-
Notifications
You must be signed in to change notification settings - Fork 336
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Jira Server: Jira Server OAuth1 flow #5817
Comments
|
@Dschoordsch any ideas how this mutation parameters would look like? It'd be great to be able to just use the one we're adding in #5805 I'm happy to sync on that if needed |
|
@BartoszJarocki I thought #5805 is about adding integration providers, #5809 is capturing that bit of work for JiraServer. |
|
Oh perfect. So this one is actually authenticating users with Jira Server, I assume. If yes, maybe we can make it work with |
|
I don't think that's beneficial since OAuth1.0a and OAuth2 are different enough to have 2 separate mutations (rather than a if/else in one mutation). We could name it more generically, but that's not important because we will probably never add another OAuth1.0a integration. |
addJiraServerAuth mutation and UIaddJiraServerAuth mutation and UI
|
@Dschoordsch you should be able to use the To make this implementation clean, all I'd suggest doing would be to add an Doing this should be less work—or at least equivalent work—than needing to implement your own mutation. At the least, we should walk through it, to see if anything in our new generic authentication architecture should change... |
|
@jordanh you're right. With the current implementation in #5805 it would be adding another if to store the correct provider metadata.
We need to have an additional query for OAuth1 though since it requires a request token for the client flow. |
addJiraServerAuth mutation and UI|
@Dschoordsch - when extending the graphql schema to support Jira, I see AtlassianIntegration and associated types created in the schema.graphql file on the backend. Are you manually updating these types on both server and client? There appears to be some graphql types that you are getting directly from GitHub and GitLab. I am looking to extend the schema to support ADO, and wanted to make sure I was working within whatever process you are using right now. I was planning on
|
|
@bobjac You shouldn't need to modify any
|
|
@Dschoordsch Perfect. I saw all the types programmatically created, which is what I was sure to do, but got confused when I saw Atlassian types in schema.graphql. I didn't think Atlassian supported graphql natively, so I didn't think that was a pulled type from them. Thanks. |
|
@Dschoordsch - Azure Active Directory / Azure DevOps, requires the PKCE flow for Oauth. This requires rolling your own pkce key and making an additional API call to get the auth token. I reviewed the code for the GitHub and Atlassian Managers that handle the authorization popups, and the code for the AzureDevOps Manager would need to include the PKCE flow implementation. Typically, we would recommend using msal (https://github.com/AzureAD/microsoft-authentication-library-for-js) for this. Are you OK with using this library? It would mean that Parabol would take an additional npm package as a dependency, but you wouldn't have to own and maintain identity protocol implementation in your AzureDevOpsManager implementation. |
|
@bobjac I'm not opposed against adding the library for the server since it's actively maintained and has no additional dependencies. For the client side I don't see a big benefit since it would increase client size and I would be afraid integrating it would be more effort than following existing patterns. Correct me if I'm wrong. Adding PKCE to the OAuth flow client side shouldn't be much work. If I understand it correctly, adding it to Atlassian as an example, we would generate a
and then pass it along with the code here
In addition the parameter needs to be passed on from the OAuth callback
|
Needs #5809
We could start making
add...Authmutations generic based on the type of service provider. Jira Server is the only one with OAuth1.0a, thus it would be different from existing ones in any case. Thus we're adding it as a separate mutation.Integration row must be added when org/team has provider set up

OAuth1 has an additional first step to get a request token which then can be used for the OAuth flow on the client
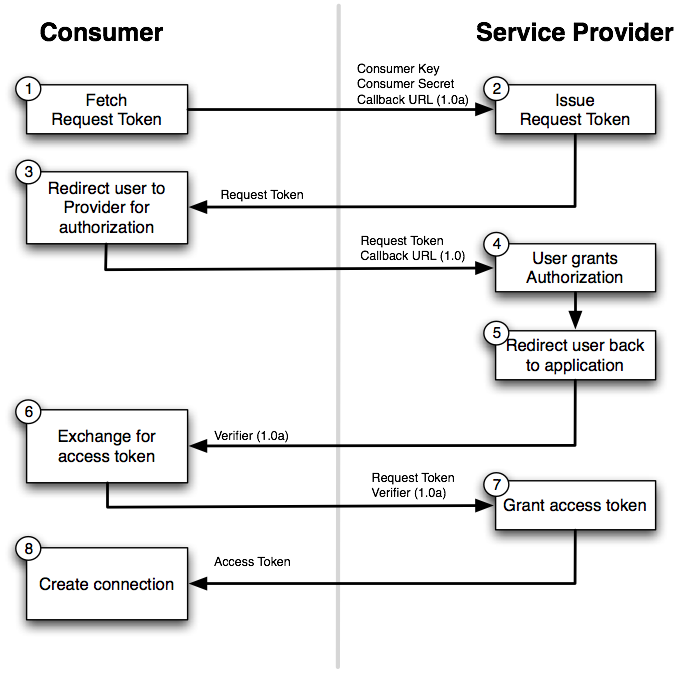
Flow
getOAuth1RequestTokenis called to get the authentication URLaddIntegrationTokenis called with the access tokenhttps://datatracker.ietf.org/doc/html/rfc5849
Acceptance criteria
getOAuth1RequestTokenaddIntegrationTokento support OAuth1 tokengetandpostmethods implemented including signatures from OAuth1getRequestTokenmethod#5818 contains UI draft and asset
The text was updated successfully, but these errors were encountered: