diff --git a/.github/ISSUE_TEMPLATE/bug_report.md b/.github/ISSUE_TEMPLATE/bug_report.md
index c79686bb05..d882cbb3a4 100644
--- a/.github/ISSUE_TEMPLATE/bug_report.md
+++ b/.github/ISSUE_TEMPLATE/bug_report.md
@@ -38,11 +38,11 @@ Steps to reproduce the behavior:
-## Expected behaviour
+## Expected behavior
-## Actual behaviour
+## Actual behavior
diff --git a/.github/workflows/pre-commit.yml b/.github/workflows/pre-commit.yml
index 71e872ad97..31232f83f8 100644
--- a/.github/workflows/pre-commit.yml
+++ b/.github/workflows/pre-commit.yml
@@ -1,4 +1,4 @@
-name: pre-commit
+name: Pre-commit
on:
pull_request:
@@ -10,41 +10,19 @@ on:
- '**.yaml'
env:
+ TERRAFORM_VERSION: 1.3.10
TERRAFORM_DOCS_VERSION: v0.16.0
- TFSEC_VERSION: v1.22.0
TF_PLUGIN_CACHE_DIR: ${{ github.workspace }}/.terraform.d/plugin-cache
- TFLINT_VERSION: v0.42.1
+ TFLINT_VERSION: v0.50.2
concurrency:
group: '${{ github.workflow }} @ ${{ github.event.pull_request.head.label || github.head_ref || github.ref }}'
cancel-in-progress: true
jobs:
- collectInputs:
- name: Collect workflow inputs
- runs-on: ubuntu-latest
- outputs:
- directories: ${{ steps.dirs.outputs.directories }}
- steps:
- - name: Harden Runner
- uses: step-security/harden-runner@v2
- with:
- egress-policy: audit
-
- - name: Checkout
- uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11
-
- - name: Get root directories
- id: dirs
- uses: clowdhaus/terraform-composite-actions/directories@v1.8.3
-
- preCommitMinVersions:
+ pre-commit:
name: Min TF pre-commit
- needs: collectInputs
runs-on: ubuntu-latest
- strategy:
- matrix:
- directory: ${{ fromJson(needs.collectInputs.outputs.directories) }}
steps:
- name: Harden Runner
uses: step-security/harden-runner@v2
@@ -62,7 +40,7 @@ jobs:
with:
filters: |
src:
- - '${{ matrix.directory }}/*.tf'
+ - '*.tf'
- name: Config Terraform plugin cache
if: steps.changes.outputs.src== 'true'
@@ -76,18 +54,10 @@ jobs:
key: ${{ runner.os }}-terraform-${{ hashFiles('**/.terraform.lock.hcl') }}
restore-keys: ${{ runner.os }}-terraform-
- - name: Terraform min/max versions
- uses: clowdhaus/terraform-min-max@v1.2.7
- if: steps.changes.outputs.src== 'true'
- id: minMax
- with:
- directory: ${{ matrix.directory }}
-
- name: Pre-commit Terraform ${{ steps.minMax.outputs.minVersion }}
uses: clowdhaus/terraform-composite-actions/pre-commit@v1.8.3
if: steps.changes.outputs.src== 'true'
with:
- terraform-version: ${{ steps.minMax.outputs.maxVersion }}
+ terraform-version: ${{ env.TERRAFORM_VERSION }}
terraform-docs-version: ${{ env.TERRAFORM_DOCS_VERSION }}
tflint-version: ${{ env.TFLINT_VERSION }}
- args: '--files ${{ matrix.directory }}/*'
diff --git a/.pre-commit-config.yaml b/.pre-commit-config.yaml
index 734900772e..999d31212a 100644
--- a/.pre-commit-config.yaml
+++ b/.pre-commit-config.yaml
@@ -1,35 +1,44 @@
repos:
+ - repo: https://github.com/streetsidesoftware/cspell-cli
+ rev: v8.3.0
+ hooks:
+ - id: cspell
+ args: [--exclude, 'ADOPTERS.md', --exclude, '.pre-commit-config.yaml', --exclude, '.gitignore', --exclude, '*.drawio', --exclude, 'mkdocs.yml', --exclude, '.helmignore', --exclude, '.github/workflows/*', --exclude, 'patterns/istio-multi-cluster/*', --exclude, 'patterns/blue-green-upgrade/*']
+ - repo: https://github.com/macisamuele/language-formatters-pre-commit-hooks
+ rev: v2.12.0
+ hooks:
+ - id: pretty-format-yaml
+ args: [--autofix, --indent, '2', --offset, '2', --preserve-quotes]
- repo: https://github.com/pre-commit/pre-commit-hooks
rev: v4.5.0
hooks:
- id: trailing-whitespace
- args: ['--markdown-linebreak-ext=md']
- id: end-of-file-fixer
- id: check-merge-conflict
- id: detect-private-key
- id: detect-aws-credentials
- args: ['--allow-missing-credentials']
+ args: [--allow-missing-credentials]
- repo: https://github.com/antonbabenko/pre-commit-terraform
rev: v1.86.0
hooks:
- id: terraform_fmt
- id: terraform_docs
args:
- - '--args=--lockfile=false'
+ - --args=--lockfile=false
- id: terraform_tflint
args:
- - '--args=--only=terraform_deprecated_interpolation'
- - '--args=--only=terraform_deprecated_index'
- - '--args=--only=terraform_unused_declarations'
- - '--args=--only=terraform_comment_syntax'
- - '--args=--only=terraform_documented_outputs'
- - '--args=--only=terraform_documented_variables'
- - '--args=--only=terraform_typed_variables'
- - '--args=--only=terraform_module_pinned_source'
- - '--args=--only=terraform_naming_convention'
- - '--args=--only=terraform_required_version'
- - '--args=--only=terraform_required_providers'
- - '--args=--only=terraform_unused_required_providers'
- - '--args=--only=terraform_workspace_remote'
+ - --args=--only=terraform_deprecated_interpolation
+ - --args=--only=terraform_deprecated_index
+ - --args=--only=terraform_unused_declarations
+ - --args=--only=terraform_comment_syntax
+ - --args=--only=terraform_documented_outputs
+ - --args=--only=terraform_documented_variables
+ - --args=--only=terraform_typed_variables
+ - --args=--only=terraform_module_pinned_source
+ - --args=--only=terraform_naming_convention
+ - --args=--only=terraform_required_version
+ - --args=--only=terraform_required_providers
+ - --args=--only=terraform_unused_required_providers
+ - --args=--only=terraform_workspace_remote
- id: terraform_validate
exclude: (docs|modules)
diff --git a/cspell.config.yaml b/cspell.config.yaml
new file mode 100644
index 0000000000..f0e8f532fa
--- /dev/null
+++ b/cspell.config.yaml
@@ -0,0 +1,6 @@
+dictionaryDefinitions:
+ - name: bpWords
+ path: ./docs/cSpell_dict.txt
+ addWords: true
+dictionaries:
+ - bpWords
diff --git a/docs/cSpell_dict.txt b/docs/cSpell_dict.txt
new file mode 100644
index 0000000000..33aad47b8b
--- /dev/null
+++ b/docs/cSpell_dict.txt
@@ -0,0 +1,161 @@
+acmpca
+acmca_arn
+addrs
+adot
+agones
+akuity
+algbw
+ALLOWVOLUMEEXPANSION
+amazonlinux
+apigatewayv2
+apiextensions
+apiversion
+applicationset
+appsets
+argocd
+argoproj
+athenaaccess
+athenacurcfn
+autoscaler
+awscli
+awscliv2
+awslabs
+awspca
+awspcaclusterissuers
+basepath
+billingreports
+bootstrappers
+boto
+bottlerocket
+busbw
+cacerts
+cainjector
+chdir
+cidrsubnet
+ciliumnetworkpolicy
+clusterip
+clusterissuer
+clusterrole
+clusterrolebinding
+clusterwide
+cncf
+compat
+configmap
+concat
+containerd
+coredns
+cuda
+customresourcedefinition
+crossplane
+crds
+curlimages
+cwlogs
+daemonset
+dcgm
+distro
+ecrpublic
+ecsdemo
+ecsfrontend
+elbv
+eksctl
+eksvpc
+emrcontainers
+errexit
+eventbridge
+externaldns
+externalsecrets
+externalsnat
+fargate
+fileexists
+finalizer
+finalizers
+flblogs
+fluentbit
+gameserver
+gameservers
+gavinbunney
+gitops
+helloworld
+heptio
+identitystore
+iedn
+iezn
+ingressgateway
+instanceids
+ipam
+irsa
+istio
+istiod
+istioing
+jsonencode
+karpenter
+kiali
+kubeconfig
+kubecost
+kubeflow
+kubelet
+kyverno
+libfabric
+logtag
+loglevel
+makefiles
+maxport
+minport
+mkdocs
+mktemp
+mountpoint
+mpijob
+mpijobs
+mtls
+nccl
+netcat
+nics
+nodegroup
+nodeport
+nvme
+oidc
+persistentvolume
+pkce
+pubkey
+privateca
+privatelink
+prometheusservice
+proto
+readyz
+reclaimpolicy
+redop
+replicaset
+rdmap
+rolearn
+rollouts
+rootdir
+rpfilter
+secretpassword
+secretstore
+secretuser
+selfsigned
+serviceaccount
+SHA512WITHRSA
+sleepdocs
+ssoadmin
+storageclass
+storageclasses
+tcpdump
+templatefile
+tfstate
+tfvars
+tolist
+toset
+velero
+VOLUMEBINDINGMODE
+vpclattice
+webfront
+wontfix
+yamlencode
+xlarge
+xonotic
+xrds
+xvda
+xvdb
+zipkin
+zipmap
diff --git a/docs/getting-started.md b/docs/getting-started.md
index 8e1433030c..c30f25bd09 100644
--- a/docs/getting-started.md
+++ b/docs/getting-started.md
@@ -25,9 +25,9 @@ directory of your choice.
terraform apply -auto-approve
```
- For patterns that deviate from this general flow, see the pattern's respective `REAMDE.md` for more details.
+ For patterns that deviate from this general flow, see the pattern's respective `README.md` for more details.
- !!! info "Terraform targetted apply"
+ !!! info "Terraform targeted apply"
Please see the [Terraform Caveats](https://aws-ia.github.io/terraform-aws-eks-blueprints/#terraform-caveats) section for details on the use of targeted Terraform apply's
3. Once all of the resources have successfully been provisioned, the following command can be used to update the `kubeconfig`
diff --git a/docs/v4-to-v5/example/v5.tf b/docs/v4-to-v5/example/v5.tf
index 2d0dd7df17..01dd67fc54 100644
--- a/docs/v4-to-v5/example/v5.tf
+++ b/docs/v4-to-v5/example/v5.tf
@@ -14,7 +14,6 @@ provider "kubernetes" {
# Cluster
################################################################################
-#tfsec:ignore:aws-eks-enable-control-plane-logging
module "eks" {
source = "terraform-aws-modules/eks/aws"
version = "~> 19.13"
diff --git a/mkdocs.yml b/mkdocs.yml
index 2e751bfc61..8712629b9c 100644
--- a/mkdocs.yml
+++ b/mkdocs.yml
@@ -1,10 +1,10 @@
site_name: Amazon EKS Blueprints for Terraform
-docs_dir: 'docs/'
-copyright: 'Copyright © Amazon 2023'
-site_author: 'AWS'
-site_url: 'https://aws-ia.github.io/terraform-aws-eks-blueprints/'
-repo_name: 'terraform-aws-eks-blueprints'
-repo_url: 'https://github.com/aws-ia/terraform-aws-eks-blueprints'
+docs_dir: docs/
+copyright: Copyright © Amazon 2023
+site_author: AWS
+site_url: https://aws-ia.github.io/terraform-aws-eks-blueprints/
+repo_name: terraform-aws-eks-blueprints
+repo_url: https://github.com/aws-ia/terraform-aws-eks-blueprints
theme:
name: material
diff --git a/patterns/agones-game-controller/test/sample-game-server/gameserver.yaml b/patterns/agones-game-controller/test/sample-game-server/gameserver.yaml
index cae9671f1d..301f72e55a 100644
--- a/patterns/agones-game-controller/test/sample-game-server/gameserver.yaml
+++ b/patterns/agones-game-controller/test/sample-game-server/gameserver.yaml
@@ -4,18 +4,18 @@ metadata:
generateName: "simple-game-server-"
spec:
ports:
- - name: default
- portPolicy: Dynamic
- containerPort: 7654
+ - name: default
+ portPolicy: Dynamic
+ containerPort: 7654
template:
spec:
containers:
- - name: simple-game-server
- image: gcr.io/agones-images/simple-game-server:0.3
- resources:
- requests:
- memory: "64Mi"
- cpu: "20m"
- limits:
- memory: "64Mi"
- cpu: "20m"
+ - name: simple-game-server
+ image: gcr.io/agones-images/simple-game-server:0.3
+ resources:
+ requests:
+ memory: "64Mi"
+ cpu: "20m"
+ limits:
+ memory: "64Mi"
+ cpu: "20m"
diff --git a/patterns/appmesh-mtls/README.md b/patterns/appmesh-mtls/README.md
index a7dc2802de..ea56e66391 100644
--- a/patterns/appmesh-mtls/README.md
+++ b/patterns/appmesh-mtls/README.md
@@ -17,11 +17,11 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
```text
NAMESPACE NAME READY STATUS RESTARTS AGE
appmesh-system appmesh-controller-7c98b87bdc-q6226 1/1 Running 0 4h44m
- cert-manager cert-manager-87f5555f-tcxj7 1/1 Running 0 4h43m
- cert-manager cert-manager-cainjector-8448ff8ddb-wwjsc 1/1 Running 0 4h43m
- cert-manager cert-manager-webhook-5468b675b-fvdwk 1/1 Running 0 4h43m
+ cert-manager cert-manager-87f5555f-t1xj7 1/1 Running 0 4h43m
+ cert-manager cert-manager-cainjector-8448ff8ddb-ww2sc 1/1 Running 0 4h43m
+ cert-manager cert-manager-webhook-5468b675b-fv2wk 1/1 Running 0 4h43m
kube-system aws-node-rf4wg 1/1 Running 0 4h43m
- kube-system aws-node-skkwh 1/1 Running 0 4h43m
+ kube-system aws-node-sk1wh 1/1 Running 0 4h43m
kube-system aws-privateca-issuer-b6fb8c5bd-hh8q4 1/1 Running 0 4h44m
kube-system coredns-5f9f955df6-qhr6p 1/1 Running 0 4h44m
kube-system coredns-5f9f955df6-tw8r7 1/1 Running 0 4h44m
@@ -243,7 +243,7 @@ The full documentation for this example can be found [here](https://docs.aws.ama
```text
NAME READY STATUS RESTARTS AGE
- appmesh-example-app-6946cdbdf6-gnxww 2/2 Running 0 54s
+ appmesh-example-app-6946cdbdf6-gn1ww 2/2 Running 0 54s
appmesh-example-app-6946cdbdf6-nx9tg 2/2 Running 0 54s
```
diff --git a/patterns/aws-vpc-cni-network-policy/README.md b/patterns/aws-vpc-cni-network-policy/README.md
index 1a41550939..b2db189038 100644
--- a/patterns/aws-vpc-cni-network-policy/README.md
+++ b/patterns/aws-vpc-cni-network-policy/README.md
@@ -26,11 +26,11 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
```text
NAMESPACE NAME READY STATUS RESTARTS AGE
[...]
