"
"yes":
- "11"
scriptarguments:
@@ -497,8 +382,8 @@ tasks:
view: |-
{
"position": {
- "x": 740,
- "y": 1310
+ "x": 430,
+ "y": 1290
}
}
note: false
@@ -527,14 +412,14 @@ tasks:
scriptarguments:
searchText:
complex:
- root: File.References
+ root: McAfee.TIE.FilesReferences.References
accessor: AgentGuid
separatecontext: false
view: |-
{
"position": {
- "x": 1010,
- "y": 1630
+ "x": 430,
+ "y": 1500
}
}
note: false
@@ -549,16 +434,15 @@ view: |-
{
"linkLabelsPosition": {
"10_11_yes": 0.48,
- "10_2_#default#": 0.48,
"1_4_#default#": 0.1,
- "2_4_#default#": 0.17,
- "5_4_#default#": 0.11,
- "9_4_#default#": 0.12
+ "5_4_#default#": 0.24,
+ "5_8_yes": 0.59,
+ "9_4_#default#": 0.19
},
"paper": {
"dimensions": {
- "height": 2158,
- "width": 1227.5,
+ "height": 1708,
+ "width": 647.5,
"x": 162.5,
"y": 50
}
diff --git a/Packs/McAfee-TIE/Playbooks/playbook-Search_Endpoints_By_Hash_-_TIE_README.md b/Packs/McAfee-TIE/Playbooks/playbook-Search_Endpoints_By_Hash_-_TIE_README.md
index eaf0f73b1082..71521f34452a 100644
--- a/Packs/McAfee-TIE/Playbooks/playbook-Search_Endpoints_By_Hash_-_TIE_README.md
+++ b/Packs/McAfee-TIE/Playbooks/playbook-Search_Endpoints_By_Hash_-_TIE_README.md
@@ -1,4 +1,4 @@
-Hunts for sightings of MD5 hash, SHA1 hash and/or SHA256 hashes on endpoints, using McAfee TIE (requires ePO as well).
+Hunt for sightings of MD5, SHA1 and/or SHA256 hashes on endpoints, using McAfee TIE (requires ePO as well).
Input:
* Hash (default, takes all deferent hashes from context)
@@ -8,37 +8,47 @@ Output:
* Enrich Agents info from ePO
## Dependencies
+
This playbook uses the following sub-playbooks, integrations, and scripts.
### Sub-playbooks
+
This playbook does not use any sub-playbooks.
### Integrations
-* McAfee Threat Intelligence Exchange
+
* McAfee ePO v2
+* McAfeeTIEV2
+* McAfee-TIE
### Scripts
-* EPOFindSystem
+
+This playbook does not use any scripts.
### Commands
-* tie-file-references
+
* epo-find-system
+* tie-file-references
## Playbook Inputs
+
---
| **Name** | **Description** | **Default Value** | **Required** |
-| --- | --- | --- | --- |
-| Hash | The hash to hunt. Can be, "MD5", "SHA1", or "SHA256". The default is set to all hashes. | ${.=val.File.map(function(f) {return [f.MD5, f.SHA1, f.SHA256];}).reduce(function(a, b){return a.concat(b);}, []).filter(function (val1) {return val1;})} |Optional |
+| --- | --- | --- | --- |
+| Hash | The Hash to hunt \(Could be MD5,SHA1,SHA256\).
Default is set to all hashes | ${.=val.File.map(function(f) {return [f.MD5, f.SHA1, f.SHA256];}).reduce(function(a, b){return a.concat(b);}, []).filter(function (val1) {return val1;})} | Optional |
## Playbook Outputs
+
---
| **Path** | **Description** | **Type** |