- client client-xlffc 1/1 Running 0 5m19s
+ client client-xlf2c 1/1 Running 0 5m19s
[...]
management-ui management-ui-qrb2g 1/1 Running 0 5m24s
stars backend-sz87q 1/1 Running 0 5m23s
- stars frontend-cscnf 1/1 Running 0 5m21s
+ stars frontend-c1cnf 1/1 Running 0 5m21s
[...]
```
diff --git a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/backend-deploy.yaml b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/backend-deploy.yaml
index 766e0b573a..dc4d8d1dcd 100644
--- a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/backend-deploy.yaml
+++ b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/backend-deploy.yaml
@@ -14,12 +14,12 @@ spec:
role: backend
spec:
containers:
- - name: backend
- image: calico/star-probe:v0.1.0
- imagePullPolicy: Always
- command:
- - probe
- - --http-port=6379
- - --urls=http://frontend.stars:80/status,http://backend.stars:6379/status,http://client.client:9000/status
- ports:
- - containerPort: 6379
+ - name: backend
+ image: calico/star-probe:v0.1.0
+ imagePullPolicy: Always
+ command:
+ - probe
+ - --http-port=6379
+ - --urls=http://frontend.stars:80/status,http://backend.stars:6379/status,http://client.client:9000/status
+ ports:
+ - containerPort: 6379
diff --git a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/backend-svc.yaml b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/backend-svc.yaml
index 1298c3b74e..086ed83d9a 100644
--- a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/backend-svc.yaml
+++ b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/backend-svc.yaml
@@ -5,7 +5,7 @@ metadata:
namespace: stars
spec:
ports:
- - port: 6379
- targetPort: 6379
+ - port: 6379
+ targetPort: 6379
selector:
role: backend
diff --git a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/client-deploy.yaml b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/client-deploy.yaml
index 35c2d7caab..8276b6f116 100644
--- a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/client-deploy.yaml
+++ b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/client-deploy.yaml
@@ -14,11 +14,11 @@ spec:
role: client
spec:
containers:
- - name: client
- image: calico/star-probe:v0.1.0
- imagePullPolicy: Always
- command:
- - probe
- - --urls=http://frontend.stars:80/status,http://backend.stars:6379/status
- ports:
- - containerPort: 9000
+ - name: client
+ image: calico/star-probe:v0.1.0
+ imagePullPolicy: Always
+ command:
+ - probe
+ - --urls=http://frontend.stars:80/status,http://backend.stars:6379/status
+ ports:
+ - containerPort: 9000
diff --git a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/client-svc.yaml b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/client-svc.yaml
index a91ded3d1c..eed8f886de 100644
--- a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/client-svc.yaml
+++ b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/client-svc.yaml
@@ -5,7 +5,7 @@ metadata:
namespace: client
spec:
ports:
- - port: 9000
- targetPort: 9000
+ - port: 9000
+ targetPort: 9000
selector:
role: client
diff --git a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/frontend-deploy.yaml b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/frontend-deploy.yaml
index 5c0352c0d4..3c0ae7d9a3 100644
--- a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/frontend-deploy.yaml
+++ b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/frontend-deploy.yaml
@@ -14,12 +14,12 @@ spec:
role: frontend
spec:
containers:
- - name: frontend
- image: calico/star-probe:v0.1.0
- imagePullPolicy: Always
- command:
- - probe
- - --http-port=80
- - --urls=http://frontend.stars:80/status,http://backend.stars:6379/status,http://client.client:9000/status
- ports:
- - containerPort: 80
+ - name: frontend
+ image: calico/star-probe:v0.1.0
+ imagePullPolicy: Always
+ command:
+ - probe
+ - --http-port=80
+ - --urls=http://frontend.stars:80/status,http://backend.stars:6379/status,http://client.client:9000/status
+ ports:
+ - containerPort: 80
diff --git a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/frontend-svc.yaml b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/frontend-svc.yaml
index 51426395b7..ad0bbc7e4a 100644
--- a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/frontend-svc.yaml
+++ b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/frontend-svc.yaml
@@ -5,7 +5,7 @@ metadata:
namespace: stars
spec:
ports:
- - port: 80
- targetPort: 80
+ - port: 80
+ targetPort: 80
selector:
role: frontend
diff --git a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/management-ui-deploy.yaml b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/management-ui-deploy.yaml
index 391119d3e6..4ac076aea7 100644
--- a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/management-ui-deploy.yaml
+++ b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/management-ui-deploy.yaml
@@ -14,8 +14,8 @@ spec:
role: management-ui
spec:
containers:
- - name: management-ui
- image: calico/star-collect:v0.1.0
- imagePullPolicy: Always
- ports:
- - containerPort: 9001
+ - name: management-ui
+ image: calico/star-collect:v0.1.0
+ imagePullPolicy: Always
+ ports:
+ - containerPort: 9001
diff --git a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/management-ui-svc.yaml b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/management-ui-svc.yaml
index 9c0e64337d..aac690e6da 100644
--- a/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/management-ui-svc.yaml
+++ b/patterns/aws-vpc-cni-network-policy/charts/demo-application/templates/management-ui-svc.yaml
@@ -6,7 +6,7 @@ metadata:
spec:
type: LoadBalancer
ports:
- - port: 80
- targetPort: 9001
+ - port: 80
+ targetPort: 9001
selector:
role: management-ui
diff --git a/patterns/blue-green-upgrade/eks-blue/variables.tf b/patterns/blue-green-upgrade/eks-blue/variables.tf
index 77416b8ed8..95e45c3548 100644
--- a/patterns/blue-green-upgrade/eks-blue/variables.tf
+++ b/patterns/blue-green-upgrade/eks-blue/variables.tf
@@ -12,7 +12,7 @@ variable "environment_name" {
variable "ingress_type" {
type = string
- description = "Type of ingress to uses (alb | nginx | ...). this parameter will be sent to arocd via gitops bridge"
+ description = "Type of ingress to uses (alb | nginx | ...). this parameter will be sent to argocd via gitops bridge"
default = "alb"
}
diff --git a/patterns/blue-green-upgrade/eks-green/variables.tf b/patterns/blue-green-upgrade/eks-green/variables.tf
index 77416b8ed8..95e45c3548 100644
--- a/patterns/blue-green-upgrade/eks-green/variables.tf
+++ b/patterns/blue-green-upgrade/eks-green/variables.tf
@@ -12,7 +12,7 @@ variable "environment_name" {
variable "ingress_type" {
type = string
- description = "Type of ingress to uses (alb | nginx | ...). this parameter will be sent to arocd via gitops bridge"
+ description = "Type of ingress to uses (alb | nginx | ...). this parameter will be sent to argocd via gitops bridge"
default = "alb"
}
diff --git a/patterns/blue-green-upgrade/environment/README.md b/patterns/blue-green-upgrade/environment/README.md
index f5d2bf0236..b49fd1825a 100644
--- a/patterns/blue-green-upgrade/environment/README.md
+++ b/patterns/blue-green-upgrade/environment/README.md
@@ -1,8 +1,8 @@
-# Common Environement Infrastructure
+# Common Environment Infrastructure
## Table of content
-- [Common Environement Infrastructure](#common-environement-infrastructure)
+- [Common Environment Infrastructure](#common-environment-infrastructure)
- [Table of content](#table-of-content)
- [Getting Started](#getting-started)
- [Usage](#usage)
@@ -69,7 +69,7 @@ Example:
```
aws_acm_certificate_status = "ISSUED"
-aws_route53_zone = "eks-blueprint.eks.mydomain.org"
+aws_route53_zone = "eks-blueprint.eks.example.org"
vpc_id = "vpc-0d649baf641a8071e"
```
diff --git a/patterns/blue-green-upgrade/environment/main.tf b/patterns/blue-green-upgrade/environment/main.tf
index ee29c7803d..42bc7e968a 100644
--- a/patterns/blue-green-upgrade/environment/main.tf
+++ b/patterns/blue-green-upgrade/environment/main.tf
@@ -94,7 +94,6 @@ resource "random_password" "argocd" {
override_special = "!#$%&*()-_=+[]{}<>:?"
}
-#tfsec:ignore:aws-ssm-secret-use-customer-key
resource "aws_secretsmanager_secret" "argocd" {
name = "${local.argocd_secret_manager_name}.${local.name}"
recovery_window_in_days = 0 # Set to zero for this example to force delete during Terraform destroy
diff --git a/patterns/blue-green-upgrade/modules/eks_cluster/variables.tf b/patterns/blue-green-upgrade/modules/eks_cluster/variables.tf
index 087f7fd1b3..769c0061fe 100644
--- a/patterns/blue-green-upgrade/modules/eks_cluster/variables.tf
+++ b/patterns/blue-green-upgrade/modules/eks_cluster/variables.tf
@@ -12,7 +12,7 @@ variable "environment_name" {
variable "ingress_type" {
type = string
- description = "Type of ingress to uses (alb | nginx | ...). this parameter will be sent to arocd via gitops bridge"
+ description = "Type of ingress to uses (alb | nginx | ...). this parameter will be sent to argocd via gitops bridge"
default = "alb"
}
@@ -109,7 +109,7 @@ variable "argocd_route53_weight" {
}
variable "ecsfrontend_route53_weight" {
- description = "The Route53 weighted records weight for ecsdeo-frontend application"
+ description = "The Route53 weighted records weight for ecsdemo-frontend application"
type = string
default = "100"
}
diff --git a/patterns/blue-green-upgrade/terraform.tfvars.example b/patterns/blue-green-upgrade/terraform.tfvars.example
index 0d70039604..9f9cf18f20 100644
--- a/patterns/blue-green-upgrade/terraform.tfvars.example
+++ b/patterns/blue-green-upgrade/terraform.tfvars.example
@@ -2,7 +2,7 @@
aws_region = "eu-west-1"
environment_name = "eks-blueprint"
-hosted_zone_name = "eks.mydomain.org" # your Existing Hosted Zone
+hosted_zone_name = "eks.example.org" # your Existing Hosted Zone
eks_admin_role_name = "Admin" # Additional role admin in the cluster (usually the role I use in the AWS console)
#gitops_addons_org = "git@github.com:aws-samples"
diff --git a/patterns/fargate-serverless/README.md b/patterns/fargate-serverless/README.md
index 2efb07b769..0ecafec613 100644
--- a/patterns/fargate-serverless/README.md
+++ b/patterns/fargate-serverless/README.md
@@ -34,12 +34,12 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
```text
NAMESPACE NAME READY STATUS RESTARTS AGE
app-2048 app-2048-65bd744dfb-7g9rx 1/1 Running 0 2m34s
- app-2048 app-2048-65bd744dfb-nxcbm 1/1 Running 0 2m34s
+ app-2048 app-2048-65bd744dfb-n1cbm 1/1 Running 0 2m34s
app-2048 app-2048-65bd744dfb-z4b6z 1/1 Running 0 2m34s
- kube-system aws-load-balancer-controller-6cbdb58654-fvskt 1/1 Running 0 26m
+ kube-system aws-load-balancer-controller-6cbdb58654-f1skt 1/1 Running 0 26m
kube-system aws-load-balancer-controller-6cbdb58654-sc7dk 1/1 Running 0 26m
- kube-system coredns-7b7bddbc85-jmbv6 1/1 Running 0 26m
- kube-system coredns-7b7bddbc85-rgmzq 1/1 Running 0 26m
+ kube-system coredns-7b7bddbc85-j1bv6 1/1 Running 0 26m
+ kube-system coredns-7b7bddbc85-rg2zq 1/1 Running 0 26m
```
3. Validate the `aws-logging` configMap for Fargate Fluentbit was created:
@@ -118,10 +118,10 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
```json
[
"fargate-logs-flblogs.var.log.fluent-bit.log",
- "fargate-logs-kube.var.log.containers.aws-load-balancer-controller-7f989fc6c-grjsq_kube-system_aws-load-balancer-controller-feaa22b4cdaa71ecfc8355feb81d4b61ea85598a7bb57aef07667c767c6b98e4.log",
+ "fargate-logs-kube.var.log.containers.aws-load-balancer-controller-7f989fc6c-gr1sq_kube-system_aws-load-balancer-controller-feaa22b4cdaa71ecfc8355feb81d4b61ea85598a7bb57aef07667c767c6b98e4.log",
"fargate-logs-kube.var.log.containers.aws-load-balancer-controller-7f989fc6c-wzr46_kube-system_aws-load-balancer-controller-69075ea9ab3c7474eac2a1696d3a84a848a151420cd783d79aeef960b181567f.log",
- "fargate-logs-kube.var.log.containers.coredns-7b7bddbc85-8cxvq_kube-system_coredns-9e4f3ab435269a566bcbaa606c02c146ad58508e67cef09fa87d5c09e4ac0088.log",
- "fargate-logs-kube.var.log.containers.coredns-7b7bddbc85-gcjwp_kube-system_coredns-11016818361cd68c32bf8f0b1328f3d92a6d7b8cf5879bfe8b301f393cb011cc.log"
+ "fargate-logs-kube.var.log.containers.coredns-7b7bddbc85-8cx1q_kube-system_coredns-9e4f3ab435269a566bcbaa606c02c146ad58508e67cef09fa87d5c09e4ac0088.log",
+ "fargate-logs-kube.var.log.containers.coredns-7b7bddbc85-g1jwp_kube-system_coredns-11016818361cd68c32bf8f0b1328f3d92a6d7b8cf5879bfe8b301f393cb011cc.log"
]
```
diff --git a/patterns/fargate-serverless/main.tf b/patterns/fargate-serverless/main.tf
index f4fefdea75..9c9037e7d0 100644
--- a/patterns/fargate-serverless/main.tf
+++ b/patterns/fargate-serverless/main.tf
@@ -116,13 +116,13 @@ module "eks_blueprints_addons" {
resources = {
limits = {
cpu = "0.25"
- # We are targetting the smallest Task size of 512Mb, so we subtract 256Mb from the
+ # We are targeting the smallest Task size of 512Mb, so we subtract 256Mb from the
# request/limit to ensure we can fit within that task
memory = "256M"
}
requests = {
cpu = "0.25"
- # We are targetting the smallest Task size of 512Mb, so we subtract 256Mb from the
+ # We are targeting the smallest Task size of 512Mb, so we subtract 256Mb from the
# request/limit to ensure we can fit within that task
memory = "256M"
}
diff --git a/patterns/fully-private-cluster/README.md b/patterns/fully-private-cluster/README.md
index fdcbe3305e..57ff8e7662 100644
--- a/patterns/fully-private-cluster/README.md
+++ b/patterns/fully-private-cluster/README.md
@@ -49,14 +49,14 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
```text
NAMESPACE NAME READY STATUS RESTARTS AGE
- kube-system aws-node-jvn9x 1/1 Running 0 7m42s
- kube-system aws-node-mnjlf 1/1 Running 0 7m45s
+ kube-system aws-node-j2n9x 1/1 Running 0 7m42s
+ kube-system aws-node-m1jlf 1/1 Running 0 7m45s
kube-system aws-node-q458h 1/1 Running 0 7m49s
kube-system coredns-6c45d94f67-495rr 1/1 Running 0 14m
kube-system coredns-6c45d94f67-5c8tc 1/1 Running 0 14m
kube-system kube-proxy-47wfh 1/1 Running 0 8m32s
kube-system kube-proxy-f6chz 1/1 Running 0 8m30s
- kube-system kube-proxy-xcfkc 1/1 Running 0 8m31s
+ kube-system kube-proxy-x2fkc 1/1 Running 0 8m31s
```
## Destroy
diff --git a/patterns/gitops/getting-started-argocd/README.md b/patterns/gitops/getting-started-argocd/README.md
index 292978fa6d..6ac4df89f4 100644
--- a/patterns/gitops/getting-started-argocd/README.md
+++ b/patterns/gitops/getting-started-argocd/README.md
@@ -286,7 +286,7 @@ The expected output should look like the following:
```text
NAME CPU(cores) MEMORY(bytes)
-game-2048-66fb78b995-hqbjv 1m 2Mi
+game-2048-66fb78b995-h1bjv 1m 2Mi
```
Check the CPU and memory metrics for all pods for Addons and Workloads:
@@ -303,19 +303,19 @@ argocd argo-cd-argocd-application-controller-0 43m
argocd argo-cd-argocd-applicationset-controller-5db688844c-79skp 1m 25Mi
argocd argo-cd-argocd-dex-server-cd48d7bc-x7flf 1m 16Mi
argocd argo-cd-argocd-notifications-controller-7d7ccc6b9d-dg9r6 1m 17Mi
-argocd argo-cd-argocd-redis-7f89c69877-6mmcj 2m 3Mi
+argocd argo-cd-argocd-redis-7f89c69877-6m2cj 2m 3Mi
argocd argo-cd-argocd-repo-server-644b9b5668-m9ddg 8m 62Mi
argocd argo-cd-argocd-server-57cbbd6f94-lp4wx 2m 26Mi
-game-2048 game-2048-66fb78b995-hqbjv 1m 2Mi
+game-2048 game-2048-66fb78b995-h1bjv 1m 2Mi
kube-system aws-load-balancer-controller-8488df87c-4nxv6 2m 26Mi
kube-system aws-load-balancer-controller-8488df87c-zs4p6 1m 19Mi
kube-system aws-node-ck6vq 3m 57Mi
-kube-system aws-node-fvvsg 3m 56Mi
-kube-system coredns-59754897cf-5rlxp 1m 13Mi
+kube-system aws-node-fv2sg 3m 56Mi
+kube-system coredns-59754897cf-5r2xp 1m 13Mi
kube-system coredns-59754897cf-fn7jb 1m 13Mi
-kube-system kube-proxy-lzbdc 1m 11Mi
-kube-system kube-proxy-pdvlm 1m 12Mi
-kube-system metrics-server-5b76987ff-5gzsv 4m 17Mi
+kube-system kube-proxy-lz2dc 1m 11Mi
+kube-system kube-proxy-pd2lm 1m 12Mi
+kube-system metrics-server-5b76987ff-5g1sv 4m 17Mi
```
## Destroy the EKS Cluster
diff --git a/patterns/gitops/getting-started-argocd/bootstrap/workloads.yaml b/patterns/gitops/getting-started-argocd/bootstrap/workloads.yaml
index abebd17f9e..584a80b439 100644
--- a/patterns/gitops/getting-started-argocd/bootstrap/workloads.yaml
+++ b/patterns/gitops/getting-started-argocd/bootstrap/workloads.yaml
@@ -27,6 +27,6 @@ spec:
automated:
allowEmpty: true
syncOptions:
- - CreateNamespace=true
+ - CreateNamespace=true
retry:
limit: 60
diff --git a/patterns/gitops/getting-started-argocd/k8s/game-2048.yaml b/patterns/gitops/getting-started-argocd/k8s/game-2048.yaml
index c261a166dc..cf246a0ad0 100644
--- a/patterns/gitops/getting-started-argocd/k8s/game-2048.yaml
+++ b/patterns/gitops/getting-started-argocd/k8s/game-2048.yaml
@@ -1,3 +1,4 @@
+---
apiVersion: v1
kind: Namespace
metadata:
@@ -19,11 +20,11 @@ spec:
app.kubernetes.io/name: game-2048
spec:
containers:
- - image: public.ecr.aws/l6m2t8p7/docker-2048
- name: game-2048
- ports:
- - containerPort: 80
- name: http
+ - image: public.ecr.aws/l6m2t8p7/docker-2048
+ name: game-2048
+ ports:
+ - containerPort: 80
+ name: http
---
apiVersion: v1
kind: Service
@@ -53,10 +54,10 @@ spec:
rules:
- http:
paths:
- - path: /
- pathType: Prefix
- backend:
- service:
- name: game-2048
- port:
- name: http
+ - path: /
+ pathType: Prefix
+ backend:
+ service:
+ name: game-2048
+ port:
+ name: http
diff --git a/patterns/gitops/getting-started-argocd/main.tf b/patterns/gitops/getting-started-argocd/main.tf
index a4a0413d89..8ab48c046e 100644
--- a/patterns/gitops/getting-started-argocd/main.tf
+++ b/patterns/gitops/getting-started-argocd/main.tf
@@ -188,7 +188,7 @@ module "eks_blueprints_addons" {
################################################################################
# EKS Cluster
################################################################################
-#tfsec:ignore:aws-eks-enable-control-plane-logging
+
module "eks" {
source = "terraform-aws-modules/eks/aws"
version = "~> 19.13"
diff --git a/patterns/gitops/multi-cluster-hub-spoke-argocd/README.md b/patterns/gitops/multi-cluster-hub-spoke-argocd/README.md
index 72cd798fc8..cdeabdd22b 100644
--- a/patterns/gitops/multi-cluster-hub-spoke-argocd/README.md
+++ b/patterns/gitops/multi-cluster-hub-spoke-argocd/README.md
@@ -1,6 +1,6 @@
# Multi-Cluster centralized hub-spoke topology
-This tutorial guides you through deploying an Amazon EKS cluster with addons configured via ArgoCD in a Multi-Cluster Hub-Spoke topoloy, employing the [GitOps Bridge Pattern](https://github.com/gitops-bridge-dev).
+This tutorial guides you through deploying an Amazon EKS cluster with addons configured via ArgoCD in a Multi-Cluster Hub-Spoke topology, employing the [GitOps Bridge Pattern](https://github.com/gitops-bridge-dev).
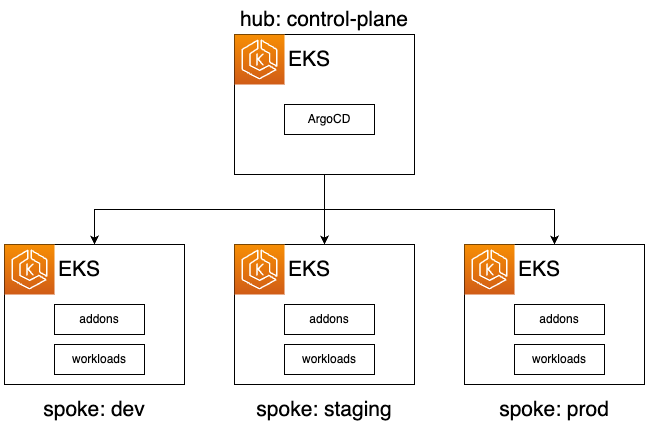 @@ -97,7 +97,7 @@ echo "ArgoCD Password: $(kubectl --context hub get secrets argocd-initial-admin-
echo "ArgoCD URL: https://$(kubectl --context hub get svc -n argocd argo-cd-argocd-server -o jsonpath='{.status.loadBalancer.ingress[0].hostname}')"
```
-## Verify that ArgoCD Service Accouts has the annotation for IRSA
+## Verify that ArgoCD Service Accounts has the annotation for IRSA
```shell
kubectl --context hub get sa -n argocd argocd-application-controller -o json | jq '.metadata.annotations."eks.amazonaws.com/role-arn"'
@@ -220,7 +220,7 @@ cd ../hub
## Fork GitOps Repositories
-To modify the `values.yaml` file or the helm chart version for addons, you'll need to fork tthe repository [aws-samples/eks-blueprints-add-ons](https://github.com/aws-samples/eks-blueprints-add-ons).
+To modify the `values.yaml` file or the helm chart version for addons, you'll need to fork the repository [aws-samples/eks-blueprints-add-ons](https://github.com/aws-samples/eks-blueprints-add-ons).