| --- | --- | --- |
-| Endpoint.Hostname | The hostname. | string |
-| Endpoint | The endpoint. | unknown |
+| Endpoint.Hostname | Hostname | string |
+| Endpoint | The endpoint | unknown |
## Playbook Image
+
---
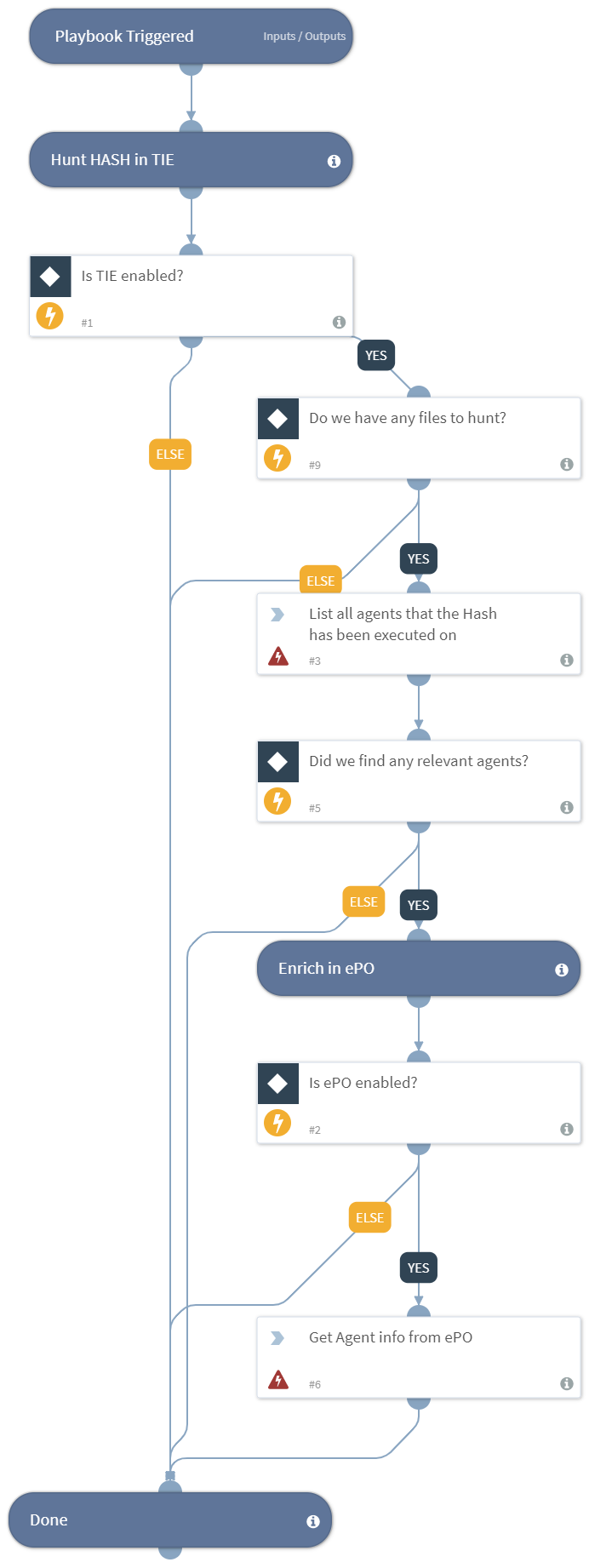
-
+
+
diff --git a/Packs/McAfee-TIE/Playbooks/playbook-TIE_-_IOC_Hunt.yml b/Packs/McAfee-TIE/Playbooks/playbook-TIE_-_IOC_Hunt.yml
index b17c8b7a1b62..77750e94472c 100644
--- a/Packs/McAfee-TIE/Playbooks/playbook-TIE_-_IOC_Hunt.yml
+++ b/Packs/McAfee-TIE/Playbooks/playbook-TIE_-_IOC_Hunt.yml
@@ -77,42 +77,6 @@ tasks:
quietmode: 0
isoversize: false
isautoswitchedtoquietmode: false
- "2":
- id: "2"
- taskid: 992f05a8-3c0e-43bc-8f68-b40d2a9542e9
- type: condition
- task:
- id: 992f05a8-3c0e-43bc-8f68-b40d2a9542e9
- version: -1
- name: Is ePO enabled?
- scriptName: Exists
- type: condition
- iscommand: false
- brand: ""
- description: Is the McAfee ePO integration installed and configured?
- nexttasks:
- '#default#':
- - "4"
- "yes":
- - "10"
- scriptarguments:
- value:
- simple: ${modules(val.brand=="epo")}
- separatecontext: false
- view: |-
- {
- "position": {
- "x": 460,
- "y": 1480
- }
- }
- note: false
- timertriggers: []
- ignoreworker: false
- skipunavailable: false
- quietmode: 0
- isoversize: false
- isautoswitchedtoquietmode: false
"3":
id: "3"
taskid: c906e63c-45c5-4540-8f42-b74db1943725
@@ -121,17 +85,18 @@ tasks:
id: c906e63c-45c5-4540-8f42-b74db1943725
version: -1
name: List all agents that the hash has been executed on
- script: McAfee Threat Intelligence Exchange|||tie-file-references
+ description: Retrieves the set of systems which have referenced (typically executed) the specified hashes.
+ script: '|||tie-file-references'
type: regular
iscommand: true
- brand: McAfee Threat Intelligence Exchange
- description: Retrieves the set of systems which have been referenced (typically executed).
+ brand: ""
nexttasks:
'#none#':
- "5"
scriptarguments:
file:
- simple: ${inputs.Hash}
+ complex:
+ root: inputs.Hash
separatecontext: false
view: |-
{
@@ -163,8 +128,8 @@ tasks:
view: |-
{
"position": {
- "x": 155,
- "y": 1962
+ "x": 162.5,
+ "y": 1492
}
}
note: false
@@ -228,15 +193,17 @@ tasks:
- "4"
scriptarguments:
searchText:
- simple: ${File.References.AgentGuid}
+ complex:
+ root: McAfee.TIE.FilesReferences.References
+ accessor: AgentGuid
verbose:
simple: "false"
separatecontext: false
view: |-
{
"position": {
- "x": 1150,
- "y": 1480
+ "x": 430,
+ "y": 1300
}
}
note: false
@@ -295,8 +262,8 @@ tasks:
view: |-
{
"position": {
- "x": 750,
- "y": 976
+ "x": 430,
+ "y": 926
}
}
note: false
@@ -320,7 +287,7 @@ tasks:
description: Is the McAfee ePO v2 integration installed and configured?