After forking, update the following environment variables to point to your forks, replacing the default values.
diff --git a/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf b/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf
index 254499b4ec..536172751f 100644
--- a/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf
+++ b/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf
@@ -223,7 +223,7 @@ module "eks_blueprints_addons" {
################################################################################
# EKS Cluster
################################################################################
-#tfsec:ignore:aws-eks-enable-control-plane-logging
+
module "eks" {
source = "terraform-aws-modules/eks/aws"
version = "~> 19.13"
diff --git a/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf b/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf
index 617769acb7..1946f47ff3 100644
--- a/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf
+++ b/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf
@@ -240,7 +240,7 @@ module "eks_blueprints_addons" {
################################################################################
# EKS Cluster
################################################################################
-#tfsec:ignore:aws-eks-enable-control-plane-logging
+
module "eks" {
source = "terraform-aws-modules/eks/aws"
version = "~> 19.13"
diff --git a/patterns/ipv6-eks-cluster/README.md b/patterns/ipv6-eks-cluster/README.md
index 370caa80c9..67897786f7 100644
--- a/patterns/ipv6-eks-cluster/README.md
+++ b/patterns/ipv6-eks-cluster/README.md
@@ -17,12 +17,12 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
```text
# Output should look like below
NAMESPACE NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
- kube-system aws-node-bhd2s 1/1 Running 0 3m5s 2600:1f13:6c4:a703:ecf8:3ac1:76b0:9303 ip-10-0-10-183.us-west-2.compute.internal
- kube-system aws-node-nmdgq 1/1 Running 0 3m21s 2600:1f13:6c4:a705:a929:f8d4:9350:1b20 ip-10-0-12-188.us-west-2.compute.internal
- kube-system coredns-799c5565b4-6wxrc 1/1 Running 0 10m 2600:1f13:6c4:a705:bbda:: ip-10-0-12-188.us-west-2.compute.internal
- kube-system coredns-799c5565b4-fjq4q 1/1 Running 0 10m 2600:1f13:6c4:a705:bbda::1 ip-10-0-12-188.us-west-2.compute.internal
+ kube-system aws-node-1hd2s 1/1 Running 0 3m5s 2600:1f13:6c4:a703:ecf8:3ac1:76b0:9303 ip-10-0-10-183.us-west-2.compute.internal
+ kube-system aws-node-2mdg 1/1 Running 0 3m21s 2600:1f13:6c4:a705:a929:f8d4:9350:1b20 ip-10-0-12-188.us-west-2.compute.internal
+ kube-system coredns-799c5565b4-6xrc 1/1 Running 0 10m 2600:1f13:6c4:a705:1bda:: ip-10-0-12-188.us-west-2.compute.internal
+ kube-system coredns-799c5565b4-fjq4q 1/1 Running 0 10m 2600:1f13:6c4:a705:1bda::1 ip-10-0-12-188.us-west-2.compute.internal
kube-system kube-proxy-58tp7 1/1 Running 0 4m25s 2600:1f13:6c4:a703:ecf8:3ac1:76b0:9303 ip-10-0-10-183.us-west-2.compute.internal
- kube-system kube-proxy-hqkgw 1/1 Running 0 4m25s 2600:1f13:6c4:a705:a929:f8d4:9350:1b20 ip-10-0-12-188.us-west-2.compute.internal
+ kube-system kube-proxy-3kgw 1/1 Running 0 4m25s 2600:1f13:6c4:a705:a929:f8d4:9350:1b20 ip-10-0-12-188.us-west-2.compute.internal
```
2. Test by listing all the nodes running currently; the `INTERNAL-IP` should be an IPv6 address.
diff --git a/patterns/istio-multi-cluster/0.certs-tool/README.md b/patterns/istio-multi-cluster/0.certs-tool/README.md
index 24b9d1304f..ad6dd42c21 100644
--- a/patterns/istio-multi-cluster/0.certs-tool/README.md
+++ b/patterns/istio-multi-cluster/0.certs-tool/README.md
@@ -1,4 +1,4 @@
-# Generating Certificates for Bootstrapping Multicluster / Mesh Expansion Chain of Trust
+# Generating Certificates for Bootstrapping Multi-cluster / Mesh Expansion Chain of Trust
The directory contains two Makefiles for generating new root, intermediate certificates and workload certificates:
- `Makefile.k8s.mk`: Creates certificates based on a root-ca from a k8s cluster. The current context in the default `kubeconfig` is used for accessing the cluster.
diff --git a/patterns/istio-multi-cluster/1.cluster1/README.md b/patterns/istio-multi-cluster/1.cluster1/README.md
index 45f0bb03bd..695f28a43f 100644
--- a/patterns/istio-multi-cluster/1.cluster1/README.md
+++ b/patterns/istio-multi-cluster/1.cluster1/README.md
@@ -60,7 +60,7 @@ kubectl get pods,svc -n istio-system
```
# Output should look like below
NAME READY STATUS RESTARTS AGE
-pod/istio-ingress-6f7c5dffd8-chkww 1/1 Running 0 48m
+pod/istio-ingress-6f7c5dffd8-4kww 1/1 Running 0 48m
pod/istiod-ff577f8b8-t9ww2 1/1 Running 0 48m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
@@ -235,25 +235,7 @@ kubectl exec -n sample -c sleep \
```
```
* processing: helloworld.sample:5000/hello
- % Total % Received % Xferd Average Speed Time Time Time Current
- Dload Upload Total Spent Left Speed
- 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0* Trying 172.20.26.38:5000...
-* Connected to helloworld.sample (172.20.26.38) port 5000
-> GET /hello HTTP/1.1
-> Host: helloworld.sample:5000
-> User-Agent: curl/8.2.0
-> Accept: */*
->
-< HTTP/1.1 200 OK
-< server: envoy
-< date: Fri, 21 Jul 2023 18:56:09 GMT
-< content-type: text/html; charset=utf-8
-< content-length: 58
-< x-envoy-upstream-service-time: 142
-<
-{ [58 bytes data]
-100 58 100 58 Hello version: v1, instance: helloworld-v1-b6c45f55-h592c
- 0 0 392 0 --:--:-- --:--:-- --:--:-- 394
+ ...
* Connection #0 to host helloworld.sample left intact
```
diff --git a/patterns/istio-multi-cluster/2.cluster2/main.tf b/patterns/istio-multi-cluster/2.cluster2/main.tf
index 613742f173..27956e249e 100644
--- a/patterns/istio-multi-cluster/2.cluster2/main.tf
+++ b/patterns/istio-multi-cluster/2.cluster2/main.tf
@@ -224,7 +224,7 @@ resource "helm_release" "istio_ingress" {
}
################################################################################
-# Isito certs for cross-cluster traffice
+# Istio certs for cross-cluster traffic
# https://istio.io/latest/docs/ops/deployment/deployment-models/#trust-within-a-mesh
# https://istio.io/latest/docs/ops/diagnostic-tools/multicluster/#trust-configuration
################################################################################
diff --git a/patterns/istio-multi-cluster/4.test-connectivity/istio-helloworld.yaml b/patterns/istio-multi-cluster/4.test-connectivity/istio-helloworld.yaml
index 06f6df18f5..e870420e6d 100644
--- a/patterns/istio-multi-cluster/4.test-connectivity/istio-helloworld.yaml
+++ b/patterns/istio-multi-cluster/4.test-connectivity/istio-helloworld.yaml
@@ -1,3 +1,4 @@
+---
apiVersion: v1
kind: Service
metadata:
@@ -7,8 +8,8 @@ metadata:
service: helloworld
spec:
ports:
- - port: 5000
- name: http
+ - port: 5000
+ name: http
selector:
app: helloworld
---
@@ -32,14 +33,14 @@ spec:
version: v1
spec:
containers:
- - name: helloworld
- image: docker.io/istio/examples-helloworld-v1
- resources:
- requests:
- cpu: "100m"
- imagePullPolicy: IfNotPresent #Always
- ports:
- - containerPort: 5000
+ - name: helloworld
+ image: docker.io/istio/examples-helloworld-v1
+ resources:
+ requests:
+ cpu: "100m"
+ imagePullPolicy: IfNotPresent #Always
+ ports:
+ - containerPort: 5000
---
apiVersion: apps/v1
kind: Deployment
@@ -61,11 +62,11 @@ spec:
version: v2
spec:
containers:
- - name: helloworld
- image: docker.io/istio/examples-helloworld-v2
- resources:
- requests:
- cpu: "100m"
- imagePullPolicy: IfNotPresent #Always
- ports:
- - containerPort: 5000
+ - name: helloworld
+ image: docker.io/istio/examples-helloworld-v2
+ resources:
+ requests:
+ cpu: "100m"
+ imagePullPolicy: IfNotPresent #Always
+ ports:
+ - containerPort: 5000
diff --git a/patterns/istio-multi-cluster/4.test-connectivity/istio-sleep.yaml b/patterns/istio-multi-cluster/4.test-connectivity/istio-sleep.yaml
index 570086b939..7ee33332a7 100644
--- a/patterns/istio-multi-cluster/4.test-connectivity/istio-sleep.yaml
+++ b/patterns/istio-multi-cluster/4.test-connectivity/istio-sleep.yaml
@@ -1,3 +1,4 @@
+---
# Copyright Istio Authors
#
# Licensed under the Apache License, Version 2.0 (the "License");
@@ -29,8 +30,8 @@ metadata:
service: sleep
spec:
ports:
- - port: 80
- name: http
+ - port: 80
+ name: http
selector:
app: sleep
---
@@ -51,16 +52,16 @@ spec:
terminationGracePeriodSeconds: 0
serviceAccountName: sleep
containers:
- - name: sleep
- image: curlimages/curl
- command: ["/bin/sleep", "infinity"]
- imagePullPolicy: IfNotPresent
- volumeMounts:
- - mountPath: /etc/sleep/tls
- name: secret-volume
+ - name: sleep
+ image: curlimages/curl
+ command: ["/bin/sleep", "infinity"]
+ imagePullPolicy: IfNotPresent
+ volumeMounts:
+ - mountPath: /etc/sleep/tls
+ name: secret-volume
volumes:
- - name: secret-volume
- secret:
- secretName: sleep-secret
- optional: true
+ - name: secret-volume
+ secret:
+ secretName: sleep-secret
+ optional: true
---
diff --git a/patterns/istio/README.md b/patterns/istio/README.md
index 5e32470c51..9d4b717a25 100644
--- a/patterns/istio/README.md
+++ b/patterns/istio/README.md
@@ -55,7 +55,7 @@ done
pod/istiod-ff577f8b8-c8ssk 1/1 Running 0 4m40s
pod/jaeger-58c79c85cd-n7bkx 1/1 Running 0 4m14s
pod/kiali-749d76d7bb-8kjg7 1/1 Running 0 4m14s
- pod/prometheus-5d5d6d6fc-sptxl 2/2 Running 0 4m15s
+ pod/prometheus-5d5d6d6fc-s1txl 2/2 Running 0 4m15s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/grafana ClusterIP 172.20.141.12 3000/TCP 4m14s
@@ -67,7 +67,7 @@ done
service/zipkin ClusterIP 172.20.221.157 9411/TCP 4m15s
NAME READY STATUS RESTARTS AGE
- pod/istio-ingress-6f7c5dffd8-glszr 1/1 Running 0 4m28s
+ pod/istio-ingress-6f7c5dffd8-g1szr 1/1 Running 0 4m28s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/istio-ingress LoadBalancer 172.20.104.27 k8s-istioing-istioing-844c89b6c2-875b8c9a4b4e9365.elb.us-west-2.amazonaws.com 15021:32760/TCP,80:31496/TCP,443:32534/TCP 4m28s
@@ -271,25 +271,7 @@ kubectl port-forward svc/jaeger 16686:16686 -n istio-system
```text
* processing: helloworld.sample:5000/hello
- % Total % Received % Xferd Average Speed Time Time Time Current
- Dload Upload Total Spent Left Speed
- 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0* Trying 172.20.26.38:5000...
- * Connected to helloworld.sample (172.20.26.38) port 5000
- > GET /hello HTTP/1.1
- > Host: helloworld.sample:5000
- > User-Agent: curl/8.2.0
- > Accept: */*
- >
- < HTTP/1.1 200 OK
- < server: envoy
- < date: Fri, 21 Jul 2023 18:56:09 GMT
- < content-type: text/html; charset=utf-8
- < content-length: 58
- < x-envoy-upstream-service-time: 142
- <
- { [58 bytes data]
- 100 58 100 58 Hello version: v1, instance: helloworld-v1-b6c45f55-h592c
- 0 0 392 0 --:--:-- --:--:-- --:--:-- 394
+ ...
* Connection #0 to host helloworld.sample left intact
```
diff --git a/patterns/karpenter/example.yaml b/patterns/karpenter/example.yaml
index 25ee0fef3c..0ac0500df7 100644
--- a/patterns/karpenter/example.yaml
+++ b/patterns/karpenter/example.yaml
@@ -1,4 +1,3 @@
----
apiVersion: apps/v1
kind: Deployment
metadata:
diff --git a/patterns/karpenter/main.tf b/patterns/karpenter/main.tf
index 556f51267d..da71d9dd5b 100644
--- a/patterns/karpenter/main.tf
+++ b/patterns/karpenter/main.tf
@@ -136,13 +136,13 @@ module "eks_blueprints_addons" {
resources = {
limits = {
cpu = "0.25"
- # We are targetting the smallest Task size of 512Mb, so we subtract 256Mb from the
+ # We are targeting the smallest Task size of 512Mb, so we subtract 256Mb from the
# request/limit to ensure we can fit within that task
memory = "256M"
}
requests = {
cpu = "0.25"
- # We are targetting the smallest Task size of 512Mb, so we subtract 256Mb from the
+ # We are targeting the smallest Task size of 512Mb, so we subtract 256Mb from the
# request/limit to ensure we can fit within that task
memory = "256M"
}
diff --git a/patterns/kubecost/README.md b/patterns/kubecost/README.md
index d9601cb105..eca20a221a 100644
--- a/patterns/kubecost/README.md
+++ b/patterns/kubecost/README.md
@@ -1,6 +1,6 @@
# Kubecost with AWS Cloud Billing Integration
-This pattern demostrates how to install and configure Kubecost with AWS CUR report.