nexttasks:
'#default#':
- - "2"
+ - "4"
"yes":
- "6"
separatecontext: false
@@ -354,42 +321,8 @@ tasks:
view: |-
{
"position": {
- "x": 750,
- "y": 1140
- }
- }
- note: false
- timertriggers: []
- ignoreworker: false
- skipunavailable: false
- quietmode: 0
- isoversize: false
- isautoswitchedtoquietmode: false
- "10":
- id: "10"
- taskid: 8cd1ee6d-2943-42d3-8f28-a22905f59d0f
- type: regular
- task:
- id: 8cd1ee6d-2943-42d3-8f28-a22905f59d0f
- version: -1
- name: Get Agent info from ePO
- scriptName: EPOFindSystem
- type: regular
- iscommand: false
- brand: ""
- description: Finds computers within a specified group in the McAfee ePO system.
- nexttasks:
- '#none#':
- - "4"
- scriptarguments:
- searchText:
- simple: ${File.References.AgentGuid}
- separatecontext: false
- view: |-
- {
- "position": {
- "x": 460,
- "y": 1750
+ "x": 430,
+ "y": 1090
}
}
note: false
@@ -399,19 +332,20 @@ tasks:
quietmode: 0
isoversize: false
isautoswitchedtoquietmode: false
-system: true
view: |-
{
"linkLabelsPosition": {
"1_4_#default#": 0.1,
- "2_4_#default#": 0.17,
- "5_4_#default#": 0.11
+ "5_4_#default#": 0.28,
+ "5_8_yes": 0.58,
+ "9_4_#default#": 0.44,
+ "9_6_yes": 0.59
},
"paper": {
"dimensions": {
- "height": 1977,
- "width": 1375,
- "x": 155,
+ "height": 1507,
+ "width": 647.5,
+ "x": 162.5,
"y": 50
}
}
diff --git a/Packs/McAfee-TIE/Playbooks/playbook-TIE_-_IOC_Hunt_README.md b/Packs/McAfee-TIE/Playbooks/playbook-TIE_-_IOC_Hunt_README.md
index ccd6be97e26a..62a7ade611bf 100644
--- a/Packs/McAfee-TIE/Playbooks/playbook-TIE_-_IOC_Hunt_README.md
+++ b/Packs/McAfee-TIE/Playbooks/playbook-TIE_-_IOC_Hunt_README.md
@@ -1,4 +1,4 @@
-Hunts for sightings of MD5 hash, SHA1 hash and/or SHA256 hashes on endpoints, using McAfee TIE (requires ePO as well).
+Hunt for sightings of MD5, SHA1 and/or SHA256 hashes on endpoints, using McAfee TIE (requires ePO as well).
Input:
* Hash (default, takes all deferent hashes from context)
@@ -8,33 +8,45 @@ Output:
* Enrich Agents info from ePO
## Dependencies
+
This playbook uses the following sub-playbooks, integrations, and scripts.
### Sub-playbooks
+
This playbook does not use any sub-playbooks.
### Integrations
-* McAfee Threat Intelligence Exchange
-* McAfee ePO v2
+
+* McAfeeTIEV2
+* McAfee-TIE
### Scripts
-* EPOFindSystem
+
* Exists
### Commands
-* tie-file-references
+
* epo-find-system
+* tie-file-references
## Playbook Inputs
+
---
| **Name** | **Description** | **Default Value** | **Required** |
| --- | --- | --- | --- |
-| Hash | The hash to hunt. Can be, "MD5", "SHA1", or "SHA256". The default is set to all hashes | ${.=val.File.map(function(f) {return [f.MD5, f.SHA1, f.SHA256];}).reduce(function(a, b){return a.concat(b);}, []).filter(function (val1) {return val1;})} | Optional |
+| Hash | The Hash to hunt \(Could be MD5,SHA1,SHA256\).
Default is set to all hashes | ${.=val.File.map(function(f) {return [f.MD5, f.SHA1, f.SHA256];}).reduce(function(a, b){return a.concat(b);}, []).filter(function (val1) {return val1;})} | Optional |
## Playbook Outputs
+
---
-There are no outputs for this playbook.