+This pattern demonstrates how to install and configure Kubecost with AWS CUR report.
The terraform code was created following the official Kubecost documentation for [aws cloud billing integration](https://docs.kubecost.com/install-and-configure/install/cloud-integration/aws-cloud-integrations).
## Prerequisites
@@ -22,7 +22,7 @@ Once all of the resources have successfully been provisioned, the following comm
aws eks --region update-kubeconfig --name
```
-This command will create a S3 bucket with prefix `kubecost-` and a Cost and Usage Report (CUR). Within 24h The CUR will generate a CloudFormation teamplate file called `crawler-cfn.yml` in the S3 bucket. Once that file is generated, navigate to:
+This command will create a S3 bucket with prefix `kubecost-` and a Cost and Usage Report (CUR). Within 24h The CUR will generate a CloudFormation template file called `crawler-cfn.yml` in the S3 bucket. Once that file is generated, navigate to:
```
cd run-me-in-24h/
@@ -45,7 +45,7 @@ Navigate to Settings -> Diagnostics -> View Full Diagnostics
Expected result:

-> [!NOTE]
+> [!NOTE]
> Spot Data Feed is included in Savings Plan, Reserved Instance, and Out-Of-Cluster.
## Destroy
diff --git a/patterns/multi-tenancy-with-teams/main.tf b/patterns/multi-tenancy-with-teams/main.tf
index 257bfe9f57..756ee028d3 100644
--- a/patterns/multi-tenancy-with-teams/main.tf
+++ b/patterns/multi-tenancy-with-teams/main.tf
@@ -174,7 +174,7 @@ module "eks_blueprints_dev_teams" {
}
################################################################################
-# Supporting Resoruces
+# Supporting Resources
################################################################################
module "vpc" {
diff --git a/patterns/privatelink-access/README.md b/patterns/privatelink-access/README.md
index 1124f2012d..81619eb6b8 100644
--- a/patterns/privatelink-access/README.md
+++ b/patterns/privatelink-access/README.md
@@ -90,7 +90,7 @@ kubectl get pods -A
NAMESPACE NAME READY STATUS RESTARTS AGE
kube-system aws-node-4f8g8 1/1 Running 0 1m
kube-system coredns-6ff9c46cd8-59sqp 1/1 Running 0 1m
-kube-system coredns-6ff9c46cd8-svnpb 1/1 Running 0 2m
+kube-system coredns-6ff9c46cd8-1npb 1/1 Running 0 2m
kube-system kube-proxy-mm2zc 1/1 Running 0 1m
```
diff --git a/patterns/sso-iam-identity-center/README.md b/patterns/sso-iam-identity-center/README.md
index 537980697a..377d7ecb1a 100644
--- a/patterns/sso-iam-identity-center/README.md
+++ b/patterns/sso-iam-identity-center/README.md
@@ -8,7 +8,7 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
## Validate
-After the `terraform` commands are executed sucessfully, check if the newly created users are active.
+After the `terraform` commands are executed successfully, check if the newly created users are active.
To do that use the link provided in the email invite - *if you added a valid email address for your users either in your Terraform code or IAM Identity Center Console* - or go to the [IAM Identity Center Console](https://console.aws.amazon.com/singlesignon/home/), in the *Users* dashboard on the left hand side menu, then select the user, and click on *Reset password* button on the upper right corner. Choose the option to *Generate a one-time password and share the password with the user*.
@@ -80,16 +80,16 @@ With the `kubeconfig` configured, you'll be able to run `kubectl` commands in yo
kubectl get pods -A
NAMESPACE NAME READY STATUS RESTARTS AGE
amazon-guardduty aws-guardduty-agent-bl2v2 1/1 Running 0 3h54m
-amazon-guardduty aws-guardduty-agent-sqvcx 1/1 Running 0 3h54m
+amazon-guardduty aws-guardduty-agent-s2vcx 1/1 Running 0 3h54m
amazon-guardduty aws-guardduty-agent-w8gfc 1/1 Running 0 3h54m
kube-system aws-node-m9hmd 1/1 Running 0 3h53m
kube-system aws-node-w42b8 1/1 Running 0 3h53m
kube-system aws-node-wm6rm 1/1 Running 0 3h53m
kube-system coredns-6ff9c46cd8-94jlr 1/1 Running 0 3h59m
-kube-system coredns-6ff9c46cd8-nwmrb 1/1 Running 0 3h59m
+kube-system coredns-6ff9c46cd8-n2mrb 1/1 Running 0 3h59m
kube-system kube-proxy-7fb86 1/1 Running 0 3h54m
kube-system kube-proxy-p4f5g 1/1 Running 0 3h54m
-kube-system kube-proxy-qkfmc 1/1 Running 0 3h54m
+kube-system kube-proxy-q1fmc 1/1 Running 0 3h54m
```
You can also use the `configure_kubectl` output to assume the *Cluster creator* role with `cluster-admin` access.
diff --git a/patterns/sso-iam-identity-center/main.tf b/patterns/sso-iam-identity-center/main.tf
index 187e01adbd..5c599f5cee 100644
--- a/patterns/sso-iam-identity-center/main.tf
+++ b/patterns/sso-iam-identity-center/main.tf
@@ -21,7 +21,6 @@ locals {
# Cluster
################################################################################
-#tfsec:ignore:aws-eks-enable-control-plane-logging
module "eks" {
source = "terraform-aws-modules/eks/aws"
version = "~> 19.21"
diff --git a/patterns/sso-okta/README.md b/patterns/sso-okta/README.md
index b25294bd94..480cf75395 100644
--- a/patterns/sso-okta/README.md
+++ b/patterns/sso-okta/README.md
@@ -8,7 +8,7 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
## Validate
-After the `terraform` commands are executed sucessfully, check if the newly created users are active.
+After the `terraform` commands are executed successfully, check if the newly created users are active.
To do that use the link provided in the email invite if you added a valid email address for your users, or go to the [Okta Admin Dashboard](https://dev-ORGID-admin.okta.com/admin/users/), select the user, and click on *Set Password and Activate* button.
@@ -34,16 +34,16 @@ The read-only user has a `cluster-viewer` Kubernetes role bound to it's group, w
kubectl get pods -A
NAMESPACE NAME READY STATUS RESTARTS AGE
amazon-guardduty aws-guardduty-agent-bl2v2 1/1 Running 0 3h54m
-amazon-guardduty aws-guardduty-agent-sqvcx 1/1 Running 0 3h54m
+amazon-guardduty aws-guardduty-agent-s1vcx 1/1 Running 0 3h54m
amazon-guardduty aws-guardduty-agent-w8gfc 1/1 Running 0 3h54m
kube-system aws-node-m9hmd 1/1 Running 0 3h53m
kube-system aws-node-w42b8 1/1 Running 0 3h53m
kube-system aws-node-wm6rm 1/1 Running 0 3h53m
kube-system coredns-6ff9c46cd8-94jlr 1/1 Running 0 3h59m
-kube-system coredns-6ff9c46cd8-nwmrb 1/1 Running 0 3h59m
+kube-system coredns-6ff9c46cd8-nw2rb 1/1 Running 0 3h59m
kube-system kube-proxy-7fb86 1/1 Running 0 3h54m
kube-system kube-proxy-p4f5g 1/1 Running 0 3h54m
-kube-system kube-proxy-qkfmc 1/1 Running 0 3h54m
+kube-system kube-proxy-qk2mc 1/1 Running 0 3h54m
```
You can also use the `configure_kubectl` output to assume the *Cluster creator* role with `cluster-admin` access.
@@ -52,7 +52,7 @@ You can also use the `configure_kubectl` output to assume the *Cluster creator*
configure_kubectl = "aws eks --region us-west-2 update-kubeconfig --name okta"
```
-It's also possible to preconfigure your `kubeconfig` using the `okta_login` output. This will also require you to authenticate in a browser window.
+It's also possible to pre-configure your `kubeconfig` using the `okta_login` output. This will also require you to authenticate in a browser window.
```
okta_login = "kubectl oidc-login setup --oidc-issuer-url=https://dev-ORGID.okta.com/oauth2/1234567890abcdefghij--oidc-client-id=1234567890abcdefghij"
diff --git a/patterns/sso-okta/main.tf b/patterns/sso-okta/main.tf
index 8d4ec7e5aa..2e666d48a5 100644
--- a/patterns/sso-okta/main.tf
+++ b/patterns/sso-okta/main.tf
@@ -21,7 +21,6 @@ locals {
# Cluster
################################################################################
-#tfsec:ignore:aws-eks-enable-control-plane-logging
module "eks" {
source = "terraform-aws-modules/eks/aws"
version = "~> 20.0"
diff --git a/patterns/stateful/README.md b/patterns/stateful/README.md
index dd7a20689a..4d75c2bc42 100644
--- a/patterns/stateful/README.md
+++ b/patterns/stateful/README.md
@@ -159,7 +159,7 @@ The following command will update the `kubeconfig` on your local machine and all
# Output should look similar to below
NAME PROVIDER BUCKET/PREFIX PHASE LAST VALIDATED ACCESS MODE DEFAULT
- default aws velero-ssqwm44hvofzb32d Available 2022-05-22 10:53:26 -0400 EDT ReadWrite true
+ default aws velero-ss1wm44hv1fzb32d Available 2022-05-22 10:53:26 -0400 EDT ReadWrite true
```
## Destroy
diff --git a/patterns/stateful/main.tf b/patterns/stateful/main.tf
index 79c16dfd31..807ee986be 100644
--- a/patterns/stateful/main.tf
+++ b/patterns/stateful/main.tf
@@ -105,7 +105,7 @@ module "eks" {
}
# This user data mounts the containerd directories to the second EBS volume which
- # is dedicated to just contianerd. You can read more about the practice and why
+ # is dedicated to just containerd. You can read more about the practice and why
# here https://aws.github.io/aws-eks-best-practices/scalability/docs/data-plane/#use-multiple-ebs-volumes-for-containers
# and https://github.com/containerd/containerd/blob/main/docs/ops.md#base-configuration
pre_bootstrap_user_data = <<-EOT
@@ -322,7 +322,6 @@ module "vpc" {
tags = local.tags
}
-#tfsec:ignore:*
module "velero_backup_s3_bucket" {
source = "terraform-aws-modules/s3-bucket/aws"
version = "~> 3.0"
@@ -377,7 +376,7 @@ module "efs" {
security_group_vpc_id = module.vpc.vpc_id
security_group_rules = {
vpc = {
- # relying on the defaults provdied for EFS/NFS (2049/TCP + ingress)
+ # relying on the defaults provided for EFS/NFS (2049/TCP + ingress)
description = "NFS ingress from VPC private subnets"
cidr_blocks = module.vpc.private_subnets_cidr_blocks
}
diff --git a/patterns/vpc-lattice/client-server-communication/README.md b/patterns/vpc-lattice/client-server-communication/README.md
index e79a725494..b058dcb287 100644
--- a/patterns/vpc-lattice/client-server-communication/README.md
+++ b/patterns/vpc-lattice/client-server-communication/README.md
@@ -4,7 +4,7 @@ This pattern demonstrates how to expose an EKS cluster hosted application to an
## Scenario
-With this soluton we showcase how to configure Amazon VPC Lattice using the AWS Gateway API Controller in order to manage Amazon VPC Lattice resources through native K8S Gateway API objects. This pattern deploys two distinct VPCs with a client application running in one of them and a server application in the other. The server application is deployed inside an EKS cluster and made exposed to the client application through Amazon VPC Lattice which establishes connectivity between the two applications. Further we demonstrate how to configure a custom domain name for the exposed service using Amazon Route53 and the external-dns project.
+With this solution we showcase how to configure Amazon VPC Lattice using the AWS Gateway API Controller in order to manage Amazon VPC Lattice resources through native K8S Gateway API objects. This pattern deploys two distinct VPCs with a client application running in one of them and a server application in the other. The server application is deployed inside an EKS cluster and made exposed to the client application through Amazon VPC Lattice which establishes connectivity between the two applications. Further we demonstrate how to configure a custom domain name for the exposed service using Amazon Route53 and the external-dns project.