+
+| **Path** | **Description** | **Type** |
+| --- | --- | --- |
+| McAfee.ePO.Endpoint | Endpoint information for agents has been executed on. | unknown |
+
## Playbook Image
+
---
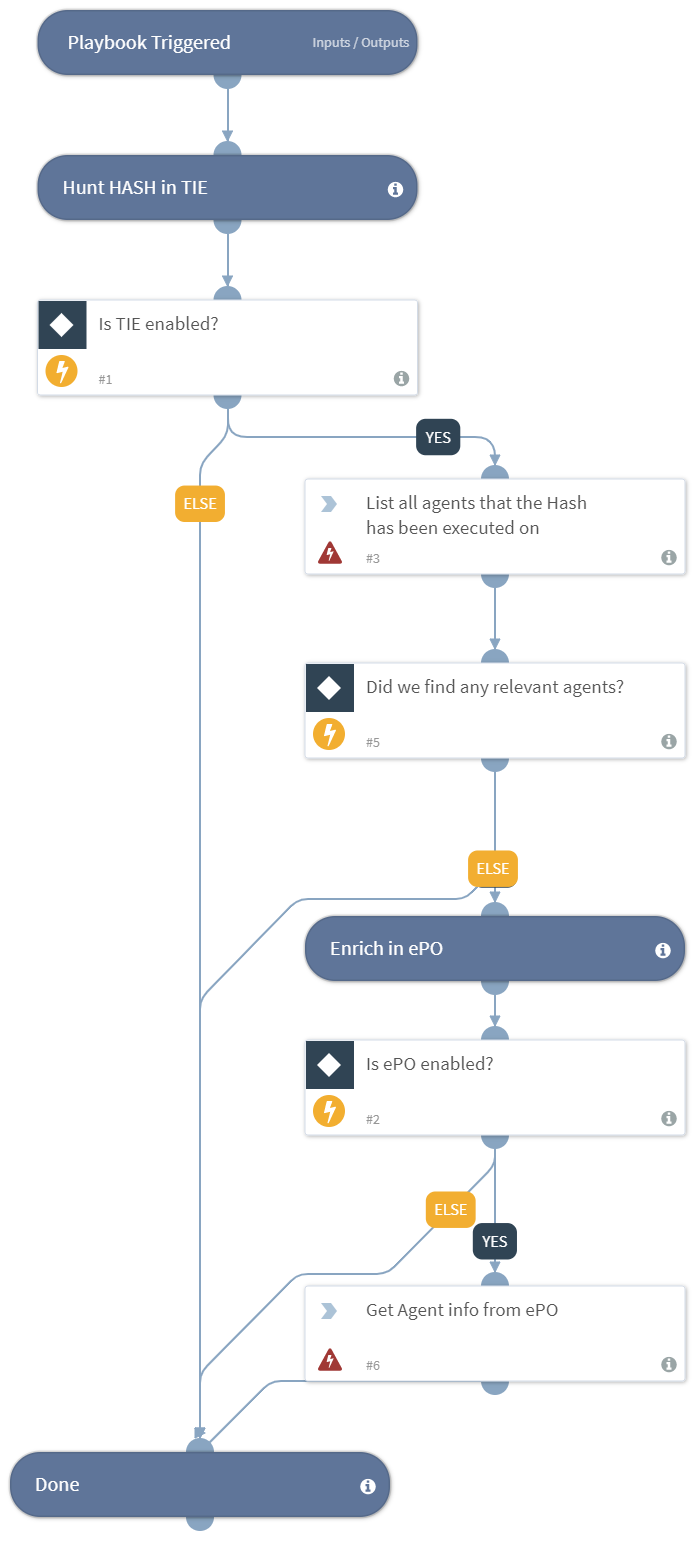
-
+
+
diff --git a/Packs/McAfee-TIE/ReleaseNotes/2_0_7.md b/Packs/McAfee-TIE/ReleaseNotes/2_0_7.md
new file mode 100644
index 000000000000..0b25b4f085b5
--- /dev/null
+++ b/Packs/McAfee-TIE/ReleaseNotes/2_0_7.md
@@ -0,0 +1,10 @@
+#### Playbooks
+##### TIE - IOC Hunt
+- Updated the deprecated command from ***tie-file-references (McAfee Threat Intelligence Exchange)*** to ***tie-file-references***.
+- Removed the ***EPOFindSystem*** command. This command is part of the deprecated **McAfee ePO** pack, which has reached its end of life
+(EOL) and is no longer supported. Use the **McAfee ePO v2** integration instead.
+
+##### Search Endpoints By Hash - TIE
+- Updated the deprecated command from ***tie-file-references (McAfee Threat Intelligence Exchange)*** to ***tie-file-references***.
+- Removed the ***EPOFindSystem*** command. This command is part of the deprecated **McAfee ePO** pack, which has reached its end of life
+(EOL) and is no longer supported. Use the **McAfee ePO v2** integration instead.
\ No newline at end of file
diff --git a/Packs/McAfee-TIE/doc_files/Search_Endpoints_By_Hash_-_TIE.png b/Packs/McAfee-TIE/doc_files/Search_Endpoints_By_Hash_-_TIE.png
new file mode 100644
index 000000000000..a3a47e380d32
Binary files /dev/null and b/Packs/McAfee-TIE/doc_files/Search_Endpoints_By_Hash_-_TIE.png differ
diff --git a/Packs/McAfee-TIE/doc_files/TIE_-_IOC_Hunt.png b/Packs/McAfee-TIE/doc_files/TIE_-_IOC_Hunt.png
new file mode 100644
index 000000000000..fbd8157fa54b
Binary files /dev/null and b/Packs/McAfee-TIE/doc_files/TIE_-_IOC_Hunt.png differ
diff --git a/Packs/McAfee-TIE/pack_metadata.json b/Packs/McAfee-TIE/pack_metadata.json
index c9e705c3d346..f61327ed7def 100644
--- a/Packs/McAfee-TIE/pack_metadata.json
+++ b/Packs/McAfee-TIE/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "McAfee Threat Intelligence Exchange",
"description": "Connect to McAfee TIE using the McAfee DXL client.",
"support": "xsoar",
- "currentVersion": "2.0.6",
+ "currentVersion": "2.0.7",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/PrismaSaasSecurity/Playbooks/Saas_Security_-_Incident_Processor.yml b/Packs/PrismaSaasSecurity/Playbooks/Saas_Security_-_Incident_Processor.yml
index bdea3e32697a..023e3b0c28f7 100644
--- a/Packs/PrismaSaasSecurity/Playbooks/Saas_Security_-_Incident_Processor.yml
+++ b/Packs/PrismaSaasSecurity/Playbooks/Saas_Security_-_Incident_Processor.yml
@@ -43,10 +43,10 @@ tasks:
version: -1
name: Send Notification Email
description: Sends an email using EWS.