@@ -15,11 +15,11 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
## Validate
-In order to test the connectivty between the client and server, please follow the steps outlined below:
+In order to test the connectivity between the client and server, please follow the steps outlined below:
1. Login to the management console of your AWS account and navigate to the EC2 service
2. Select your the EC2 Instance with the name **client**, click **Connect**, choose **Session Manager** and click **Connect**
-3. Within the console test the connecvity to the server application by entering the following command:
+3. Within the console test the connectivity to the server application by entering the following command:
```sh
$ curl -i http://server.example.com
diff --git a/patterns/vpc-lattice/client-server-communication/charts/demo-application/templates/deployment.yaml b/patterns/vpc-lattice/client-server-communication/charts/demo-application/templates/deployment.yaml
index 1b8e744907..0f1fabd93a 100644
--- a/patterns/vpc-lattice/client-server-communication/charts/demo-application/templates/deployment.yaml
+++ b/patterns/vpc-lattice/client-server-communication/charts/demo-application/templates/deployment.yaml
@@ -15,8 +15,8 @@ spec:
app: server
spec:
containers:
- - name: server
- image: public.ecr.aws/x2j8p8w7/http-server:latest
- env:
- - name: PodName
- value: "server pod"
+ - name: server
+ image: public.ecr.aws/x2j8p8w7/http-server:latest
+ env:
+ - name: PodName
+ value: "server pod"
diff --git a/patterns/wireguard-with-cilium/README.md b/patterns/wireguard-with-cilium/README.md
index 0cfbeacb88..c558968885 100644
--- a/patterns/wireguard-with-cilium/README.md
+++ b/patterns/wireguard-with-cilium/README.md
@@ -49,7 +49,7 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
CNI Chaining: aws-cni
Cilium: Ok 1.14.2 (v1.14.2-a6748946)
NodeMonitor: Listening for events on 2 CPUs with 64x4096 of shared memory
- Cilium health daemon: Ok
+ Cilium health daemon: Ok
IPAM: IPv4: 1/254 allocated from 10.0.0.0/24,
IPv4 BIG TCP: Disabled
IPv6 BIG TCP: Disabled
diff --git a/patterns/wireguard-with-cilium/example.yaml b/patterns/wireguard-with-cilium/example.yaml
index 77fb7c36b4..e9c4deea9d 100644
--- a/patterns/wireguard-with-cilium/example.yaml
+++ b/patterns/wireguard-with-cilium/example.yaml
@@ -11,12 +11,12 @@ spec:
- name: server
image: nginx
topologySpreadConstraints:
- - maxSkew: 1
- topologyKey: "kubernetes.io/hostname"
- whenUnsatisfiable: DoNotSchedule
- labelSelector:
- matchLabels:
- blog: wireguard
+ - maxSkew: 1
+ topologyKey: "kubernetes.io/hostname"
+ whenUnsatisfiable: DoNotSchedule
+ labelSelector:
+ matchLabels:
+ blog: wireguard
---
apiVersion: v1
kind: Service
@@ -26,7 +26,7 @@ spec:
selector:
name: server
ports:
- - port: 80
+ - port: 80
sessionAffinity: ClientIP
sessionAffinityConfig:
clientIP:
@@ -45,10 +45,10 @@ spec:
image: busybox
command: ["watch", "wget", "server"]
topologySpreadConstraints:
- - maxSkew: 1
- topologyKey: "kubernetes.io/hostname"
- whenUnsatisfiable: DoNotSchedule
- labelSelector:
- matchLabels:
- blog: wireguard
+ - maxSkew: 1
+ topologyKey: "kubernetes.io/hostname"
+ whenUnsatisfiable: DoNotSchedule
+ labelSelector:
+ matchLabels:
+ blog: wireguard
---
@@ -97,7 +97,7 @@ echo "ArgoCD Password: $(kubectl --context hub get secrets argocd-initial-admin-
echo "ArgoCD URL: https://$(kubectl --context hub get svc -n argocd argo-cd-argocd-server -o jsonpath='{.status.loadBalancer.ingress[0].hostname}')"
```
-## Verify that ArgoCD Service Accouts has the annotation for IRSA
+## Verify that ArgoCD Service Accounts has the annotation for IRSA
```shell
kubectl --context hub get sa -n argocd argocd-application-controller -o json | jq '.metadata.annotations."eks.amazonaws.com/role-arn"'
@@ -220,7 +220,7 @@ cd ../hub
## Fork GitOps Repositories
-To modify the `values.yaml` file or the helm chart version for addons, you'll need to fork tthe repository [aws-samples/eks-blueprints-add-ons](https://github.com/aws-samples/eks-blueprints-add-ons).
+To modify the `values.yaml` file or the helm chart version for addons, you'll need to fork the repository [aws-samples/eks-blueprints-add-ons](https://github.com/aws-samples/eks-blueprints-add-ons).
After forking, update the following environment variables to point to your forks, replacing the default values.
diff --git a/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf b/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf
index 254499b4ec..536172751f 100644
--- a/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf
+++ b/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf
@@ -223,7 +223,7 @@ module "eks_blueprints_addons" {
################################################################################
# EKS Cluster
################################################################################
-#tfsec:ignore:aws-eks-enable-control-plane-logging
+
module "eks" {
source = "terraform-aws-modules/eks/aws"
version = "~> 19.13"
diff --git a/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf b/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf
index 617769acb7..1946f47ff3 100644
--- a/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf
+++ b/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf
@@ -240,7 +240,7 @@ module "eks_blueprints_addons" {
################################################################################
# EKS Cluster
################################################################################
-#tfsec:ignore:aws-eks-enable-control-plane-logging
+
module "eks" {
source = "terraform-aws-modules/eks/aws"
version = "~> 19.13"
diff --git a/patterns/ipv6-eks-cluster/README.md b/patterns/ipv6-eks-cluster/README.md
index 370caa80c9..67897786f7 100644
--- a/patterns/ipv6-eks-cluster/README.md
+++ b/patterns/ipv6-eks-cluster/README.md
@@ -17,12 +17,12 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
```text
# Output should look like below
NAMESPACE NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
- kube-system aws-node-bhd2s 1/1 Running 0 3m5s 2600:1f13:6c4:a703:ecf8:3ac1:76b0:9303 ip-10-0-10-183.us-west-2.compute.internal
- kube-system aws-node-nmdgq 1/1 Running 0 3m21s 2600:1f13:6c4:a705:a929:f8d4:9350:1b20 ip-10-0-12-188.us-west-2.compute.internal
- kube-system coredns-799c5565b4-6wxrc 1/1 Running 0 10m 2600:1f13:6c4:a705:bbda:: ip-10-0-12-188.us-west-2.compute.internal
- kube-system coredns-799c5565b4-fjq4q 1/1 Running 0 10m 2600:1f13:6c4:a705:bbda::1 ip-10-0-12-188.us-west-2.compute.internal
+ kube-system aws-node-1hd2s 1/1 Running 0 3m5s 2600:1f13:6c4:a703:ecf8:3ac1:76b0:9303 ip-10-0-10-183.us-west-2.compute.internal
+ kube-system aws-node-2mdg 1/1 Running 0 3m21s 2600:1f13:6c4:a705:a929:f8d4:9350:1b20 ip-10-0-12-188.us-west-2.compute.internal
+ kube-system coredns-799c5565b4-6xrc 1/1 Running 0 10m 2600:1f13:6c4:a705:1bda:: ip-10-0-12-188.us-west-2.compute.internal
+ kube-system coredns-799c5565b4-fjq4q 1/1 Running 0 10m 2600:1f13:6c4:a705:1bda::1 ip-10-0-12-188.us-west-2.compute.internal
kube-system kube-proxy-58tp7 1/1 Running 0 4m25s 2600:1f13:6c4:a703:ecf8:3ac1:76b0:9303 ip-10-0-10-183.us-west-2.compute.internal
- kube-system kube-proxy-hqkgw 1/1 Running 0 4m25s 2600:1f13:6c4:a705:a929:f8d4:9350:1b20 ip-10-0-12-188.us-west-2.compute.internal
+ kube-system kube-proxy-3kgw 1/1 Running 0 4m25s 2600:1f13:6c4:a705:a929:f8d4:9350:1b20 ip-10-0-12-188.us-west-2.compute.internal
```
2. Test by listing all the nodes running currently; the `INTERNAL-IP` should be an IPv6 address.
diff --git a/patterns/istio-multi-cluster/0.certs-tool/README.md b/patterns/istio-multi-cluster/0.certs-tool/README.md
index 24b9d1304f..ad6dd42c21 100644
--- a/patterns/istio-multi-cluster/0.certs-tool/README.md
+++ b/patterns/istio-multi-cluster/0.certs-tool/README.md
@@ -1,4 +1,4 @@
-# Generating Certificates for Bootstrapping Multicluster / Mesh Expansion Chain of Trust
+# Generating Certificates for Bootstrapping Multi-cluster / Mesh Expansion Chain of Trust
The directory contains two Makefiles for generating new root, intermediate certificates and workload certificates:
- `Makefile.k8s.mk`: Creates certificates based on a root-ca from a k8s cluster. The current context in the default `kubeconfig` is used for accessing the cluster.
diff --git a/patterns/istio-multi-cluster/1.cluster1/README.md b/patterns/istio-multi-cluster/1.cluster1/README.md
index 45f0bb03bd..695f28a43f 100644
--- a/patterns/istio-multi-cluster/1.cluster1/README.md
+++ b/patterns/istio-multi-cluster/1.cluster1/README.md
@@ -60,7 +60,7 @@ kubectl get pods,svc -n istio-system
```
# Output should look like below
NAME READY STATUS RESTARTS AGE
-pod/istio-ingress-6f7c5dffd8-chkww 1/1 Running 0 48m
+pod/istio-ingress-6f7c5dffd8-4kww 1/1 Running 0 48m
pod/istiod-ff577f8b8-t9ww2 1/1 Running 0 48m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
@@ -235,25 +235,7 @@ kubectl exec -n sample -c sleep \
```
```
* processing: helloworld.sample:5000/hello
- % Total % Received % Xferd Average Speed Time Time Time Current
- Dload Upload Total Spent Left Speed
- 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0* Trying 172.20.26.38:5000...
-* Connected to helloworld.sample (172.20.26.38) port 5000
-> GET /hello HTTP/1.1
-> Host: helloworld.sample:5000
-> User-Agent: curl/8.2.0
-> Accept: */*
->
-< HTTP/1.1 200 OK
-< server: envoy
-< date: Fri, 21 Jul 2023 18:56:09 GMT
-< content-type: text/html; charset=utf-8
-< content-length: 58
-< x-envoy-upstream-service-time: 142
-<
-{ [58 bytes data]
-100 58 100 58 Hello version: v1, instance: helloworld-v1-b6c45f55-h592c
- 0 0 392 0 --:--:-- --:--:-- --:--:-- 394
+ ...