- script: EWS Mail Sender|||send-mail
+ script: '|||send-mail'
type: regular
iscommand: true
- brand: EWS Mail Sender
+ brand: ""
nexttasks:
'#none#':
- "8"
@@ -60,8 +60,11 @@ tasks:
subject:
simple: An Incident Found in SaaS Security Platform
to:
- simple: ${incident.itemowneremail}
+ complex:
+ root: incident
+ accessor: itemowneremail
separatecontext: false
+ continueonerrortype: ""
view: |-
{
"position": {
@@ -391,12 +394,6 @@ view: |-
}
}
inputs:
-- key: updated_at
- value:
- simple: ${incident.lastupdatetime}
- required: false
- description: This is the incident updated at timestamp.
- playbookInputQuery:
- key: tenant_admin
value: {}
required: false
diff --git a/Packs/PrismaSaasSecurity/Playbooks/Saas_Security_-_Incident_Processor_README.md b/Packs/PrismaSaasSecurity/Playbooks/Saas_Security_-_Incident_Processor_README.md
index 895396704426..ea527a88d206 100644
--- a/Packs/PrismaSaasSecurity/Playbooks/Saas_Security_-_Incident_Processor_README.md
+++ b/Packs/PrismaSaasSecurity/Playbooks/Saas_Security_-_Incident_Processor_README.md
@@ -1,30 +1,35 @@
This playbook notifies incidents owner and provides remediation options to Saas Security admin for resolving incidents.
## Dependencies
+
This playbook uses the following sub-playbooks, integrations, and scripts.
### Sub-playbooks
-* Send Action Taken Email to Tenant Admin
-* Send Action Taken Email to Assignee
+
+* Saas Security - Take Action on the Incident
### Integrations
-* EWS Mail Sender
+
+This playbook does not use any integrations.
### Scripts
-This playbook does not use any scripts.
+
+* IsIntegrationAvailable
### Commands
+
* send-mail
## Playbook Inputs
+
---
| **Name** | **Description** | **Default Value** | **Required** |
| --- | --- | --- | --- |
-| updated_at | This is the incident updated at timestamp. | ${incident.saassecurityincidentupdatedat} | Optional |
| tenant_admin | This is the tenant admin email. | | Optional |
## Playbook Outputs
+
---
| **Path** | **Description** | **Type** |
@@ -59,5 +64,7 @@ This playbook does not use any scripts.
| SaasSecurity.Incident.asset_owner_email | Email address of the asset owner. | unknown |
## Playbook Image
+
---
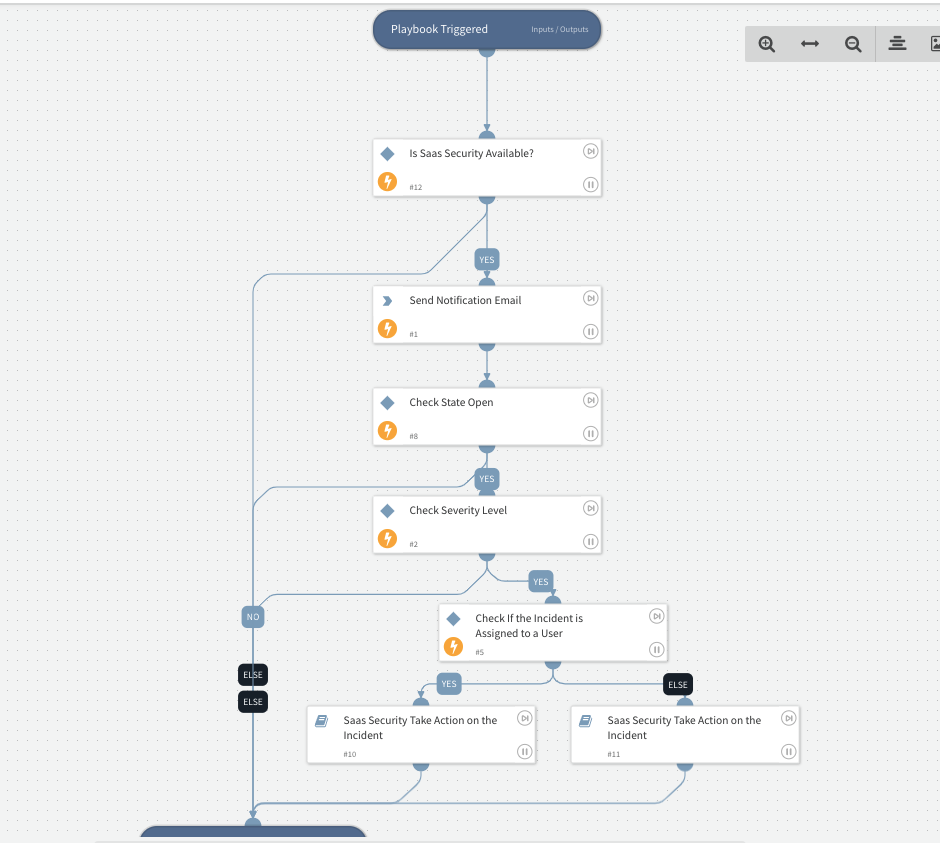
-
\ No newline at end of file
+
+
diff --git a/Packs/PrismaSaasSecurity/ReleaseNotes/2_0_21.md b/Packs/PrismaSaasSecurity/ReleaseNotes/2_0_21.md
new file mode 100644
index 000000000000..07df0aea2212
--- /dev/null
+++ b/Packs/PrismaSaasSecurity/ReleaseNotes/2_0_21.md
@@ -0,0 +1,4 @@
+#### Playbooks
+
+##### Saas Security - Incident Processor
+Updated the deprecated command from ***send-mail (EWS Mail Sender)*** to ***send-mail***.
\ No newline at end of file
diff --git a/Packs/PrismaSaasSecurity/doc_files/Incident_Processor_Playbook.png b/Packs/PrismaSaasSecurity/doc_files/Incident_Processor_Playbook.png
deleted file mode 100644
index aa49004ddb3f..000000000000
Binary files a/Packs/PrismaSaasSecurity/doc_files/Incident_Processor_Playbook.png and /dev/null differ
diff --git a/Packs/PrismaSaasSecurity/doc_files/Saas_Security_-_Incident_Processor.png b/Packs/PrismaSaasSecurity/doc_files/Saas_Security_-_Incident_Processor.png
new file mode 100644
index 000000000000..69cbb419424c
Binary files /dev/null and b/Packs/PrismaSaasSecurity/doc_files/Saas_Security_-_Incident_Processor.png differ
diff --git a/Packs/PrismaSaasSecurity/pack_metadata.json b/Packs/PrismaSaasSecurity/pack_metadata.json
index c13909e41ab6..e5f27d3b68b7 100644
--- a/Packs/PrismaSaasSecurity/pack_metadata.json
+++ b/Packs/PrismaSaasSecurity/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "SaaS Security by Palo Alto Networks",
"description": "SaaS Security connects directly to your sanctioned SaaS applications to provide data classification, sharing and permission visibility, and threat detection.",
"support": "xsoar",
- "currentVersion": "2.0.20",
+ "currentVersion": "2.0.21",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Tanium/Playbooks/playbook-Tanium_Demo.yml b/Packs/Tanium/Playbooks/playbook-Tanium_Demo.yml
index 2f3785ce1df9..607211ac2ee2 100644
--- a/Packs/Tanium/Playbooks/playbook-Tanium_Demo.yml
+++ b/Packs/Tanium/Playbooks/playbook-Tanium_Demo.yml
@@ -40,17 +40,19 @@ tasks:
id: 3533d2be-a90d-4f93-8630-c169d790254d
version: -1
name: Ask questions
- description: Ask the server to parse the question text and choose the first parsed result as the question to run
- script: Tanium|||tn-ask-question
+ description: Asks the server to parse the question text and choose the first parsed result as the question to run.
+ script: '|||tn-ask-question'
type: regular
iscommand: true
- brand: Tanium
+ brand: ""
nexttasks:
'#none#':
- "3"
scriptarguments:
- question:
- simple: ${Tanium.SavedQuestions.query_text}
+ question-text:
+ complex:
+ root: Tanium.SavedQuestion
+ accessor: QueryText
separatecontext: false
view: |-
{
@@ -72,16 +74,16 @@ tasks:
id: d7609125-e21f-4871-8d72-518017ea0b93
version: -1
name: Run a complex Tanium query to find all machines with processes starting with "EC"
- description: Ask the server to parse the question text and choose the first parsed result as the question to run
- script: Tanium|||tn-ask-question
+ description: Asks the server to parse the question text and choose the first parsed result as the question to run.
+ script: '|||tn-ask-question'
type: regular
iscommand: true
- brand: Tanium
+ brand: ""
nexttasks:
'#none#':
- "8"
scriptarguments:
- question:
+ question-text:
simple: Get all machines with processes starting with "EC"
separatecontext: false
view: |-
@@ -104,17 +106,16 @@ tasks:
id: 6553c9ee-e178-4084-8718-5e2fdc549fed
version: -1
name: Get saved question - Tanium Client Versions
- description: Get a saved question by name or id
- script: Tanium|||tn-get-saved-question
+ description: Returns a saved question object based on name or ID.