* Connection #0 to host helloworld.sample left intact
```
diff --git a/patterns/istio-multi-cluster/2.cluster2/main.tf b/patterns/istio-multi-cluster/2.cluster2/main.tf
index 613742f173..27956e249e 100644
--- a/patterns/istio-multi-cluster/2.cluster2/main.tf
+++ b/patterns/istio-multi-cluster/2.cluster2/main.tf
@@ -224,7 +224,7 @@ resource "helm_release" "istio_ingress" {
}
################################################################################
-# Isito certs for cross-cluster traffice
+# Istio certs for cross-cluster traffic
# https://istio.io/latest/docs/ops/deployment/deployment-models/#trust-within-a-mesh
# https://istio.io/latest/docs/ops/diagnostic-tools/multicluster/#trust-configuration
################################################################################
diff --git a/patterns/istio-multi-cluster/4.test-connectivity/istio-helloworld.yaml b/patterns/istio-multi-cluster/4.test-connectivity/istio-helloworld.yaml
index 06f6df18f5..e870420e6d 100644
--- a/patterns/istio-multi-cluster/4.test-connectivity/istio-helloworld.yaml
+++ b/patterns/istio-multi-cluster/4.test-connectivity/istio-helloworld.yaml
@@ -1,3 +1,4 @@
+---
apiVersion: v1
kind: Service
metadata:
@@ -7,8 +8,8 @@ metadata:
service: helloworld
spec:
ports:
- - port: 5000
- name: http
+ - port: 5000
+ name: http
selector:
app: helloworld
---
@@ -32,14 +33,14 @@ spec:
version: v1
spec:
containers:
- - name: helloworld
- image: docker.io/istio/examples-helloworld-v1
- resources:
- requests:
- cpu: "100m"
- imagePullPolicy: IfNotPresent #Always
- ports:
- - containerPort: 5000
+ - name: helloworld
+ image: docker.io/istio/examples-helloworld-v1
+ resources:
+ requests:
+ cpu: "100m"
+ imagePullPolicy: IfNotPresent #Always
+ ports:
+ - containerPort: 5000
---
apiVersion: apps/v1
kind: Deployment
@@ -61,11 +62,11 @@ spec:
version: v2
spec:
containers:
- - name: helloworld
- image: docker.io/istio/examples-helloworld-v2
- resources:
- requests:
- cpu: "100m"
- imagePullPolicy: IfNotPresent #Always
- ports:
- - containerPort: 5000
+ - name: helloworld
+ image: docker.io/istio/examples-helloworld-v2
+ resources:
+ requests:
+ cpu: "100m"
+ imagePullPolicy: IfNotPresent #Always
+ ports:
+ - containerPort: 5000
diff --git a/patterns/istio-multi-cluster/4.test-connectivity/istio-sleep.yaml b/patterns/istio-multi-cluster/4.test-connectivity/istio-sleep.yaml
index 570086b939..7ee33332a7 100644
--- a/patterns/istio-multi-cluster/4.test-connectivity/istio-sleep.yaml
+++ b/patterns/istio-multi-cluster/4.test-connectivity/istio-sleep.yaml
@@ -1,3 +1,4 @@
+---
# Copyright Istio Authors
#
# Licensed under the Apache License, Version 2.0 (the "License");
@@ -29,8 +30,8 @@ metadata:
service: sleep
spec:
ports:
- - port: 80
- name: http
+ - port: 80
+ name: http
selector:
app: sleep
---
@@ -51,16 +52,16 @@ spec:
terminationGracePeriodSeconds: 0
serviceAccountName: sleep
containers:
- - name: sleep
- image: curlimages/curl
- command: ["/bin/sleep", "infinity"]
- imagePullPolicy: IfNotPresent
- volumeMounts:
- - mountPath: /etc/sleep/tls
- name: secret-volume
+ - name: sleep
+ image: curlimages/curl
+ command: ["/bin/sleep", "infinity"]
+ imagePullPolicy: IfNotPresent
+ volumeMounts:
+ - mountPath: /etc/sleep/tls
+ name: secret-volume
volumes:
- - name: secret-volume
- secret:
- secretName: sleep-secret
- optional: true
+ - name: secret-volume
+ secret:
+ secretName: sleep-secret
+ optional: true
---
diff --git a/patterns/istio/README.md b/patterns/istio/README.md
index 5e32470c51..9d4b717a25 100644
--- a/patterns/istio/README.md
+++ b/patterns/istio/README.md
@@ -55,7 +55,7 @@ done
pod/istiod-ff577f8b8-c8ssk 1/1 Running 0 4m40s
pod/jaeger-58c79c85cd-n7bkx 1/1 Running 0 4m14s
pod/kiali-749d76d7bb-8kjg7 1/1 Running 0 4m14s
- pod/prometheus-5d5d6d6fc-sptxl 2/2 Running 0 4m15s
+ pod/prometheus-5d5d6d6fc-s1txl 2/2 Running 0 4m15s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/grafana ClusterIP 172.20.141.12 3000/TCP 4m14s
@@ -67,7 +67,7 @@ done
service/zipkin ClusterIP 172.20.221.157 9411/TCP 4m15s
NAME READY STATUS RESTARTS AGE
- pod/istio-ingress-6f7c5dffd8-glszr 1/1 Running 0 4m28s
+ pod/istio-ingress-6f7c5dffd8-g1szr 1/1 Running 0 4m28s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/istio-ingress LoadBalancer 172.20.104.27 k8s-istioing-istioing-844c89b6c2-875b8c9a4b4e9365.elb.us-west-2.amazonaws.com 15021:32760/TCP,80:31496/TCP,443:32534/TCP 4m28s
@@ -271,25 +271,7 @@ kubectl port-forward svc/jaeger 16686:16686 -n istio-system
```text
* processing: helloworld.sample:5000/hello
- % Total % Received % Xferd Average Speed Time Time Time Current
- Dload Upload Total Spent Left Speed
- 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0* Trying 172.20.26.38:5000...
- * Connected to helloworld.sample (172.20.26.38) port 5000
- > GET /hello HTTP/1.1
- > Host: helloworld.sample:5000
- > User-Agent: curl/8.2.0
- > Accept: */*
- >
- < HTTP/1.1 200 OK
- < server: envoy
- < date: Fri, 21 Jul 2023 18:56:09 GMT
- < content-type: text/html; charset=utf-8
- < content-length: 58
- < x-envoy-upstream-service-time: 142
- <
- { [58 bytes data]
- 100 58 100 58 Hello version: v1, instance: helloworld-v1-b6c45f55-h592c
- 0 0 392 0 --:--:-- --:--:-- --:--:-- 394
+ ...
* Connection #0 to host helloworld.sample left intact
```
diff --git a/patterns/karpenter/example.yaml b/patterns/karpenter/example.yaml
index 25ee0fef3c..0ac0500df7 100644
--- a/patterns/karpenter/example.yaml
+++ b/patterns/karpenter/example.yaml
@@ -1,4 +1,3 @@
----
apiVersion: apps/v1
kind: Deployment
metadata:
diff --git a/patterns/karpenter/main.tf b/patterns/karpenter/main.tf
index 556f51267d..da71d9dd5b 100644
--- a/patterns/karpenter/main.tf
+++ b/patterns/karpenter/main.tf
@@ -136,13 +136,13 @@ module "eks_blueprints_addons" {
resources = {
limits = {
cpu = "0.25"
- # We are targetting the smallest Task size of 512Mb, so we subtract 256Mb from the
+ # We are targeting the smallest Task size of 512Mb, so we subtract 256Mb from the
# request/limit to ensure we can fit within that task
memory = "256M"
}
requests = {
cpu = "0.25"
- # We are targetting the smallest Task size of 512Mb, so we subtract 256Mb from the
+ # We are targeting the smallest Task size of 512Mb, so we subtract 256Mb from the
# request/limit to ensure we can fit within that task
memory = "256M"
}
diff --git a/patterns/kubecost/README.md b/patterns/kubecost/README.md
index d9601cb105..eca20a221a 100644
--- a/patterns/kubecost/README.md
+++ b/patterns/kubecost/README.md
@@ -1,6 +1,6 @@
# Kubecost with AWS Cloud Billing Integration
-This pattern demostrates how to install and configure Kubecost with AWS CUR report.
+This pattern demonstrates how to install and configure Kubecost with AWS CUR report.
The terraform code was created following the official Kubecost documentation for [aws cloud billing integration](https://docs.kubecost.com/install-and-configure/install/cloud-integration/aws-cloud-integrations).
## Prerequisites
@@ -22,7 +22,7 @@ Once all of the resources have successfully been provisioned, the following comm
aws eks --region update-kubeconfig --name
```
-This command will create a S3 bucket with prefix `kubecost-` and a Cost and Usage Report (CUR). Within 24h The CUR will generate a CloudFormation teamplate file called `crawler-cfn.yml` in the S3 bucket. Once that file is generated, navigate to:
+This command will create a S3 bucket with prefix `kubecost-` and a Cost and Usage Report (CUR). Within 24h The CUR will generate a CloudFormation template file called `crawler-cfn.yml` in the S3 bucket. Once that file is generated, navigate to:
```
cd run-me-in-24h/
@@ -45,7 +45,7 @@ Navigate to Settings -> Diagnostics -> View Full Diagnostics
Expected result:

-> [!NOTE]
+> [!NOTE]
> Spot Data Feed is included in Savings Plan, Reserved Instance, and Out-Of-Cluster.
## Destroy
diff --git a/patterns/multi-tenancy-with-teams/main.tf b/patterns/multi-tenancy-with-teams/main.tf
index 257bfe9f57..756ee028d3 100644
--- a/patterns/multi-tenancy-with-teams/main.tf
+++ b/patterns/multi-tenancy-with-teams/main.tf
@@ -174,7 +174,7 @@ module "eks_blueprints_dev_teams" {
}
################################################################################
-# Supporting Resoruces
+# Supporting Resources
################################################################################
module "vpc" {
diff --git a/patterns/privatelink-access/README.md b/patterns/privatelink-access/README.md
index 1124f2012d..81619eb6b8 100644
--- a/patterns/privatelink-access/README.md
+++ b/patterns/privatelink-access/README.md
@@ -90,7 +90,7 @@ kubectl get pods -A
NAMESPACE NAME READY STATUS RESTARTS AGE
kube-system aws-node-4f8g8 1/1 Running 0 1m
kube-system coredns-6ff9c46cd8-59sqp 1/1 Running 0 1m
-kube-system coredns-6ff9c46cd8-svnpb 1/1 Running 0 2m
+kube-system coredns-6ff9c46cd8-1npb 1/1 Running 0 2m
kube-system kube-proxy-mm2zc 1/1 Running 0 1m
```
diff --git a/patterns/sso-iam-identity-center/README.md b/patterns/sso-iam-identity-center/README.md
index 537980697a..377d7ecb1a 100644
--- a/patterns/sso-iam-identity-center/README.md
+++ b/patterns/sso-iam-identity-center/README.md
@@ -8,7 +8,7 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
## Validate
-After the `terraform` commands are executed sucessfully, check if the newly created users are active.
+After the `terraform` commands are executed successfully, check if the newly created users are active.
To do that use the link provided in the email invite - *if you added a valid email address for your users either in your Terraform code or IAM Identity Center Console* - or go to the [IAM Identity Center Console](https://console.aws.amazon.com/singlesignon/home/), in the *Users* dashboard on the left hand side menu, then select the user, and click on *Reset password* button on the upper right corner. Choose the option to *Generate a one-time password and share the password with the user*.
@@ -80,16 +80,16 @@ With the `kubeconfig` configured, you'll be able to run `kubectl` commands in yo
kubectl get pods -A
NAMESPACE NAME READY STATUS RESTARTS AGE
amazon-guardduty aws-guardduty-agent-bl2v2 1/1 Running 0 3h54m
-amazon-guardduty aws-guardduty-agent-sqvcx 1/1 Running 0 3h54m
+amazon-guardduty aws-guardduty-agent-s2vcx 1/1 Running 0 3h54m
amazon-guardduty aws-guardduty-agent-w8gfc 1/1 Running 0 3h54m
kube-system aws-node-m9hmd 1/1 Running 0 3h53m
kube-system aws-node-w42b8 1/1 Running 0 3h53m
kube-system aws-node-wm6rm 1/1 Running 0 3h53m
kube-system coredns-6ff9c46cd8-94jlr 1/1 Running 0 3h59m
-kube-system coredns-6ff9c46cd8-nwmrb 1/1 Running 0 3h59m
+kube-system coredns-6ff9c46cd8-n2mrb 1/1 Running 0 3h59m
kube-system kube-proxy-7fb86 1/1 Running 0 3h54m
kube-system kube-proxy-p4f5g 1/1 Running 0 3h54m
-kube-system kube-proxy-qkfmc 1/1 Running 0 3h54m
+kube-system kube-proxy-q1fmc 1/1 Running 0 3h54m
```
You can also use the `configure_kubectl` output to assume the *Cluster creator* role with `cluster-admin` access.
diff --git a/patterns/sso-iam-identity-center/main.tf b/patterns/sso-iam-identity-center/main.tf
index 187e01adbd..5c599f5cee 100644
--- a/patterns/sso-iam-identity-center/main.tf
+++ b/patterns/sso-iam-identity-center/main.tf
@@ -21,7 +21,6 @@ locals {
# Cluster
################################################################################
-#tfsec:ignore:aws-eks-enable-control-plane-logging
module "eks" {
source = "terraform-aws-modules/eks/aws"
version = "~> 19.21"
diff --git a/patterns/sso-okta/README.md b/patterns/sso-okta/README.md
index b25294bd94..480cf75395 100644
--- a/patterns/sso-okta/README.md
+++ b/patterns/sso-okta/README.md
@@ -8,7 +8,7 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
## Validate
-After the `terraform` commands are executed sucessfully, check if the newly created users are active.
+After the `terraform` commands are executed successfully, check if the newly created users are active.
To do that use the link provided in the email invite if you added a valid email address for your users, or go to the [Okta Admin Dashboard](https://dev-ORGID-admin.okta.com/admin/users/), select the user, and click on *Set Password and Activate* button.
@@ -34,16 +34,16 @@ The read-only user has a `cluster-viewer` Kubernetes role bound to it's group, w
kubectl get pods -A
NAMESPACE NAME READY STATUS RESTARTS AGE
amazon-guardduty aws-guardduty-agent-bl2v2 1/1 Running 0 3h54m
-amazon-guardduty aws-guardduty-agent-sqvcx 1/1 Running 0 3h54m
+amazon-guardduty aws-guardduty-agent-s1vcx 1/1 Running 0 3h54m
amazon-guardduty aws-guardduty-agent-w8gfc 1/1 Running 0 3h54m
kube-system aws-node-m9hmd 1/1 Running 0 3h53m
kube-system aws-node-w42b8 1/1 Running 0 3h53m
kube-system aws-node-wm6rm 1/1 Running 0 3h53m
kube-system coredns-6ff9c46cd8-94jlr 1/1 Running 0 3h59m
-kube-system coredns-6ff9c46cd8-nwmrb 1/1 Running 0 3h59m
+kube-system coredns-6ff9c46cd8-nw2rb 1/1 Running 0 3h59m
kube-system kube-proxy-7fb86 1/1 Running 0 3h54m
kube-system kube-proxy-p4f5g 1/1 Running 0 3h54m
-kube-system kube-proxy-qkfmc 1/1 Running 0 3h54m
+kube-system kube-proxy-qk2mc 1/1 Running 0 3h54m
```
You can also use the `configure_kubectl` output to assume the *Cluster creator* role with `cluster-admin` access.
@@ -52,7 +52,7 @@ You can also use the `configure_kubectl` output to assume the *Cluster creator*
configure_kubectl = "aws eks --region us-west-2 update-kubeconfig --name okta"
```
-It's also possible to preconfigure your `kubeconfig` using the `okta_login` output. This will also require you to authenticate in a browser window.
+It's also possible to pre-configure your `kubeconfig` using the `okta_login` output. This will also require you to authenticate in a browser window.