+ script: '|||tn-get-saved-question-metadata'
type: regular
iscommand: true
- brand: Tanium
+ brand: ""
nexttasks:
'#none#':
- "6"
scriptarguments:
- id: {}
- name:
+ question-name:
simple: Tanium Client Versions
separatecontext: false
view: |-
@@ -137,17 +138,16 @@ tasks:
id: a4aaa5eb-3724-43fe-86e5-c8e7363743ed
version: -1
name: Get saved question - Running Applications
- description: Get a saved question by name or id
- script: Tanium|||tn-get-saved-question
+ description: Returns a saved question object based on name or ID.
+ script: '|||tn-get-saved-question-metadata'
type: regular
iscommand: true
- brand: Tanium
+ brand: ""
nexttasks:
'#none#':
- "2"
scriptarguments:
- id: {}
- name:
+ question-name:
simple: Running Applications
separatecontext: false
view: |-
diff --git a/Packs/Tanium/Playbooks/playbook-Tanium_Demo_README.md b/Packs/Tanium/Playbooks/playbook-Tanium_Demo_README.md
index 1057fb354060..facdc7a7a9dd 100644
--- a/Packs/Tanium/Playbooks/playbook-Tanium_Demo_README.md
+++ b/Packs/Tanium/Playbooks/playbook-Tanium_Demo_README.md
@@ -1,30 +1,40 @@
-Shows how to use automation scripts to interact with Tanium.
+This playbook shows how to use automation scripts to interact with Tanium.
## Dependencies
+
This playbook uses the following sub-playbooks, integrations, and scripts.
### Sub-playbooks
+
This playbook does not use any sub-playbooks.
### Integrations
+
* Tanium
+* Tanium_v2
### Scripts
+
This playbook does not use any scripts.
### Commands
-* tn-get-saved-question
+
* tn-ask-question
* tn-deploy-package
+* tn-get-saved-question-metadata
## Playbook Inputs
+
---
There are no inputs for this playbook.
## Playbook Outputs
+
---
There are no outputs for this playbook.
## Playbook Image
+
---
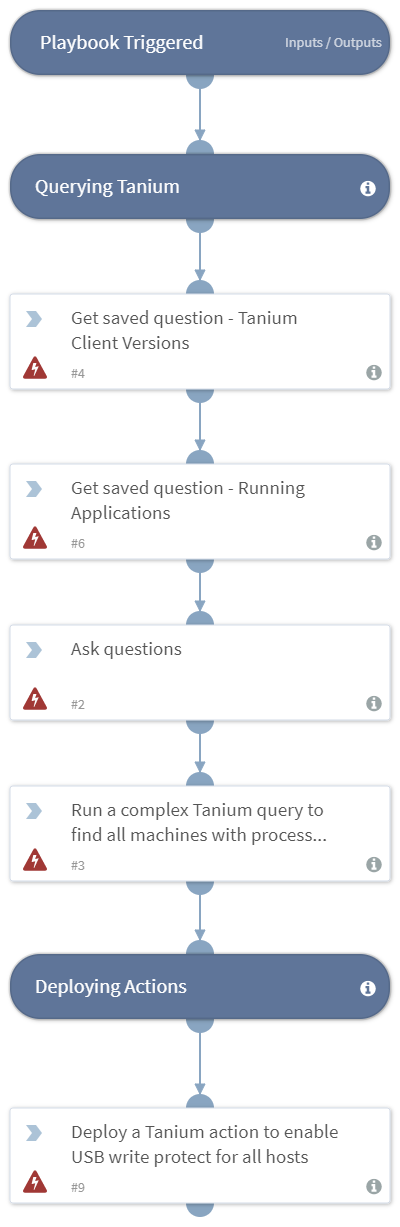
-
+
+
diff --git a/Packs/Tanium/ReleaseNotes/1_0_25.md b/Packs/Tanium/ReleaseNotes/1_0_25.md
new file mode 100644
index 000000000000..904ae3e83b2e
--- /dev/null
+++ b/Packs/Tanium/ReleaseNotes/1_0_25.md
@@ -0,0 +1,7 @@
+
+#### Playbooks
+
+##### Tanium Demo Playbook
+
+- Updated the deprecated command from ***tn-get-saved-question (Tanium)*** to ***tn-get-saved-question-metadata***.
+- Updated the deprecated command from ***tn-ask-question (Tanium)*** to ***tn-ask-question***.
\ No newline at end of file
diff --git a/Packs/Tanium/doc_files/Tanium_Demo_Playbook.png b/Packs/Tanium/doc_files/Tanium_Demo_Playbook.png
new file mode 100644
index 000000000000..ccdf51325cf8
Binary files /dev/null and b/Packs/Tanium/doc_files/Tanium_Demo_Playbook.png differ
diff --git a/Packs/Tanium/pack_metadata.json b/Packs/Tanium/pack_metadata.json
index 0a485bcba8f8..9c6d515ef7ce 100644
--- a/Packs/Tanium/pack_metadata.json
+++ b/Packs/Tanium/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Tanium",
"description": "Tanium endpoint security and systems management",
"support": "xsoar",
- "currentVersion": "1.0.24",
+ "currentVersion": "1.0.25",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/qualys/Playbooks/playbook-Vulnerability_Management__-_Qualys_(Job).yml b/Packs/qualys/Playbooks/playbook-Vulnerability_Management__-_Qualys_(Job).yml
index 24f25b54bdb7..fc1bdda98255 100644
--- a/Packs/qualys/Playbooks/playbook-Vulnerability_Management__-_Qualys_(Job).yml
+++ b/Packs/qualys/Playbooks/playbook-Vulnerability_Management__-_Qualys_(Job).yml
@@ -2,7 +2,9 @@ id: vulnerability_management_-_qualys_Job
version: -1
name: Vulnerability Management - Qualys (Job)
fromversion: 5.0.0
+deprecated: true
description: |-
+ Deprecated. Use the `Vulnerability Management - Qualys (Job) - V2` playbook instead.