```
okta_login = "kubectl oidc-login setup --oidc-issuer-url=https://dev-ORGID.okta.com/oauth2/1234567890abcdefghij--oidc-client-id=1234567890abcdefghij"
diff --git a/patterns/sso-okta/main.tf b/patterns/sso-okta/main.tf
index 8d4ec7e5aa..2e666d48a5 100644
--- a/patterns/sso-okta/main.tf
+++ b/patterns/sso-okta/main.tf
@@ -21,7 +21,6 @@ locals {
# Cluster
################################################################################
-#tfsec:ignore:aws-eks-enable-control-plane-logging
module "eks" {
source = "terraform-aws-modules/eks/aws"
version = "~> 20.0"
diff --git a/patterns/stateful/README.md b/patterns/stateful/README.md
index dd7a20689a..4d75c2bc42 100644
--- a/patterns/stateful/README.md
+++ b/patterns/stateful/README.md
@@ -159,7 +159,7 @@ The following command will update the `kubeconfig` on your local machine and all
# Output should look similar to below
NAME PROVIDER BUCKET/PREFIX PHASE LAST VALIDATED ACCESS MODE DEFAULT
- default aws velero-ssqwm44hvofzb32d Available 2022-05-22 10:53:26 -0400 EDT ReadWrite true
+ default aws velero-ss1wm44hv1fzb32d Available 2022-05-22 10:53:26 -0400 EDT ReadWrite true
```
## Destroy
diff --git a/patterns/stateful/main.tf b/patterns/stateful/main.tf
index 79c16dfd31..807ee986be 100644
--- a/patterns/stateful/main.tf
+++ b/patterns/stateful/main.tf
@@ -105,7 +105,7 @@ module "eks" {
}
# This user data mounts the containerd directories to the second EBS volume which
- # is dedicated to just contianerd. You can read more about the practice and why
+ # is dedicated to just containerd. You can read more about the practice and why
# here https://aws.github.io/aws-eks-best-practices/scalability/docs/data-plane/#use-multiple-ebs-volumes-for-containers
# and https://github.com/containerd/containerd/blob/main/docs/ops.md#base-configuration
pre_bootstrap_user_data = <<-EOT
@@ -322,7 +322,6 @@ module "vpc" {
tags = local.tags
}
-#tfsec:ignore:*
module "velero_backup_s3_bucket" {
source = "terraform-aws-modules/s3-bucket/aws"
version = "~> 3.0"
@@ -377,7 +376,7 @@ module "efs" {
security_group_vpc_id = module.vpc.vpc_id
security_group_rules = {
vpc = {
- # relying on the defaults provdied for EFS/NFS (2049/TCP + ingress)
+ # relying on the defaults provided for EFS/NFS (2049/TCP + ingress)
description = "NFS ingress from VPC private subnets"
cidr_blocks = module.vpc.private_subnets_cidr_blocks
}
diff --git a/patterns/vpc-lattice/client-server-communication/README.md b/patterns/vpc-lattice/client-server-communication/README.md
index e79a725494..b058dcb287 100644
--- a/patterns/vpc-lattice/client-server-communication/README.md
+++ b/patterns/vpc-lattice/client-server-communication/README.md
@@ -4,7 +4,7 @@ This pattern demonstrates how to expose an EKS cluster hosted application to an
## Scenario
-With this soluton we showcase how to configure Amazon VPC Lattice using the AWS Gateway API Controller in order to manage Amazon VPC Lattice resources through native K8S Gateway API objects. This pattern deploys two distinct VPCs with a client application running in one of them and a server application in the other. The server application is deployed inside an EKS cluster and made exposed to the client application through Amazon VPC Lattice which establishes connectivity between the two applications. Further we demonstrate how to configure a custom domain name for the exposed service using Amazon Route53 and the external-dns project.
+With this solution we showcase how to configure Amazon VPC Lattice using the AWS Gateway API Controller in order to manage Amazon VPC Lattice resources through native K8S Gateway API objects. This pattern deploys two distinct VPCs with a client application running in one of them and a server application in the other. The server application is deployed inside an EKS cluster and made exposed to the client application through Amazon VPC Lattice which establishes connectivity between the two applications. Further we demonstrate how to configure a custom domain name for the exposed service using Amazon Route53 and the external-dns project.

@@ -15,11 +15,11 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
## Validate
-In order to test the connectivty between the client and server, please follow the steps outlined below:
+In order to test the connectivity between the client and server, please follow the steps outlined below:
1. Login to the management console of your AWS account and navigate to the EC2 service
2. Select your the EC2 Instance with the name **client**, click **Connect**, choose **Session Manager** and click **Connect**
-3. Within the console test the connecvity to the server application by entering the following command:
+3. Within the console test the connectivity to the server application by entering the following command:
```sh
$ curl -i http://server.example.com
diff --git a/patterns/vpc-lattice/client-server-communication/charts/demo-application/templates/deployment.yaml b/patterns/vpc-lattice/client-server-communication/charts/demo-application/templates/deployment.yaml
index 1b8e744907..0f1fabd93a 100644
--- a/patterns/vpc-lattice/client-server-communication/charts/demo-application/templates/deployment.yaml
+++ b/patterns/vpc-lattice/client-server-communication/charts/demo-application/templates/deployment.yaml
@@ -15,8 +15,8 @@ spec:
app: server
spec:
containers:
- - name: server
- image: public.ecr.aws/x2j8p8w7/http-server:latest
- env:
- - name: PodName
- value: "server pod"
+ - name: server
+ image: public.ecr.aws/x2j8p8w7/http-server:latest
+ env:
+ - name: PodName
+ value: "server pod"
diff --git a/patterns/wireguard-with-cilium/README.md b/patterns/wireguard-with-cilium/README.md
index 0cfbeacb88..c558968885 100644
--- a/patterns/wireguard-with-cilium/README.md
+++ b/patterns/wireguard-with-cilium/README.md
@@ -49,7 +49,7 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
CNI Chaining: aws-cni
Cilium: Ok 1.14.2 (v1.14.2-a6748946)
NodeMonitor: Listening for events on 2 CPUs with 64x4096 of shared memory
- Cilium health daemon: Ok
+ Cilium health daemon: Ok
IPAM: IPv4: 1/254 allocated from 10.0.0.0/24,
IPv4 BIG TCP: Disabled
IPv6 BIG TCP: Disabled
diff --git a/patterns/wireguard-with-cilium/example.yaml b/patterns/wireguard-with-cilium/example.yaml
index 77fb7c36b4..e9c4deea9d 100644
--- a/patterns/wireguard-with-cilium/example.yaml
+++ b/patterns/wireguard-with-cilium/example.yaml
@@ -11,12 +11,12 @@ spec:
- name: server
image: nginx
topologySpreadConstraints:
- - maxSkew: 1
- topologyKey: "kubernetes.io/hostname"
- whenUnsatisfiable: DoNotSchedule
- labelSelector:
- matchLabels:
- blog: wireguard
+ - maxSkew: 1
+ topologyKey: "kubernetes.io/hostname"
+ whenUnsatisfiable: DoNotSchedule
+ labelSelector:
+ matchLabels:
+ blog: wireguard
---
apiVersion: v1
kind: Service
@@ -26,7 +26,7 @@ spec:
selector:
name: server
ports:
- - port: 80
+ - port: 80
sessionAffinity: ClientIP
sessionAffinityConfig:
clientIP:
@@ -45,10 +45,10 @@ spec:
image: busybox
command: ["watch", "wget", "server"]
topologySpreadConstraints:
- - maxSkew: 1
- topologyKey: "kubernetes.io/hostname"
- whenUnsatisfiable: DoNotSchedule
- labelSelector:
- matchLabels:
- blog: wireguard
+ - maxSkew: 1
+ topologyKey: "kubernetes.io/hostname"
+ whenUnsatisfiable: DoNotSchedule
+ labelSelector:
+ matchLabels:
+ blog: wireguard
---
 @@ -97,7 +97,7 @@ echo "ArgoCD Password: $(kubectl --context hub get secrets argocd-initial-admin-
echo "ArgoCD URL: https://$(kubectl --context hub get svc -n argocd argo-cd-argocd-server -o jsonpath='{.status.loadBalancer.ingress[0].hostname}')"
```
-## Verify that ArgoCD Service Accouts has the annotation for IRSA
+## Verify that ArgoCD Service Accounts has the annotation for IRSA
```shell
kubectl --context hub get sa -n argocd argocd-application-controller -o json | jq '.metadata.annotations."eks.amazonaws.com/role-arn"'
@@ -220,7 +220,7 @@ cd ../hub
## Fork GitOps Repositories
-To modify the `values.yaml` file or the helm chart version for addons, you'll need to fork tthe repository [aws-samples/eks-blueprints-add-ons](https://github.com/aws-samples/eks-blueprints-add-ons).
+To modify the `values.yaml` file or the helm chart version for addons, you'll need to fork the repository [aws-samples/eks-blueprints-add-ons](https://github.com/aws-samples/eks-blueprints-add-ons).
After forking, update the following environment variables to point to your forks, replacing the default values.
diff --git a/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf b/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf
index 254499b4ec..536172751f 100644
--- a/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf
+++ b/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf
@@ -223,7 +223,7 @@ module "eks_blueprints_addons" {
################################################################################
# EKS Cluster
################################################################################
-#tfsec:ignore:aws-eks-enable-control-plane-logging
+
module "eks" {
source = "terraform-aws-modules/eks/aws"
version = "~> 19.13"
diff --git a/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf b/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf
index 617769acb7..1946f47ff3 100644
--- a/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf
+++ b/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf
@@ -240,7 +240,7 @@ module "eks_blueprints_addons" {
################################################################################
# EKS Cluster
################################################################################
-#tfsec:ignore:aws-eks-enable-control-plane-logging
+
module "eks" {
source = "terraform-aws-modules/eks/aws"
version = "~> 19.13"
diff --git a/patterns/ipv6-eks-cluster/README.md b/patterns/ipv6-eks-cluster/README.md
index 370caa80c9..67897786f7 100644
--- a/patterns/ipv6-eks-cluster/README.md
+++ b/patterns/ipv6-eks-cluster/README.md
@@ -17,12 +17,12 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
```text
# Output should look like below
NAMESPACE NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
- kube-system aws-node-bhd2s 1/1 Running 0 3m5s 2600:1f13:6c4:a703:ecf8:3ac1:76b0:9303 ip-10-0-10-183.us-west-2.compute.internal
@@ -97,7 +97,7 @@ echo "ArgoCD Password: $(kubectl --context hub get secrets argocd-initial-admin-
echo "ArgoCD URL: https://$(kubectl --context hub get svc -n argocd argo-cd-argocd-server -o jsonpath='{.status.loadBalancer.ingress[0].hostname}')"
```
-## Verify that ArgoCD Service Accouts has the annotation for IRSA
+## Verify that ArgoCD Service Accounts has the annotation for IRSA
```shell
kubectl --context hub get sa -n argocd argocd-application-controller -o json | jq '.metadata.annotations."eks.amazonaws.com/role-arn"'
@@ -220,7 +220,7 @@ cd ../hub
## Fork GitOps Repositories
-To modify the `values.yaml` file or the helm chart version for addons, you'll need to fork tthe repository [aws-samples/eks-blueprints-add-ons](https://github.com/aws-samples/eks-blueprints-add-ons).
+To modify the `values.yaml` file or the helm chart version for addons, you'll need to fork the repository [aws-samples/eks-blueprints-add-ons](https://github.com/aws-samples/eks-blueprints-add-ons).
After forking, update the following environment variables to point to your forks, replacing the default values.
diff --git a/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf b/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf
index 254499b4ec..536172751f 100644
--- a/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf
+++ b/patterns/gitops/multi-cluster-hub-spoke-argocd/hub/main.tf
@@ -223,7 +223,7 @@ module "eks_blueprints_addons" {
################################################################################
# EKS Cluster
################################################################################
-#tfsec:ignore:aws-eks-enable-control-plane-logging
+
module "eks" {
source = "terraform-aws-modules/eks/aws"
version = "~> 19.13"
diff --git a/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf b/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf
index 617769acb7..1946f47ff3 100644
--- a/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf
+++ b/patterns/gitops/multi-cluster-hub-spoke-argocd/spokes/main.tf
@@ -240,7 +240,7 @@ module "eks_blueprints_addons" {
################################################################################
# EKS Cluster
################################################################################
-#tfsec:ignore:aws-eks-enable-control-plane-logging
+
module "eks" {
source = "terraform-aws-modules/eks/aws"
version = "~> 19.13"
diff --git a/patterns/ipv6-eks-cluster/README.md b/patterns/ipv6-eks-cluster/README.md
index 370caa80c9..67897786f7 100644
--- a/patterns/ipv6-eks-cluster/README.md
+++ b/patterns/ipv6-eks-cluster/README.md
@@ -17,12 +17,12 @@ See [here](https://aws-ia.github.io/terraform-aws-eks-blueprints/getting-started
```text
# Output should look like below
NAMESPACE NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
- kube-system aws-node-bhd2s 1/1 Running 0 3m5s 2600:1f13:6c4:a703:ecf8:3ac1:76b0:9303 ip-10-0-10-183.us-west-2.compute.internal