Use the latest Qualys report to manage vulnerabilities.
This playbook runs as a job, and by default creates incidents of type "Vulnerability" based on assets and vulnerabilities.
diff --git a/Packs/qualys/Playbooks/playbook-Vulnerability_Management__-_Qualys_(Job)_README.md b/Packs/qualys/Playbooks/playbook-Vulnerability_Management__-_Qualys_(Job)_README.md
index f22bffc55e93..28de1223c4cf 100644
--- a/Packs/qualys/Playbooks/playbook-Vulnerability_Management__-_Qualys_(Job)_README.md
+++ b/Packs/qualys/Playbooks/playbook-Vulnerability_Management__-_Qualys_(Job)_README.md
@@ -1,48 +1,56 @@
-Manages vulnerabilities using the latest Qualys report.
+Deprecated. Use the **Vulnerability Management - Qualys (Job) - V2** playbook instead.
+Use the latest Qualys report to manage vulnerabilities.
This playbook runs as a job, and by default creates incidents of type "Vulnerability" based on assets and vulnerabilities.
The incidents are created from the latest version of the report determined by the report timestamp.
-
-You can define the minimum severity `minSeverity` that incidents are created for.
+You can define the minimum severity (minSeverity) that incidents are created for.
Duplicate incidents are not created for the same asset ID and QID.
This playbook is a part of a series of playbooks for Qualys vulnerability management and remediation.
For this series of playbooks to run successfully, create a Job and do the following:
1. Assign this playbook to the Job
2. Enter the Qualys XML report name into the "Details" field
-3. Associate the "Vulnerability" type incident to the `Vulnerability Handling - Qualys` playbook.
+3. Associate the *Vulnerability* type incident to the **Vulnerability Handling - Qualys** playbook.
## Dependencies
+
This playbook uses the following sub-playbooks, integrations, and scripts.
### Sub-playbooks
+
This playbook does not use any sub-playbooks.
### Integrations
+
* Qualys
-* Builtin
### Scripts
+
* QualysCreateIncidentFromReport
* Set
### Commands
+
+* qualys-report-list
* qualys-report-fetch
* closeInvestigation
-* qualys-report-list
## Playbook Inputs
+
---
-| **Name** | **Description** | **Default Value** | **Source** | **Required** |
-| --- | --- | --- | --- | --- |
-| QualysReportTitle | The report title as it appears in Qualys. Has to be in XML format. | details | incident | Required |
-| MinSeverity | The minimum Qualys severity (1 -5) to create incidents for. | 3 | - | Required |
+| **Name** | **Description** | **Default Value** | **Required** |
+| --- | --- | --- | --- |
+| QualysReportTitle | The report title as it appears in Qualys.
Has to be in XML format. | incident.details | Required |
+| MinSeverity | The minimum Qualys severity \(1 -5\) to create incidents for. | 3 | Required |
## Playbook Outputs
+
---
There are no outputs for this playbook.
## Playbook Image
+
---
-.png)
+
+.png)
diff --git a/Packs/qualys/ReleaseNotes/1_2_9.md b/Packs/qualys/ReleaseNotes/1_2_9.md
new file mode 100644
index 000000000000..1dc8d500ebc5
--- /dev/null
+++ b/Packs/qualys/ReleaseNotes/1_2_9.md
@@ -0,0 +1,6 @@
+
+#### Playbooks
+
+##### Vulnerability Management - Qualys (Job)
+
+Deprecated. Use the **Vulnerability Management - Qualys (Job) - V2** playbook instead.
diff --git a/Packs/qualys/doc_files/Vulnerability_Management_-_Qualys_(Job).png b/Packs/qualys/doc_files/Vulnerability_Management_-_Qualys_(Job).png
new file mode 100644
index 000000000000..36d5abf4eb11
Binary files /dev/null and b/Packs/qualys/doc_files/Vulnerability_Management_-_Qualys_(Job).png differ
diff --git a/Packs/qualys/pack_metadata.json b/Packs/qualys/pack_metadata.json
index a4c6d20bd61d..94745e94f7e4 100644
--- a/Packs/qualys/pack_metadata.json
+++ b/Packs/qualys/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Qualys",
"description": "Qualys Vulnerability Management let's you create, run, fetch and manage reports, launch and manage vulnerability and compliance scans, and manage the host assets you want to scan for vulnerabilities and compliance",
"support": "xsoar",
- "currentVersion": "1.2.8",
+ "currentVersion": "1.2.9",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",